
Over the past three months, two China-linked Advanced Persistent Threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign .
This includes the actor known as Mustang Panda, who has recently been linked to cyberattacks against Myanmar and other Asian countries with a variant of the PlugX (aka Korplug) backdoor called DOPLUGS.
Mustang Panda, also called Camaro Dragon, Earth Preta and Stately Taurus, is believed to have targeted entities in Myanmar, the Philippines, Japan and Singapore, targeting them with phishing emails designed to deliver two malware packages.
“Threat actors created malware for these packages on March 4-5, 2024, coinciding with the ASEAN-Australia Special Summit (March 4-6, 2024),” Palo Alto Networks Unit 42 said in a report shared with The Hacker News.
One of the malware packages is a ZIP file that contains an executable (“Talking_Points_for_China.exe”), which once started loads a DLL file (“KeyScramblerIE.dll”) and finally distributes a well-known Mustang Panda malware called PUBLOAD, a downloader previously used to delete PlugX.
It is worth pointing out here that the binary file is a renamed copy of a legitimate software called KeyScrambler.exe which is susceptible to DLL side loading.
The second package, however, is a screensaver executable (“Note PSO.scr”) used to retrieve next-stage malicious code from a remote IP address, including a benign program signed by a video game company renamed WindowsUpdate. exe and a rogue DLL launched using the same technique as before.

“This malware then attempts to establish a connection to www[.]openservername[.]com at 146.70.149[.]36 for command and control (C2),” the researchers said.
Unit 42 said it also detected network traffic between an ASEAN-affiliated entity and the C2 infrastructure of a second Chinese APT group, suggesting a breach of the victim’s environment. This cluster of unnamed threat activity has been attributed to similar attacks against Cambodia.
“These types of campaigns continue to demonstrate how organizations are targeted for cyber espionage purposes, where threat groups affiliated with nation states gather intelligence on geopolitical interests within the region,” the researchers said.
The Earth Krahang emerges in the wild
The findings come a week after Trend Micro shed light on a new Chinese threat actor known as Earth Krahang that has targeted 116 entities in 35 countries by exploiting spear-phishing and flaws in public-facing Openfire and Oracle servers to deliver malware tailor-made ones like PlugX, ShadowPad, ReShell, and DinodasRAT (also known as XDealer).
The first attacks date back to early 2022, when the adversary leveraged a combination of methods to scan sensitive data.
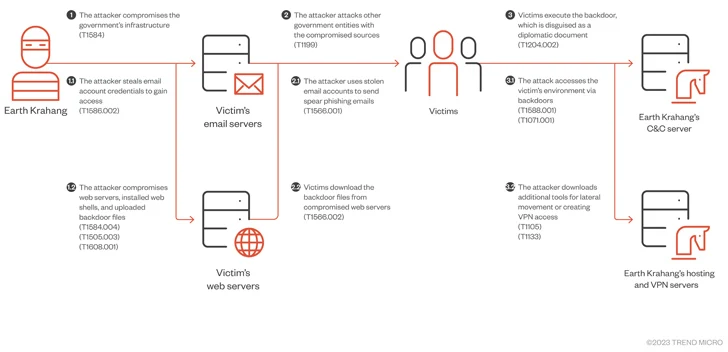
Earth Krahang, which has a strong focus in Southeast Asia, also shows some level of overlap with another monitored China-linked threat actor such as Earth Lusca (also known as RedHotel). Both sets of intrusions are likely operated by the same threat actor and linked to a Chinese government contractor called I-Soon.
“A favorite tactic of threat actors involves using malicious access to government infrastructure to attack other government entities, abusing the infrastructure to host malicious payloads, proxy attacks on traffic, and sending spear-phishing emails to targets linked to the government using compromised government email accounts,” the company explained.
“Earth Krahang also uses other tactics, such as building VPN servers on compromised public servers to establish access to victims’ private network and perform brute force attacks to obtain email credentials. These credentials are then used to exfiltrate emails of the victims.”
The I-Soon leaks and the dark rental-for-hire scene
Last month, a series of leaked documents from I-Soon (aka Anxun) on GitHub revealed how the company sells a wide range of remote access thieves and Trojans such as ShadowPad and Winnti (aka TreadStone) to several Chinese government entities. This also includes an integrated operational platform designed to carry out offensive cyber campaigns and an undocumented Linux implant codenamed Hector.
“The integrated operating platform includes both internal and external applications and networks,” Bishop Fox said. “The internal application is primarily for mission and resource management. The external application is designed to perform cyber operations.”
The shadowy hack-for-hire entity was also implicated in the 2019 POISON CARP campaign targeting Tibetan groups and the 2022 Comm100 hack, in addition to attacks against foreign governments and domestic ethnic minorities to obtain valuable intelligence, some of which are transported out independently in the hope of acquiring a government customer.
“The data leak provided a rare insight into how the Chinese government outsources part of its cyber operations to private third-party companies and how these companies collaborate with each other to meet these requests,” ReliaQuest noted.

Cybersecurity firm Recorded Future, in its analysis, said that the leak exposes “operational and organizational ties” between the company and three different state-sponsored Chinese cyber groups such as RedAlpha (aka Deepcliff), RedHotel and POISON CARP.
“It provides evidence to support the long-suspected presence of ‘digital quartermasters’ providing capabilities to multiple Chinese state-sponsored groups.”
He also said the overlaps suggest the presence of multiple sub-teams focused on particular missions within the same company. I-Soon’s victimization footprint extends to at least 22 countries, with government, telecommunications and education representing the most targeted sectors.
Furthermore, the publicized documents confirm that the Tianfu Cup – China’s version of the Pwn2Own hacking competition – acts as a “vulnerability feeding system” for the government, allowing it to stockpile zero-day exploits and devise exploit code.
“When Tianfu Cup proposals are not already complete exploit chains, the Ministry of Public Security spreads proof-of-concept vulnerabilities to private companies to further exploit these proof-of-concept capabilities,” Margin Research said.
“China’s obligation to disclose vulnerabilities is one part of the puzzle of how China accumulates and uses vulnerabilities as weapons, setting in stone the clandestine collection afforded by the Tianfu Cup in previous years.”
The source of the leak is not known at this time, although two I-Soon employees told The Associated Press that an investigation is underway in cooperation with law enforcement. The company’s website has since gone offline.
“The leak provides some of the most concrete details seen publicly to date, revealing the maturing nature of China’s cyber espionage ecosystem,” said SentinelOne’s Dakota Cary and Aleksandar Milenkoski. “It explicitly shows how government targeting requirements drive a competitive market for paid freelance hackers.”