
A new phishing campaign has been observed that leverages a new loader malware to deliver an information stealer and keylogger called Agent Tesla.
Trustwave SpiderLabs said it identified a phishing email carrying this attack chain on March 8, 2024. The message masquerades as a bank payment notification, inviting the user to open an attached archive file.
The archive (“Bank Handlowy w Warszawie – dowód wpłaty_pdf.tar.gz”) hides a malicious loader that triggers the procedure to deploy Agent Tesla on the compromised host.
“This loader then used obfuscation to evade detection and exploited polymorphic behavior with complex decryption methods,” security researcher Bernard Bautista said in an analysis on Tuesday.
“The loader also demonstrated the ability to bypass antivirus defenses and retrieve its payload using specific URLs and user agents that leverage proxies to further obfuscate traffic.”
The tactic of embedding malware within seemingly harmless files has been repeatedly employed by threat actors to trick unsuspecting victims into activating the infection sequence.

The loader used in the attack is written in .NET, with Trustwave discovering two distinct variants that each use a different decryption routine to access its configuration and ultimately retrieve the XOR-encoded Agent Tesla payload from a remote server.
In an attempt to evade detection, the loader is also designed to bypass the Windows Anti-Malware Scanning Interface (AMSI), which provides the ability for security software to scan files, memory, and other data for threats.
It achieves this by “patching the AmsiScanBuffer function to evade malware scanning of in-memory contents,” Bautista explained.
The final stage involves decoding and executing Agent Tesla in memory, allowing threat actors to stealthily exfiltrate sensitive data via SMTP using a compromised email account associated with a legitimate security vendor in Turkey (” merve@temikan[.]com[.]tr”).
The approach, Trustwave said, not only raises no red flags, but also offers a layer of anonymity that makes it harder to trace the attack back to the adversary, not to mention the effort of having to set up dedicated exfiltration channels .
“[The loader] uses methods such as patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, ensuring stealth execution and minimizing traces on disk,” Bautista said. “This loader marks a notable evolution in Agent Tesla deployment tactics.”
The disclosure comes as BlueVoyant uncovered another phishing activity conducted by a cybercrime group called TA544 that exploits PDFs masquerading as legal invoices to propagate WikiLoader (aka WailingCrab) and establish connections with command and control (C2) servers that include almost exclusively WordPress hacked. sites.
It is worth noting that TA544 armed a Windows security bypass flaw tracked as CVE-2023-36025 in November 2023 to distribute Remcos RAT via a different loader family called IDAT Loader, allowing it to take control of infected systems.
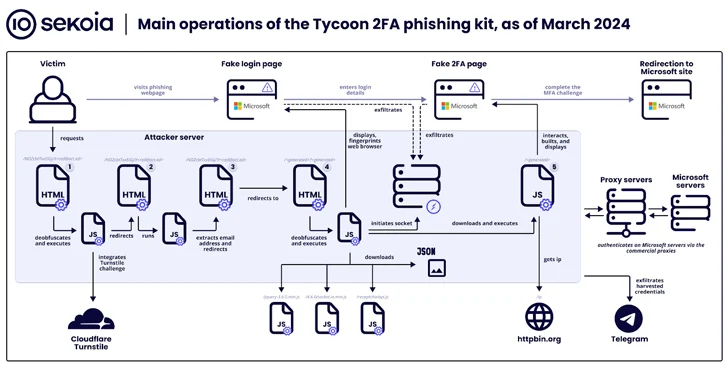
The findings also follow an increase in the use of a phishing kit called Tycoon, which Sekoia said has “become one of the most widespread [adversary-in-the-middle] phishing kits in recent months, with over 1,100 domain names detected between the end of October 2023 and the end of February 2024.”

Tycoon, publicly documented by Trustwave last month, allows cybercriminals to target Microsoft 365 users with fake login pages to capture their credentials, session cookies, and two-factor authentication (2FA) codes. It is known to have been active since at least August 2023, with the service offered via private Telegram channels.
The phishing kit is known to incorporate extensive traffic filtering methods to thwart bot activity and analysis attempts, requiring site visitors to complete a Cloudflare Turnstile challenge before redirecting users to a credential collection page.
Tycoon also shares operational and design similarities with the OTT phishing kit Dadsec, raising the possibility that developers may have accessed and modified the latter’s source code to suit their needs. This is supported by the fact that the source code of Dadsec OTT was leaked in October 2023.
“The developer has improved the stealth capabilities in the latest version of the phishing kit,” Sekoia said. “Recent updates may reduce the rate of detection of Tycoon’s 2FA phishing pages and infrastructure by security products. Additionally, its ease of use and relatively low price make it very popular among scammers. threats.”