
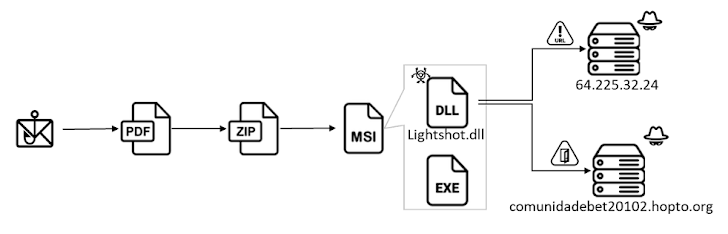
Users in Brazil are the target of a new banking trojan known as CHAVECLOAK which is propagated via phishing emails with PDF attachments.
“This intricate attack involves PDF downloading a ZIP file and then using DLL side-loading techniques to execute the final malware,” said Cara Lin, a researcher at Fortinet FortiGuard Labs.
The attack chain involves using contract-themed DocuSign lures to trick users into opening PDF files containing a button to read and sign documents.
Actually, clicking the button results in the retrieval of an installation file from a remote link which is shortened using the Goo.su URL shortening service.
Inside the installer is an executable called “Lightshot.exe” that takes advantage of DLL side loading to load “Lightshot.dll”, which is CHAVECLOAK malware that facilitates the theft of sensitive information.
This includes collecting system metadata and performing checks to determine whether the compromised machine is located in Brazil, and if so, periodically monitoring the foreground window to compare it to a predefined list of bank-related strings.

If it matches, a connection is established with a command and control (C2) server and proceeds to collect various types of information and exfiltrate it to distinct endpoints on the server depending on the financial institution.
“The malware facilitates various actions to steal the victim’s credentials, such as allowing the operator to lock the victim’s screen, log keystrokes, and display deceptive pop-up windows,” Lin said.
“The malware actively monitors the victim’s access to specific financial portals, including several banks and Mercado Bitcoin, which includes both traditional banking platforms and cryptocurrency platforms.”
Fortinet said it also discovered a Delphi variant of CHAVECLOAK, once again highlighting the prevalence of Delphi-based malware targeting Latin America.
“The emergence of the CHAVECLOAK banking Trojan highlights the evolving landscape of cyber threats targeting the financial sector, particularly focusing on users in Brazil,” concluded Lin.
The findings come from an ongoing mobile banking fraud campaign against the United Kingdom, Spain and Italy that involves the use of smishing and vishing tactics (i.e. SMS and voice phishing) to distribute Android malware called Copybara with the aim of executing unauthorized bank transfers to a network of bank accounts operated by money mules.
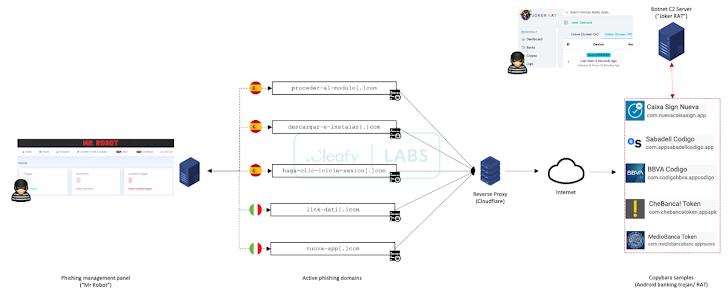
“They [Threat actors] were caught using a structured way of managing all ongoing phishing campaigns via a centralized web panel known as ‘Mr. Robot,'” Cleafy said in a report published last week.
“With this panel, TAs can enable and manage multiple phishing campaigns (against different financial institutions) based on their needs.”
The C2 framework also allows attackers to orchestrate tailored attacks against distinct financial institutions using phishing kits designed to mimic the user interface of the targeted entity, while also employing anti-detection methods via geofencing and device fingerprinting to limit the connections only from mobile devices.
The phishing kit – which acts as a fake login page – is responsible for capturing the credentials and phone numbers of retail banking customers and sending the details to a Telegram group.
Part of the malicious infrastructure used for the campaign is designed to deliver Copybara, which is operated using a C2 panel called JOKER RAT that shows all infected devices and their geographic distribution on a live map.
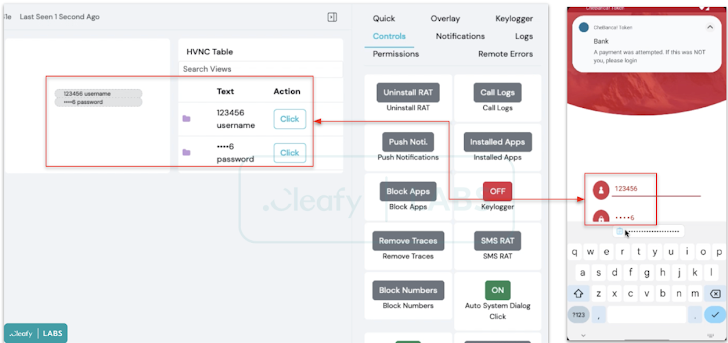
It also allows threat actors to remotely interact in real-time with an infected device using a VNC module, as well as inject fake overlays onto banking apps to steal credentials, log keystrokes by abusing Android Accessibility Services, and intercept SMS messages .

Besides that, JOKER RAT comes with an APK builder that allows you to customize the rogue app name, package name, and icons.
“Another feature available within the panel is the ‘Push Notification’, probably used to send fake push notifications that appear to be bank notifications to infected devices to entice the user to open the bank app so that the malware can steal credentials,” said Cleafy researchers Francesco Iubatti and Federico Valentini.
The growing sophistication of on-device fraud (ODF) schemes is further highlighted by a recently disclosed TeaBot (aka Anatsa) campaign that managed to infiltrate the Google Play Store under the guise of PDF reading apps.
“This application acts as a dropper and facilitates the download of a TeaBot family banking trojan through multiple stages,” Iubatti said. “Before downloading the banking Trojan, the dropper performs advanced evasion techniques, including obfuscation and file deletion, as well as multiple checks on the victim countries.”