
Extremely low RPO with continuous data protection:
Takes you back to a few seconds before an attack
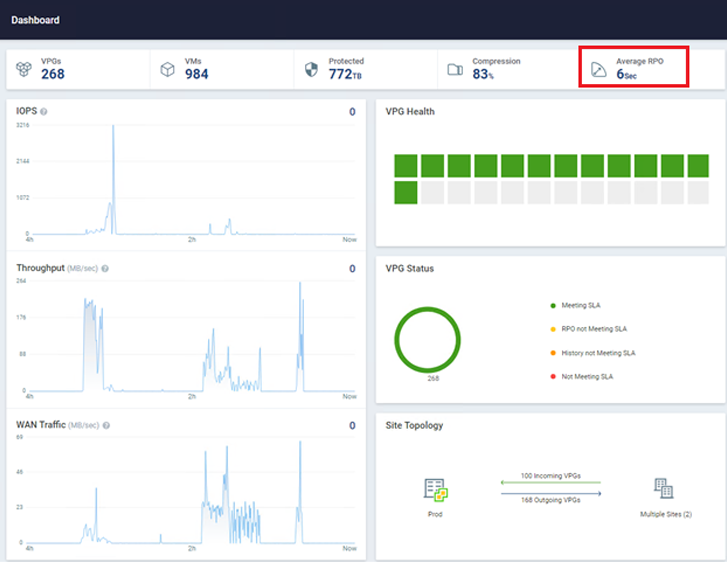
Zerto, a Hewlett Packard Enterprise company, can help you detect and restore ransomware in near real-time. This solution leverages Continuous Data Protection (CDP) to ensure that all workloads have the lowest possible Recovery Point Objective (RPO). The most valuable aspect of CDP is that it does not use snapshots, agents, or any other periodic data protection methodology. Zerto has no impact