
The Iranian actor known as MuddyWater has been attributed to a new command and control (C2) infrastructure called DarkBeatC2becoming the latest such tool in its arsenal after SimpleHarm, MuddyC3, PhonyC2 and MuddyC2Go.
“Even if you occasionally move to a new remote administration tool or change the C2 framework, MuddyWater’s methods remain constant,” Deep Instinct security researcher Simon Kenin said in a technical report published last week.
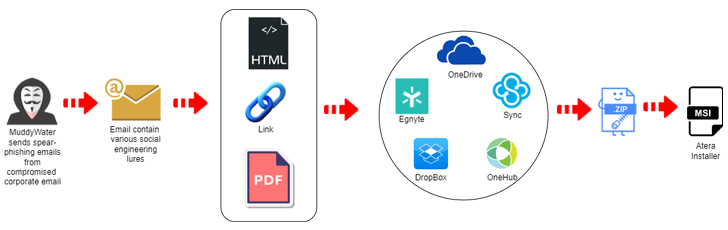
MuddyWater, also called Boggy Serpens, Mango Sandstorm and TA450, is believed to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS). It is known to have been active since at least 2017 and orchestrates spear phishing attacks that lead to the deployment of various legitimate remote monitoring and management (RMM) solutions on compromised systems.
Previous findings from Microsoft show that the group has ties to another Iranian threat activity cluster tracked as Storm-1084 (also known as DarkBit), with the latter exploiting access to orchestrate destructive attacks against Israeli entities.

The latest attack campaign, details of which were also previously revealed by Proofpoint last month, begins with spear-phishing emails sent from compromised accounts that contain links or attachments hosted on services like Egnyte to deliver Atera Agent software .
One of the URLs in question is “kinneretacil.egnyte[.]com”, where the subdomain “kinneretacil” refers to “kinneret.ac.il”, an educational institution in Israel and client of Rashim, which, in turn, was hacked by Lord Nemesis (aka Nemesis Kitten or TunnelVision) as part of a supply chain attack that targeted the country’s academic sector.
Lord Nemesis is suspected of being a “falsetivist” operation directed against Israel. It’s also worth noting that Nemesis Kitten is a private contractor company called Najee Technology, a subgroup within Mint Sandstorm backed by Iran’s Islamic Revolutionary Guard Corps (IRGC). The company was sanctioned by the US Treasury in September 2022.
“This is important because if ‘Lord Nemesis’ had succeeded in breaching Rashim’s email system, he could have breached the email systems of Rashim’s clients using the administrator accounts that we now know they obtained from ‘Rashim’,” Kenin explained.
The network of connections raised the possibility that MuddyWater may have used the email account associated with Kinneret to distribute the links, thus giving the messages an illusion of trust and tricking recipients into clicking them.
“Although not conclusive, the time frame and context of events indicate a potential handover or collaboration between the IRGC and MOIS to inflict as much damage as possible on Israeli organizations and individuals,” Kenin further added.
The attacks are also notable because they rely on a series of domains and IP addresses collectively called DarkBeatC2 that are responsible for managing the infected endpoints. This is achieved using PowerShell code designed to establish contact with the C2 server after gaining initial access through other means.
According to independent findings from Palo Alto Networks Unit 42, the threat actor was observed abusing the AutodialDLL function of the Windows registry to sideload a malicious DLL and ultimately set up connections with a DarkBeatC2 domain.
The mechanism, in particular, involves establishing persistence through a scheduled task that runs PowerShell to leverage the AutodialDLL registry key and load the DLL for the C2 framework. The cybersecurity firm said the technique was used in a cyberattack aimed at an unnamed target in the Middle East.
Other methods used by MuddyWater to establish a C2 connection include using a first-stage payload delivered via spear phishing email and leveraging DLL sideloading to execute a malicious library.
A successful contact allows the infected host to receive PowerShell responses which, in turn, retrieve two more PowerShell scripts from the same server.
While one of the scripts is designed to read the contents of a file named “C:\ProgramData\SysInt.log” and transmit it to the C2 server via an HTTP POST request, the second script periodically queries the server for additional payloads and writes the results of execution in “SysInt.log.” The exact nature of the next stage payload is currently unknown.

“This framework is similar to previous C2 frameworks used by MuddyWater,” Kenin said. “PowerShell remains their ‘bread and butter.'”
Curious Snakes Target Defense Sector with FalseFont Backdoor
The disclosure comes as Unit 42 exposed the inner workings of a backdoor called FalseFont used by an Iranian threat actor known as Peach Sandstorm (also known as APT33, Curious Serpens, Elfin, and Refined Kitten) in attacks against the aerospace and of the defense.
“Threat actors mimic legitimate HR software, using a fake recruitment process to trick victims into installing the backdoor,” security researchers Tom Fakterman, Daniel Frank and Jerome Tujague said, describing FalseFont as “highly targeted aiming.”
Once installed, it presents a login interface that impersonates an aerospace company and captures credentials, as well as educational and employment history entered by the victim on a C2 server controlled by the threat actor in JSON format.
The implant, in addition to the graphical user interface (GUI) component for user input, also stealthily activates a second component in the background that establishes persistence on the system, collects system metadata, and executes commands and processes sent by the C2 server .
Other features of FalseFont include the ability to download and upload files, steal credentials, take screenshots, kill specific processes, execute PowerShell commands, and automatically update malware.