COMMENT
Since the discovery of the Mirai botnet in 2016, governments, businesses and consumers have noticed the impact of insecure Internet of Things (IoT) devices.
It has become commonplace that numerous Internet-connected consumer devices, such as smart home security cameras and home routers, are used with unchanged default usernames and passwords, allowing attackers to take control of them and turn them into a network of “zombie” devices . Together, they create a botnet of compromised devices, used in large-scale network attacks, affecting the availability of many websites, Internet-based services, and network availability.
While it may seem like common sense to avoid using default usernames and passwords, many IoT devices lack adequate security protection, even at the most basic level. Since Mirai, a significant amount of work has been done by standards bodies, industry groups and governments to ensure that new IoT devices coming to market have a foundation of security by design.
However, insecure IoT can also impact the individual consumer. It is not clear to consumers whether their devices are safe, have been protected, or will be protected. Certification, verification, standards and regulation aim to make devices safer and enable consumers to make informed purchasing decisions.
In an effort to change that, on March 19, the Connectivity Standards Alliance Product Security Working Group (PSWG) released Specification 1.0 for Internet of Things Device Security, as well as an accompanying certification program and verified mark for security of products for compliant products.
The work aims to establish a unified IoT device security standard, alleviating the challenge for manufacturers to certify their devices and comply with international requirements, as well as inform consumers about devices that meet this set of security requirements. The Connectivity Standards Alliance (CSA) took into account existing requirements from international standards, including the European Telecommunications Standards Institute (ETSI) and the National Institute of Standards and Technology (NIST), as well as current regulations, when creating the specifications.
Safe based on the design baseline
Security by design requires device manufacturers to consider and implement security early in device design and manufacturing, rather than as an afterthought. Three existing key standards have defined the basic safety requirements:
-
ETSI EN 303 645, “Cybersecurity for Consumer Internet of Things: Baseline Requirements” — ETSI is based in Europe, but is widely used in all geographic areas.
-
NIST IR 8425, “Profile of the IoT Core Baseline for Consumer IoT Products” – Published as part of the National Institute of Standards and Technology’s response to White House Executive Order 14028.
-
ISO/IEC 27402:2023 — Most recently published by the international non-governmental organization, titled “Cybersecurity — IoT security and privacy — Basic device requirements.”
Governments have adopted these standards to varying degrees in their guidelines and legislation (planned or implemented). For the most part, across all regions, the three requirements of no default passwords, transparency about security updates, and clear disclosure of vulnerabilities constitute the minimum baseline.
While this acceleration and focus on device security is positive, a number of challenges remain in resolving the issue:
-
While some government requirements overlap, there is no unified regulation – the picture is fragmented.
-
Likewise, multiple standards exist, with no clear path for manufacturers to follow if they sell in multiple markets.
-
Most industry guidelines are voluntary, with only the UK and Singapore governments having mandatory requirements, some yet to be enforced.
Additionally, consumers are turning to manufacturers for information on the security of their devices. Omdia’s survey asked, “How do you know how secure your devices are?” and the most commonly cited source (68%) was manufacturer information.
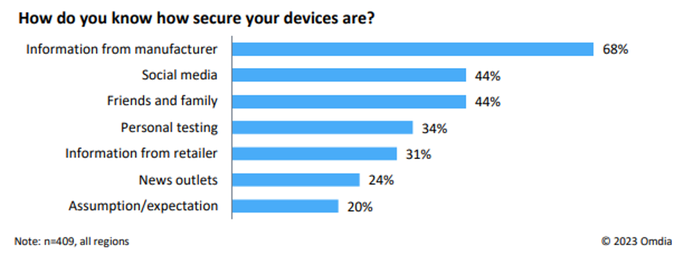
Source: Omdia, Consumer IoT Device Cybersecurity Standards, Policies, and Certification Schemes, sponsored by Connectivity Standards Alliance
Currently, without mandatory requirements or widespread use of independently verified testing and safety requirements, there is no clear way for consumers to access this information from manufacturers or verify its accuracy.
The CSA intends to change that with its new standard. In particular, it recognizes the work already done and the standards previously established: the effort has combined the requirements of the above safety baselines, as well as Singapore and European guidelines, into a single specification and certification program.
IoT Device Security Specification 1.0 requirements
Manufacturers of IoT devices (including light bulbs, switches, smart doorbells, thermostats, and more) that choose to adhere to the specifications must meet a number of device security provisions. They must demonstrate compliance with these by providing justification and evidence to an authorized testing laboratory that has crucial expertise and experience in safety assessment and certification.
Some key requirements in the specification include:
-
Securely store sensitive data on your device
-
Secure communications of safety-relevant information
-
Secure software updates throughout the support period
-
Secure development and vulnerability management
-
Public documentation regarding security and support period
Transparency for consumers
In addition to requirements involving transparency, such as public documentation of support periods, the specification is accompanied by the product safety verification mark. This product marking provides confirmation to buyers that a product has met specification safety requirements and helps them make informed purchasing decisions. More information will be accessible to consumers, via one or a combination of a printed URL, hyperlink or QR code.
Omdia Analysis: Efforts from across the industry will be key to adoption
Since this is a voluntary program, there is, of course, the question of how adoption will develop. Looking at government guidance, many published requirements and voluntary frameworks have not had the desired adoption, resulting in laws and regulations being passed and planned in many regions.
That said, the CSA project aims to address many of the issues related to fragmentation, making things easier and relieving pressure on producers as this regulation comes into force. Furthermore, existing schemes have been recognised: for example, the Singapore Label and the CSA Mark will be mutually recognised, meaning that certification activities for producers can be significantly more cost-effective.
Looking at device manufacturers and the industry, manufacturers must understand the value of implementing secure by design requirements and certifications. Not only does certification help anticipate and relieve the pressure of upcoming mandatory requirements, but consumers are more likely to purchase secure devices.
Omdia’s survey of 400 consumers suggests that nearly all consumers are more likely to purchase a device with privacy and security labeling, with the majority (81%) preferring a referral URL or QR code to provide more information about privacy and security.
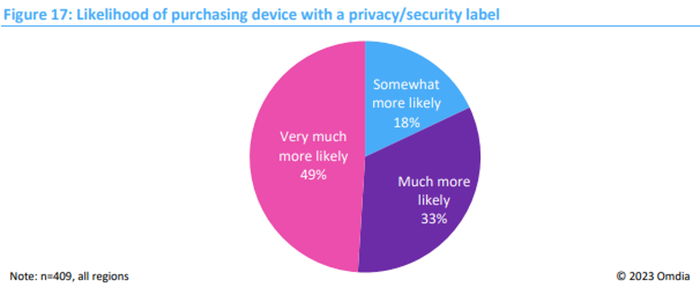
Source: Omdia, Consumer IoT Device Cybersecurity Standards, Policies, and Certification Schemes, sponsored by Connectivity Standards Alliance
The Connectivity Standards Alliance has nearly 200 member companies that collaborated on the development and validation of the final specification. This includes large industry players such as Amazon, Arm, Comcast, Google, Infineon, NXP, Schneider Electric, Signify, and Silicon Labs. The industry will have a vital role to play in promoting product safety and the support from member companies augurs well for the adoption of the CSA program.
It is crucial that botnets like Mirai have not disappeared. Even today, there are variants and devices sold that still do not have adequate protection. Efforts to improve IoT security remain a top priority for the cybersecurity industry, and efforts like the CSA standard and certification serve as critical baselines to support those efforts.
Read ” by Omdia “Standards, policies and certification schemes for cybersecurity of consumer IoT devices” relationship.