
Cybersecurity researchers have uncovered an intricate multi-stage attack that leverages invoice-themed phishing lures to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm, NanoCore RAT and a thief targeting crypto wallets .
The email messages come with Scalable Vector Graphics (SVG) file attachments that, when clicked, trigger the infection sequence, Fortinet FortiGuard Labs said in a technical report.
The modus operandi is notable for using the BatCloak and ScrubCrypt malware obfuscation engine to deliver the malware in the form of obfuscated batch scripts.
BatCloak, offered for sale to other threat actors since late 2022, has its basis in another tool called Jlaive. Its main feature is to load a next-stage payload in a way that evades traditional detection mechanisms.

According to research conducted by Trend Micro last year, ScrubCrypt, a crypter first documented by Fortinet in March 2023 in connection with a cryptojacking campaign orchestrated by the 8220 gang, is considered one of the iterations of BatCloak.
In the latest campaign analyzed by the cybersecurity firm, the SVG file acts as a conduit to release a ZIP archive that contains a batch script likely created using BatCloak, which then decompresses the ScrubCrypt batch file to ultimately execute Venom RAT, but not before having configured persistence on the host and taking measures to bypass AMSI and ETW protections.
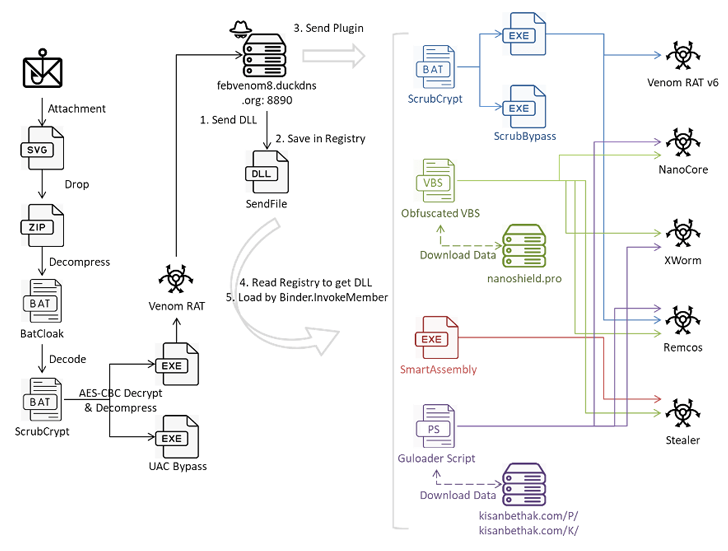
A fork of Quasar RAT, Venom RAT allows attackers to take control of compromised systems, collect sensitive information, and execute commands received from a command and control (C2) server.
“Although the main program of Venom RAT may seem simple, it maintains communication channels with the C2 server to acquire additional plugins for various tasks,” said security researcher Cara Lin. This includes Venom RAT v6.0.3 with keylogger functionality, NanoCore RAT, XWorm and Remcos RAT.
“This [Remcos RAT] plugin was distributed by VenomRAT’s C2 using three methods: an obfuscated VBS script named “remcos.vbs”, ScrubCrypt, and Guloader PowerShell,” Lin added.

Using the plugin system also provides a thief that collects system information and extracts data from folders associated with wallets and applications such as Atomic Wallet, Electrum, Ethereum, Exodus, Jaxx Liberty (retired as of March 2023), Zcash, Foxmail and Telegram to a remote server.
“This analysis reveals a sophisticated attack that leverages multiple layers of obfuscation and evasion techniques to distribute and execute VenomRAT via ScrubCrypt,” Lin said.
“Attackers use a variety of methods, including phishing emails with malicious attachments, obfuscated script files, and Guloader PowerShell, to infiltrate and compromise victims’ systems. Additionally, the implementation of plug-ins across different payloads highlights the versatility and adaptability of the attack campaign.”