
Threat hunters have identified a suspicious package in the NuGet package manager, likely designed to target developers working with tools made by a Chinese company specializing in manufacturing industrial and digital equipment.
The package in question is SqzrFramework480which according to ReversingLabs was first published on January 24, 2024. It has been downloaded 2,999 times at the time of writing.
The software supply chain security firm said it had not found any other packages exhibiting similar behavior.
However, he theorized that the campaign could likely be used to orchestrate industrial espionage on systems equipped with cameras, computer vision and robotic arms.

The indication that SqzrFramework480 is apparently linked to a Chinese company called Bozhon Precision Industry Technology Co., Ltd. comes from the use of a version of the company’s logo for the package icon. It was uploaded by a Nuget user account called “zhaoyushun1999”.
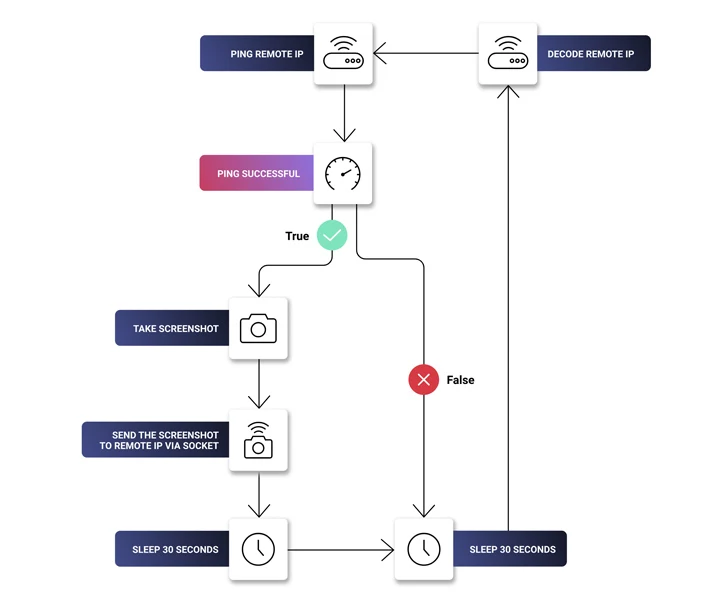
Inside the library there is a DLL file “SqzrFramework480.dll” that comes with functionality to take screenshots, ping a remote IP address every 30 seconds until the operation is complete, and transmit the screenshots over a created socket and connected to said IP address.
“None of these behaviors are absolutely malicious. However, when taken together, they raise alarms,” security researcher Petar Kirhmajer said. “The ping serves as a heart rate check to see if the exfiltration server is active.”
Malicious use of sockets for communication and data exfiltration has been observed before, such as in the case of the nodejs_net_server npm package.
The exact motive behind the package is still unclear, although it is well known that adversaries consistently resort to hiding nefarious code in seemingly innocuous software to compromise victims.

An alternative, harmless explanation could be that the package was leaked by a developer or third party working with the company.
“They could also explain a seemingly malicious behavior of continuous screen capture: It could simply be a way for a developer to transmit images from the camera on the main monitor to a workstation,” Kirhmajer said.
Aside from the ambiguity surrounding the package, the findings highlight the complicated nature of supply chain threats, making it imperative that users carefully review libraries before downloading them.
“Open source repositories like NuGet increasingly host suspicious and malicious packages designed to lure developers into downloading and embedding malicious libraries and other modules into their development pipelines,” Kirhmajer said.