on production workloads and can achieve RPOs in the range of 5-15 seconds on thousands of virtual machines simultaneously. For example, the environment in the image below has nearly 1,000 VMs protected with an average RPO of just six seconds!
Application-centric protection:
Group your VMs to gain application-level control
You can protect your virtual machines with Zerto’s application-centric approach using virtual protection groups (VPGs). This logical grouping of VMs ensures that the entire application stack can be recovered into a single cohesive unit, with checkpoints taken a few seconds apart from the exact same point in time across multiple VMs in the group.
Real-time online encryption detection:
Get early warning when an attack occurs
Zerto can detect possible ransomware attacks in real time, unlike other products that must wait for backup to complete before scanning data. Zerto scans data online in real time as it is replicated, giving you the first warning sign of a potential cyber attack occurring within your environment.
Learn more about real-time encryption with Zerto.
Let’s take a look at what a ransomware attack and Zerto recovery looks like.
In a real-life cyber attack scenario, you would not knowingly encrypt your files. It is evident that the file server in this image was infected with ransomware, which encrypted the files hosted within it.
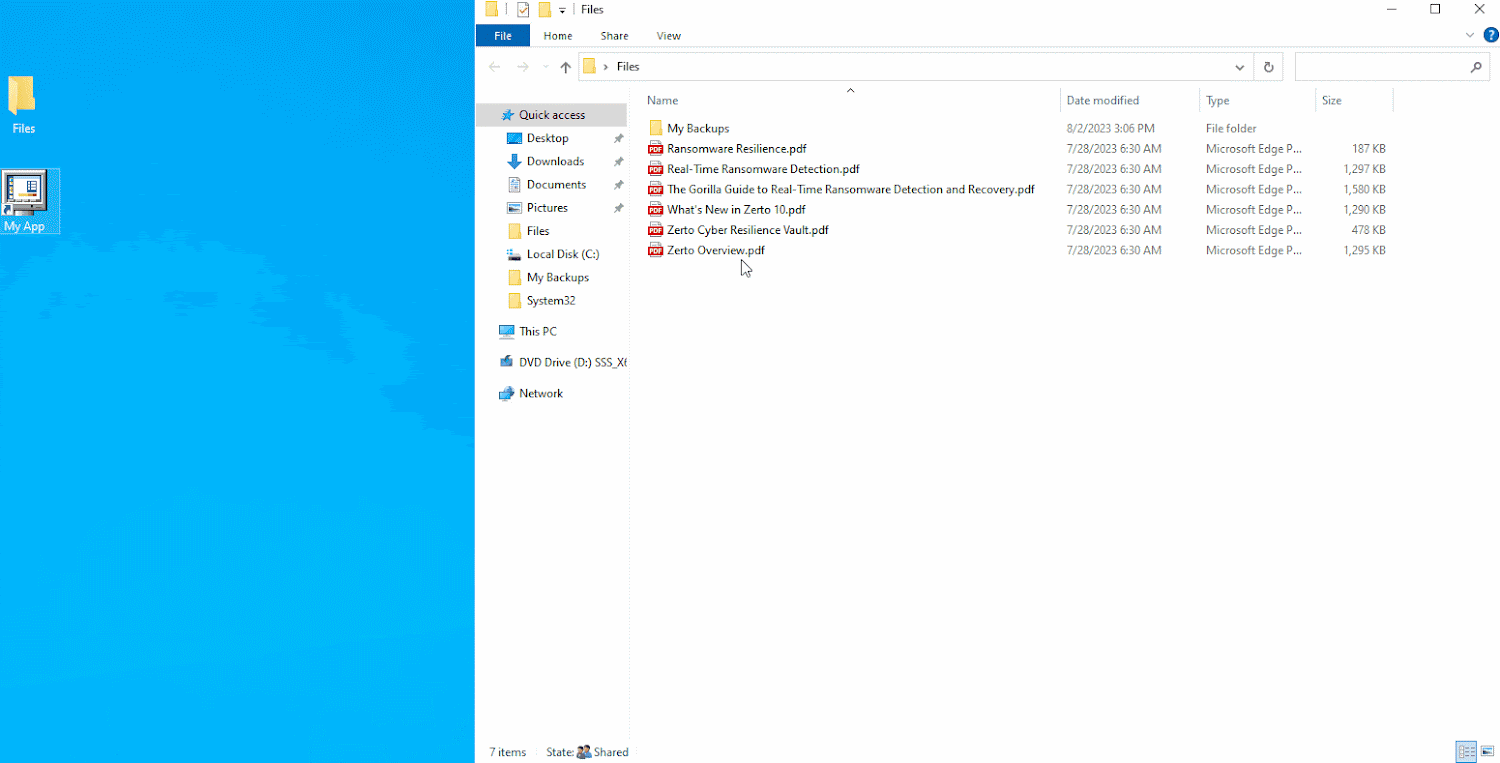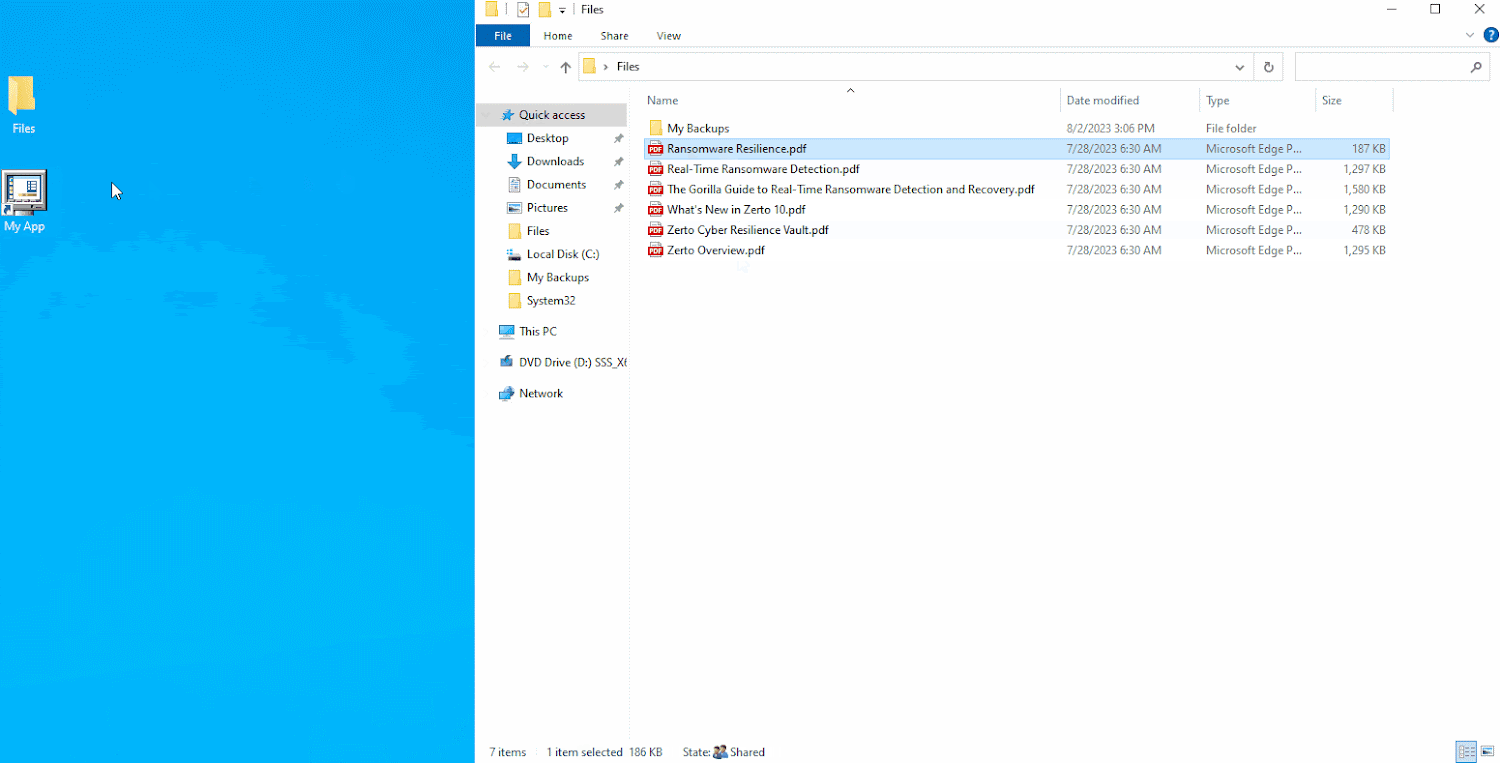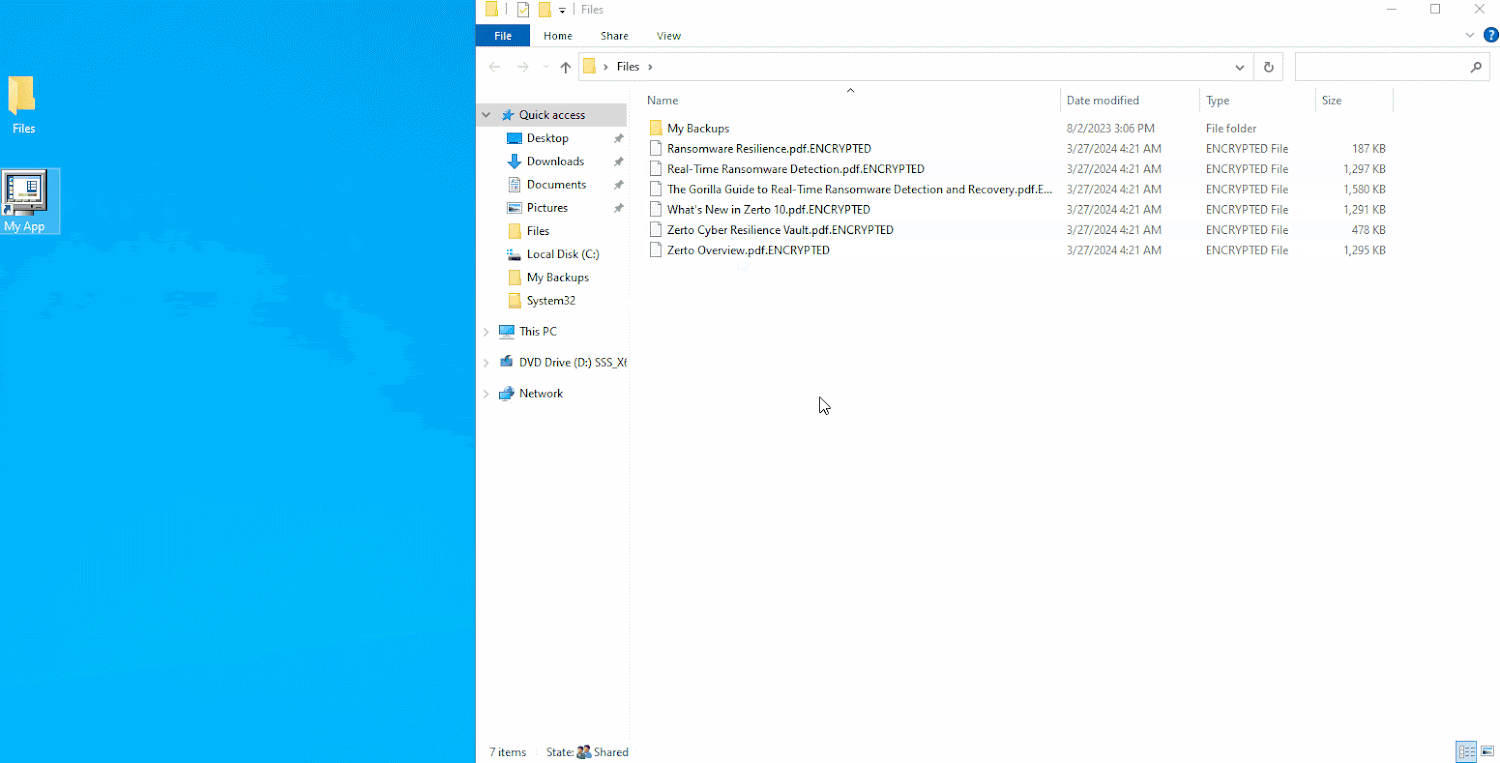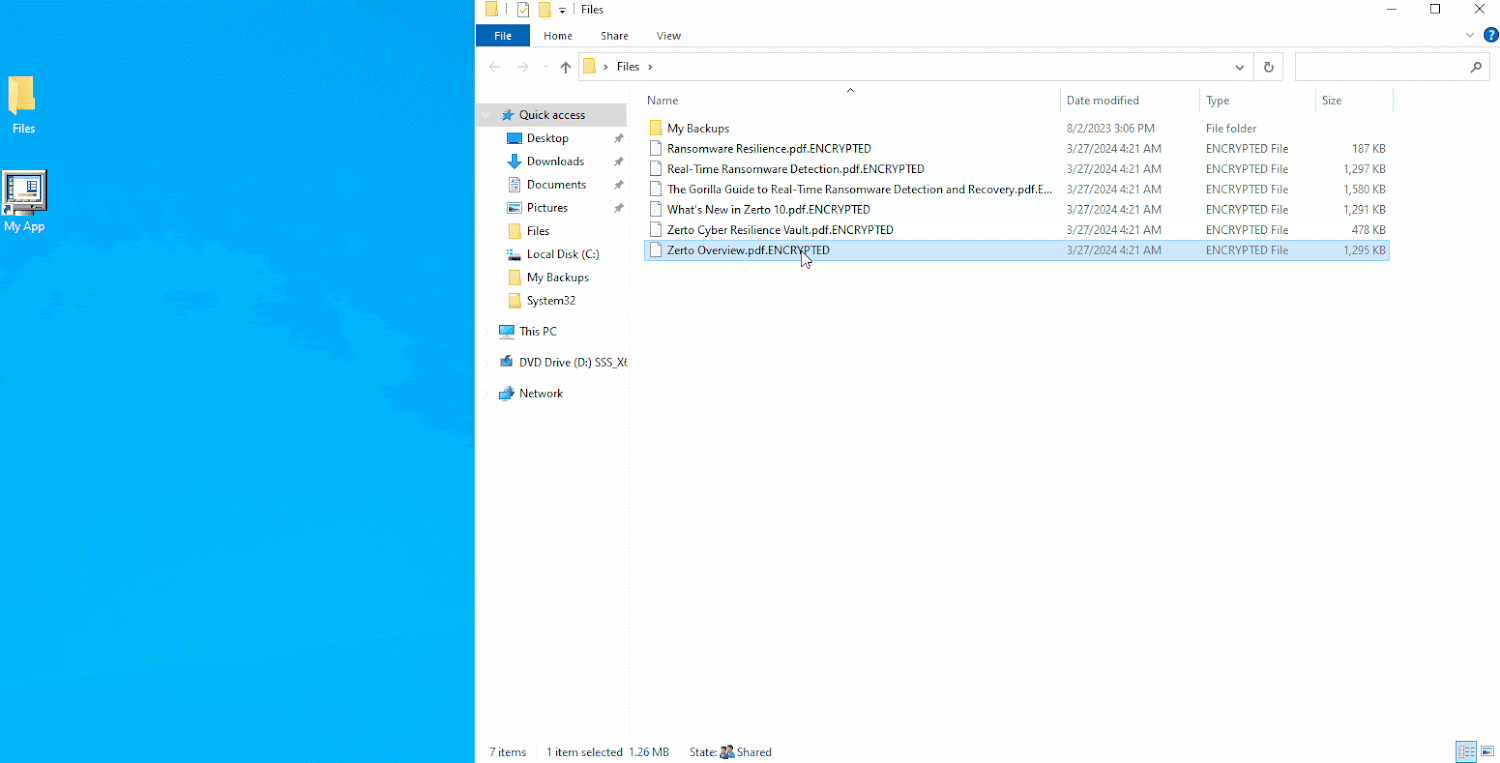
After a ransomware attack, your files will all be encrypted and cannot be used.
