
A threat actor tracked as TA547 targeted dozens of German organizations with an information stealer called Rhadamanthys as part of an invoice-themed phishing campaign.
“This is the first time researchers have observed TA547 using Rhadamanthys, an information stealer used by multiple cybercriminals,” Proofpoint said. “Furthermore, the actor appeared to be using a PowerShell script that researchers suspect was generated by a large language model (LLM).”
TA547 is a prolific financially motivated threat actor, active since at least November 2017, that uses email phishing lures to deliver a variety of Android and Windows malware such as ZLoader, Gootkit, DanaBot, Ursnif and even Adhubllka ransomware .
In recent years, the group has evolved into an initial access broker (IAB) for ransomware attacks. The use of geofencing tricks to limit payloads to specific regions has also been observed.

The emails observed as part of the latest campaign impersonate the German company Metro AG and contain a password-protected ZIP file containing a ZIP archive which, when opened, triggers the execution of a remote PowerShell script to initiate the thief Rhadamanthys directly into memory.
Interestingly, the PowerShell script used to load Rhadamanthys includes “grammatically correct and hyper-specific comments” for every statement in the program, raising the possibility that it may have been generated (or rewritten) using an LLM.
The alternative hypothesis is that TA547 copied the script from another source who had used generative AI technology to create it.
“This campaign represents an example of some technical changes compared to TA547, including the use of compressed LNKs and the previously unobserved Rhadamanthys rogue,” Proofpoint said. “It also provides insights into how threat actors are exploiting likely LLM-generated content in malware campaigns.”
The development comes as phishing campaigns also rely on unusual tactics to facilitate credential harvesting attacks. In these emails, recipients are notified of a voice message and asked to click on a link to access it.
The payload retrieved from the URL is heavily obfuscated HTML content that executes JavaScript code embedded in an SVG image when the page is rendered on the target system.
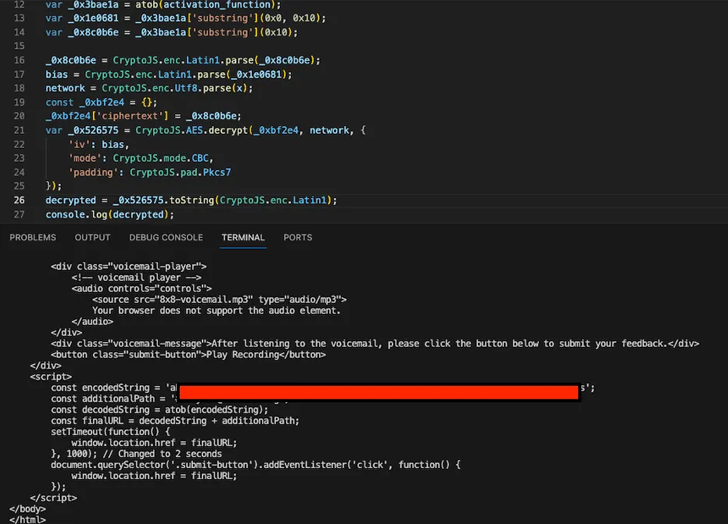
Inside the SVG data is “encrypted data containing a second-stage page that requires the target to enter their credentials to access the voice message,” Binary Defense said, adding that the page is encrypted using CryptoJS.
Other email-based attacks paved the way for Agent Tesla, which has emerged as an attractive option for threat actors because “it is a cost-effective malware service with multiple capabilities to exfiltrate and steal user data,” according to Cofense.
Social engineering campaigns have also taken the form of malicious ads posted on search engines like Google that trick unsuspecting users into downloading fake installers for popular software like PuTTY, FileZilla, and Room Planner to ultimately implement Nitrogen and IDAT Loader.

The infection chain associated with IDAT Loader is notable in that the MSIX installer is used to launch a PowerShell script which, in turn, contacts a Telegram bot to retrieve a second PowerShell script hosted on the bot.
This PowerShell script then acts as a conduit to deliver another PowerShell script used to bypass Windows Antimalware Scan Interface (AMSI) protections and trigger the loader to run, which subsequently proceeds to load the SectopRAT Trojan.
“Endpoints can be protected from malicious ads through group policies that limit traffic from major and lesser-known ad networks,” said Jérôme Segura, principal threat researcher at Malwarebytes.