
The menacing Russian-linked actor known as APT28 has been linked to numerous ongoing phishing campaigns using decoy documents imitating government and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America.
“Discovered decoys include a mix of internal and publicly available documents, as well as possible documents generated by actors associated with finance, critical infrastructure, executive positions, cybersecurity, maritime security, healthcare, business, and defense industrial manufacturing,” IBM Force said in a report published last week.
The tech company is tracking activity under the moniker ITG05, also known as Blue Athena, BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, TA422, and UAC -028.

The revelation comes more than three months after the adversary was spotted using decoys related to the ongoing war between Israel and Hamas to deliver a custom backdoor dubbed HeadLace.
APT28 has since also targeted Ukrainian government bodies and Polish organizations with phishing messages designed to deploy tailor-made implants and information thieves such as MASEPIE, OCEANMAP and STEELHOOK.
Other campaigns have involved exploiting security flaws in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) to raid NT LAN Manager (NTLM) v2 hashes, increasing the possibility that the threat actor could exploit other weaknesses to exfiltrate NTLMv2 hashes for use in relay attacks.
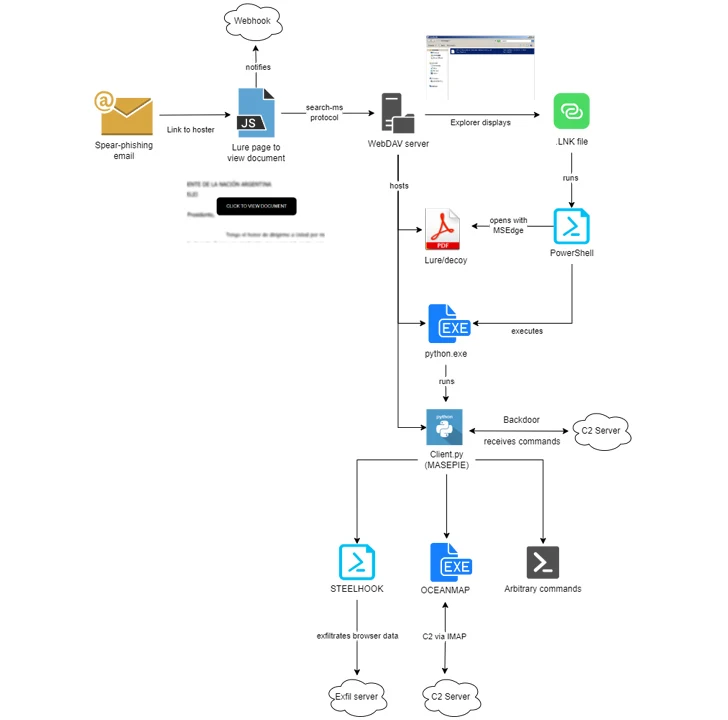
The latest campaigns observed by IBM
There is evidence to suggest that both WebDAV servers and MASEPIE C2 servers may be hosted on compromised Ubiquiti routers, a botnet that was blocked by the US government last month.

Phishing attacks impersonate entities from several countries such as Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States, using a mix of publicly available authentic government and non-government documents to activate the infection. Chains.
“In an update to their methodologies, ITG05 uses the freely available hosting provider, firstcloudit[.]com to organize payloads to enable ongoing operations,” said security researchers Joe Fasulo, Claire Zaboeva and Golo Mühr.
The culmination of APT28’s elaborate scheme ends with the execution of MASEPIE, OCEANMAP, and STEELHOOK, designed to exfiltrate files, execute arbitrary commands, and steal browser data. OCEANMAP has been characterized as a more powerful version of CredeMap, another backdoor previously identified as being used by the group.
“ITG05 remains adaptable to changing opportunities by providing new infection methodologies and leveraging commercially available infrastructures, constantly evolving the malware’s capabilities,” the researchers concluded.