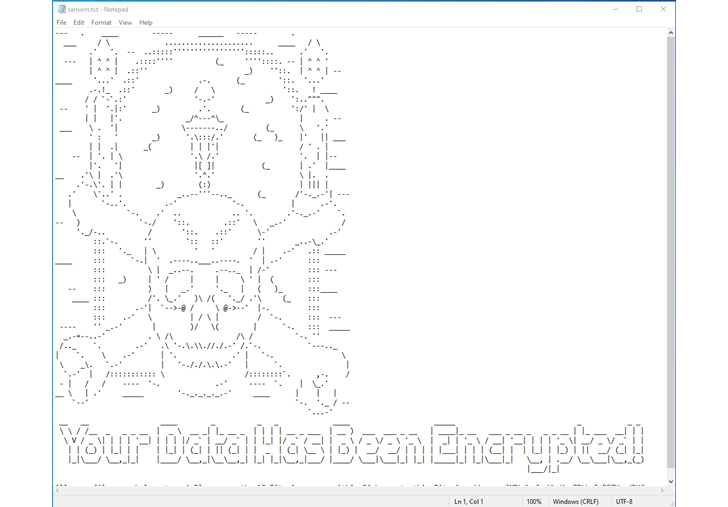
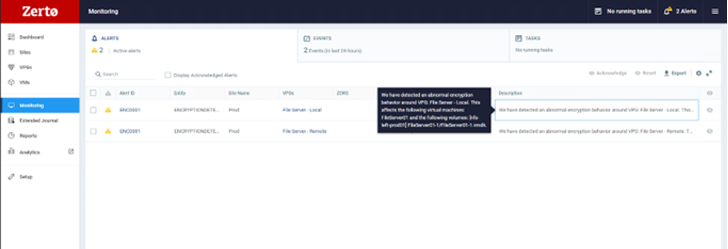
Using Zerto, at the onset of a cyber attack, you will see an alert triggered in your Zerto console, indicating potential suspicious activity on your VM. You can drill down to see the exact disk from which the anomalous activity is generated, allowing you to quickly identify infected machines, limit the blast radius, and create a timeline of events to facilitate post forensic investigations and analysis -recovery, as shown in this image.
Instant file-level recovery:
Restore an application or VM or even drill down to a single file
In the event of an attack, you will receive automatic alerts via email or notifications from Zerto extensible APIs, allowing you to act quickly. You can restore files directly to the VM in real time, seconds before the encryption event, ensuring minimal data loss.
The following graphic shows how. First select RestoreThen File.
