
Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they are not the same thing. The main difference between attack surface management and vulnerability management lies in their scope: vulnerability management checks a list of known resources, while attack surface management assumes the presence of unknown resources and therefore starts with discovery . Let’s look at both in more detail.
What is vulnerability management?
Vulnerability management is, at the simplest level, the use of automated tools to identify, prioritize and report security issues and vulnerabilities in your digital infrastructure.
Vulnerability management uses automated scanners to run regular, scheduled scans on assets within a known IP range to detect established and new vulnerabilities, so you can apply patches, remove vulnerabilities, or mitigate any potential risks. These vulnerabilities tend to use a risk score or scale – such as CVSS – and risk calculations.
Vulnerability scanners often have many thousands of automated checks at their disposal, and by analyzing and gathering information about your systems, they can identify security gaps that could be used by attackers to steal sensitive information, gain unauthorized access to your systems, or disrupt your business. . With this knowledge, you can protect your organization and prevent potential attacks.
 |
| A screenshot of the Intruder vulnerability management platform, designed to run thousands of security checks, identifying vulnerabilities in web apps, APIs, cloud systems, and more. |
What is the vulnerability management process?
- Running a vulnerability scan
- Assess vulnerability risk
- Prioritize and resolve vulnerabilities
- Continuous monitoring
What is attack surface management?
The main difference between vulnerability management and attack surface management is scope. Attack surface management (ASM) includes asset discovery, helping you find all your digital assets and services and then reducing or minimizing their exposure to prevent hackers from exploiting them.
With ASM, all known or unknown resources (on-premises, cloud, subsidiary, third-party, or partner environments) are discovered from the attacker’s perspective from outside the organization. If you don’t know what you have, how can you protect it?
Take the example of an admin interface like cPanel or a firewall admin page: today they may be secure against all known current attacks, but a vulnerability may be discovered tomorrow – when it becomes a significant risk. If you monitor and reduce your attack surface, regardless of vulnerabilities, you will become more difficult to attack.
Therefore, a significant part of attack surface management is to reduce exposure to possible future vulnerabilities by removing unnecessary services and resources from the Internet. But to do this, you first need to know what’s there.
What is the attack surface management process?
- Discover and map all your digital assets
- Ensure visibility and create documentation of what exists
- Run a vulnerability scan to identify any weaknesses
- Automate so anyone building the infrastructure can do it securely
- Continuously monitor the creation of new infrastructure and services
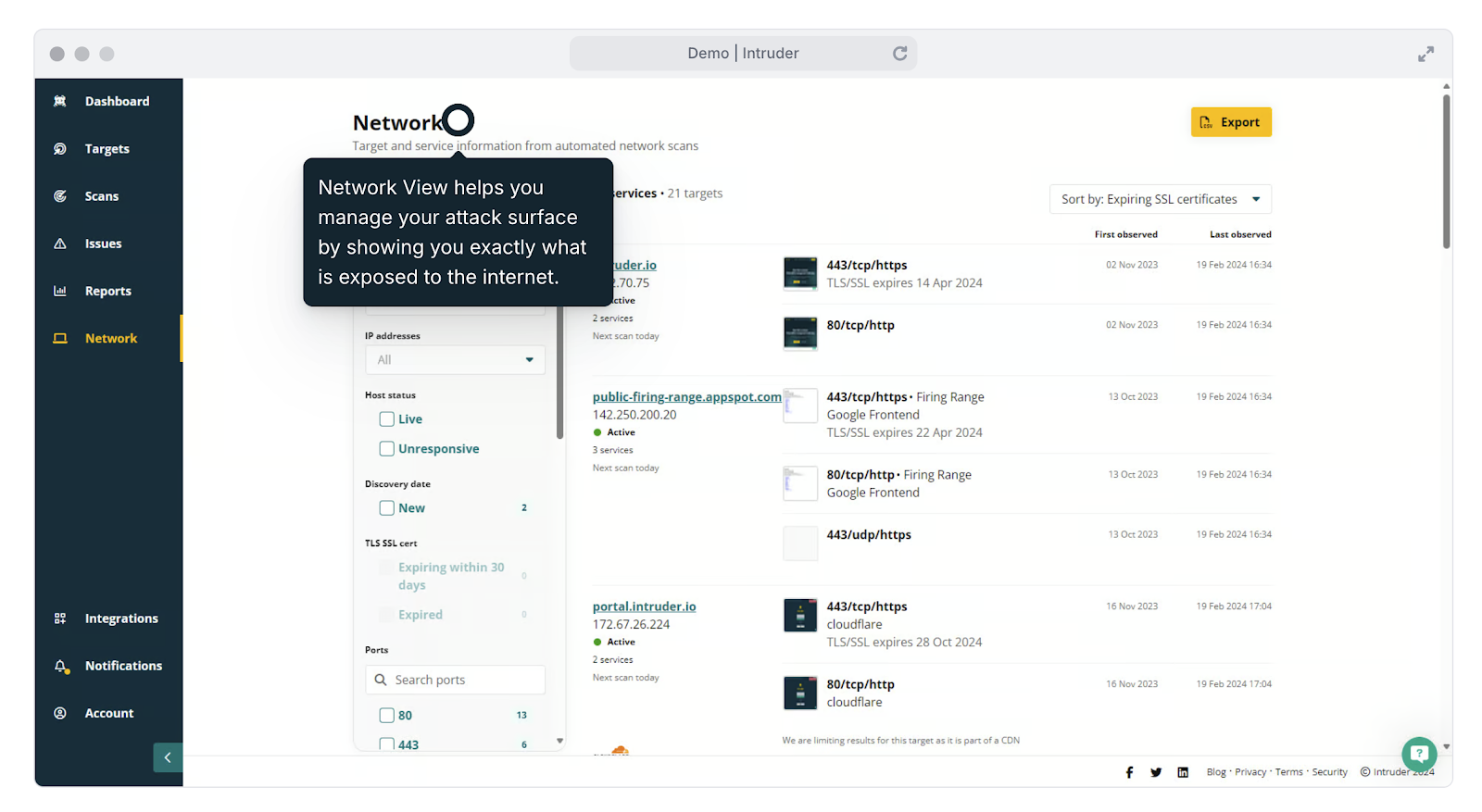 |
| Intruder’s attack surface management capabilities help you stay on top of changes in your environment, such as recently opened ports and services. |
How does attack surface management differ from vulnerability management?
Vulnerability management is the process of identifying and prioritizing vulnerabilities in IT infrastructure and applications. Attack surface management goes a step further by identifying and analyzing the attack surface: all exposed devices, entry points, and services that an attacker could potentially use to gain access to your systems or data.
Is it possible to combine attack surface management and vulnerability management?
While ASM and VM may have different scopes and objectives, they are not mutually exclusive. Used in combination, they create a much more holistic, robust and comprehensive cybersecurity strategy. By identifying your assets and vulnerabilities, you can prioritize your security efforts and allocate resources more effectively, which will help you reduce the likelihood of a successful attack and any potential impact.
How Intruder can help with ASM and VM
Ultimately, you want to leave no stone unturned when it comes to cybersecurity. Modern VM and ASM solutions like Intruder can detect vulnerabilities affecting your organization. It gives you greater visibility and control over your attack surface, monitors network changes and SSL/TLS certificate expiration dates, helps you stay on top of your cloud infrastructure, and lets you only pay for active targets. Why not check it out for yourself with a 14-day free trial?