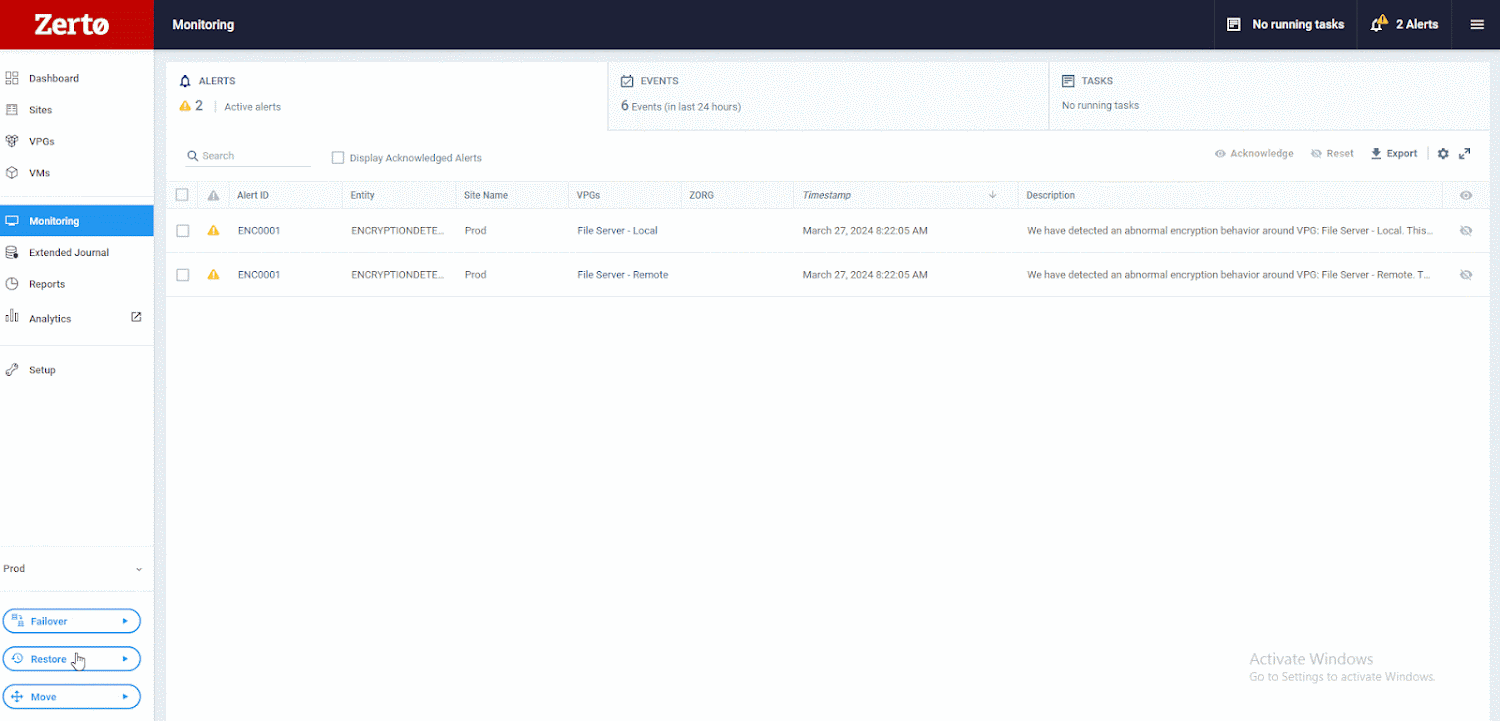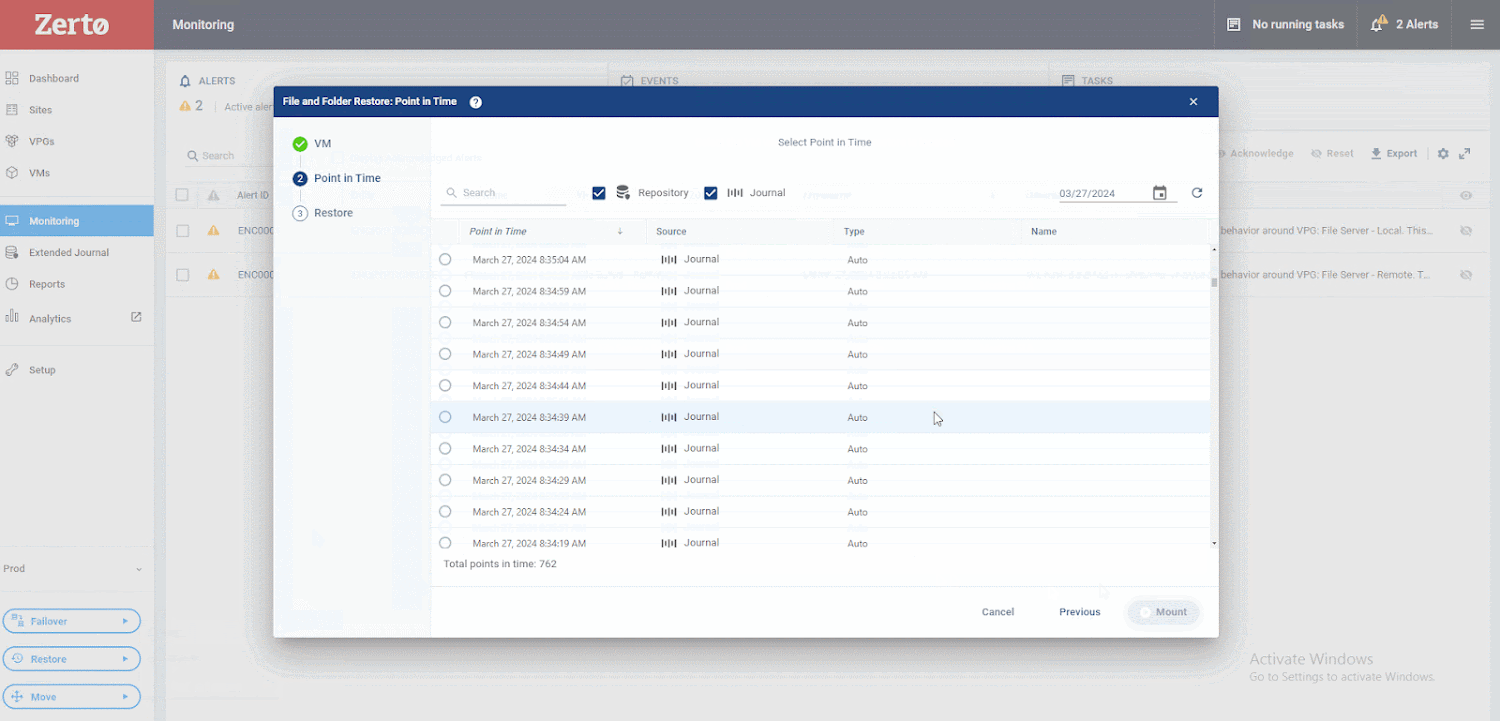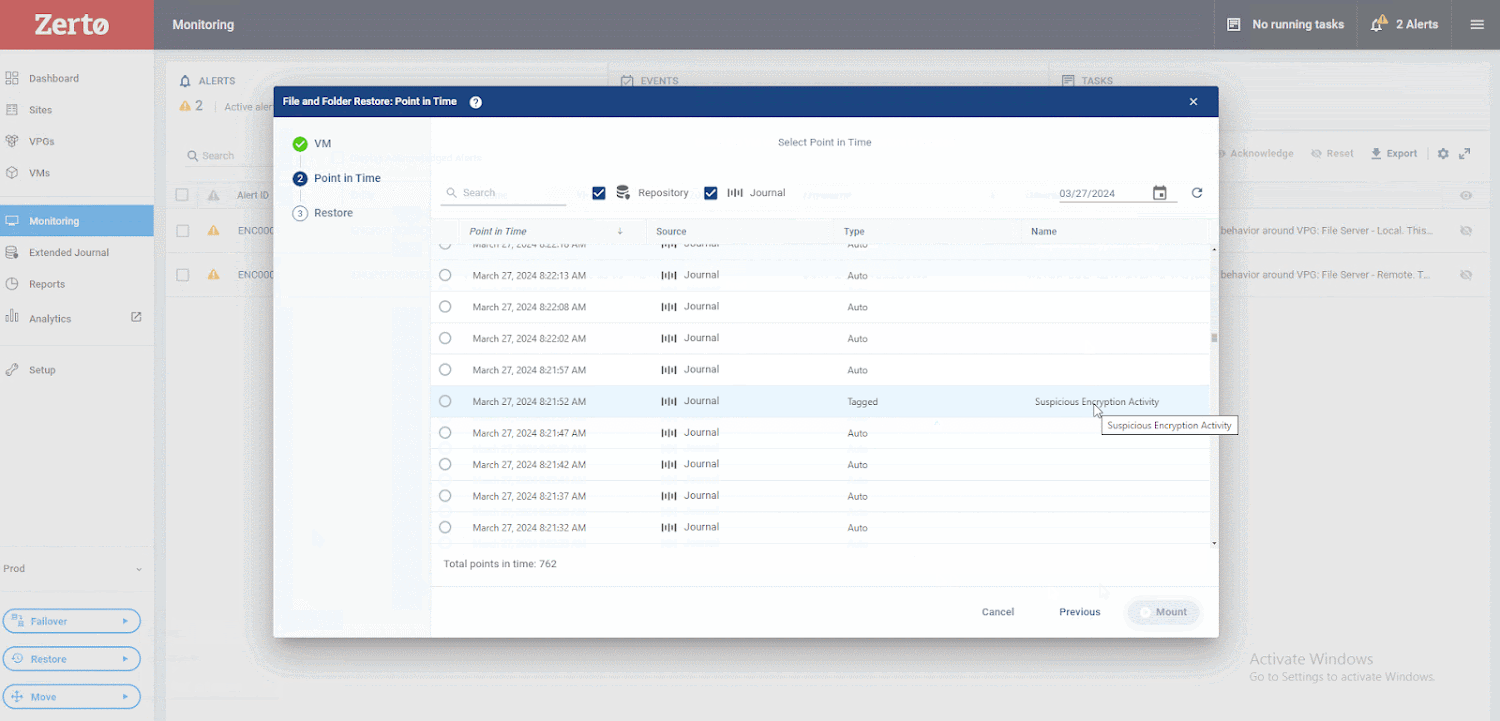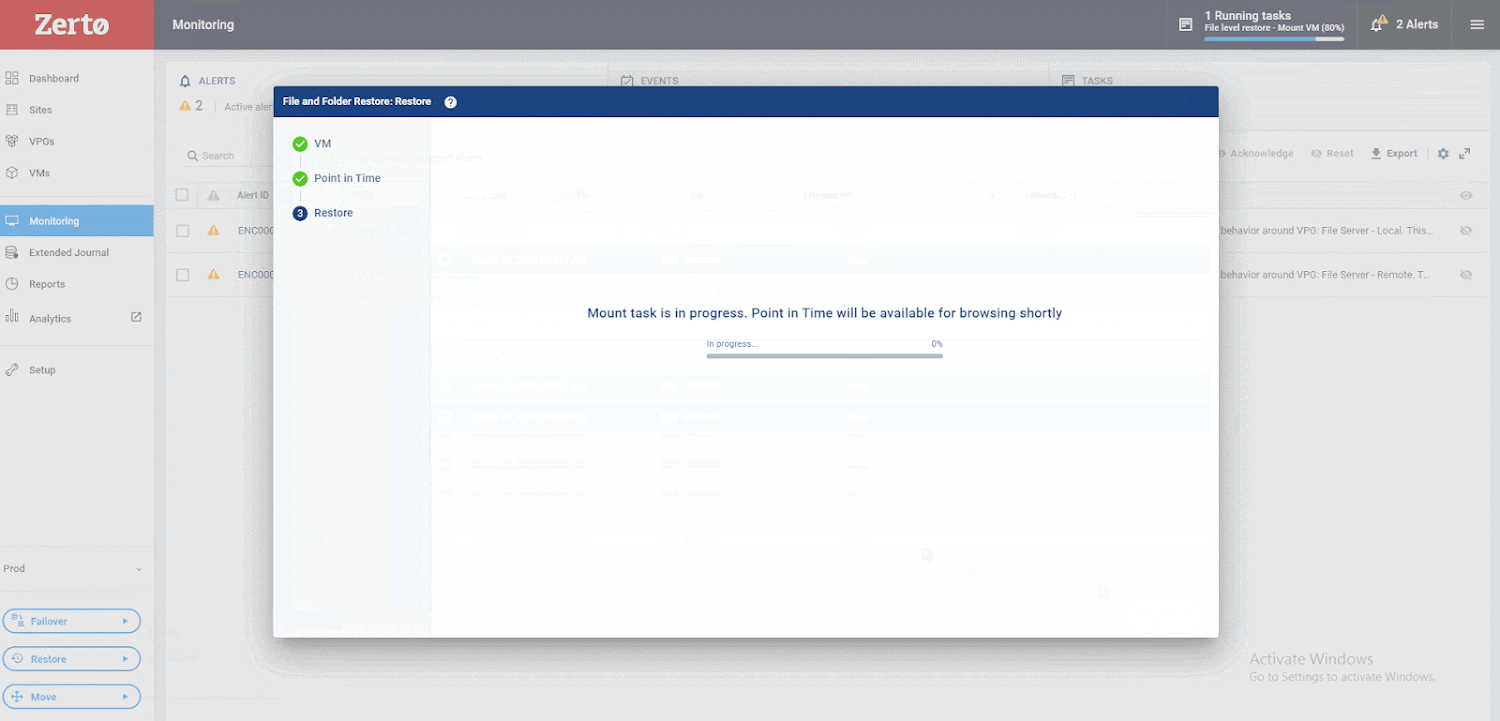
Next, choose the VM from and to which you want to restore. Once you’ve made these selections, you can browse Zerto’s unique journaling features. You’ll notice that there are over 700 points in time, just seconds apart, that you can recover from. This ensures that your RPO is as low as possible. You will then review these checkpoints, identifying the ones that Zerto has flagged as suspicious. After that, you can go back a bit and examine the ones marked as clean. This process allows you to recover directly before suspicious activity is detected.
Now you can browse the files and folders you want to restore using a simple wizard. Select the files you want to restore, choose a set of credentials to authenticate to the VM and press Restore,

as shown below. Your files will now be restored directly to production without the use of agents within the operating system and with only a few seconds of data loss.

The recovery process is quick and easy to accomplish, with minimal disruption to any organization.
Let’s now consider how to recover in the event of a large-scale attack affecting multiple VMs or even hundreds at once. Using the failover feature within Zerto, you can trigger a complete failover of all selected VPGs and the VMs within them to a secondary site. This subsite could be another VMware site, Hyper-V, or even a public cloud. With full automation and orchestration, a Zerto failover can achieve benefits like these:
- Thousands of VMs with an RTO of minutes
- Completely re-IP each VM if necessary
- Direct restore to the production-grade storage of your choice without the need for additional migrations (such as Storage vMotion)
- Direct recovery to production-grade processing without additional steps like vMotion
This type of recovery is ideal for computer recovery because large-scale restores can be difficult to achieve with backup tools not designed for large-scale recovery.
Rapid failover to secondary site with full automation and orchestration: Mobilize, move and restore with automated processes

As you can see, Zerto has some unique and exciting capabilities in terms of ransomware resilience.
To summarise:
- Zerto lets you recover within minutes or seconds before an attack, from files and folders to thousands of VMs building complex applications.
- Real-time online encryption detection helps identify anomalous activity, limit the blast radius, and provide the first warning sign that an attack may occur.
- A comprehensive suite of built-in automation and orchestration means no additional tools are needed to ensure large-scale recoveries are as simple and fast as possible.
Don’t wait for an attack to happen! Protect your organization and gain trust with Zerto. Try Zerto for free for 14 days!