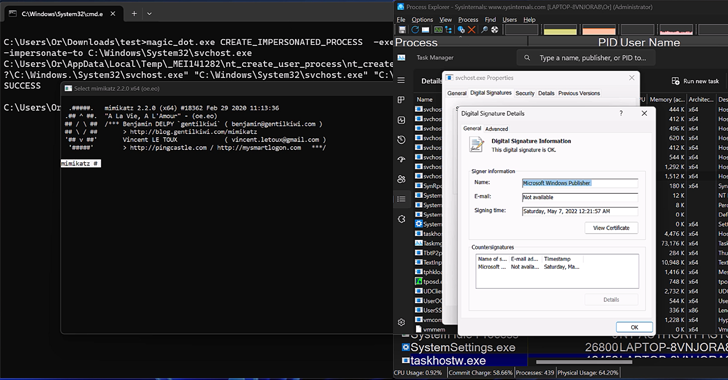
New research has found that the process of path conversion from DOS to NT could be exploited by threat actors to gain rootkit-like capabilities to hide and impersonate files, directories, and processes.
“When a user executes a function that takes the path argument in Windows, the DOS path where the file or folder is located is converted to an NT path,” said Or Yair, security researcher at SafeBreach, in an email analysis presented at the Black Hat Asian Conference last week.
“During this conversion process, there is a known issue where the function removes trailing periods from any path element and all trailing spaces from the last path element. This action is completed by most user space APIs in Windows .”
These so-called MagicDot routes enable rootkit-like functionality accessible to any non-privileged user, who could then weaponize them to perform a variety of malicious actions without having administrator permissions and remain undetected.

They include the ability to “hide files and processes, hide files in archives, affect the analysis of preload files, make Task Manager and Process Explorer users believe that a malware file was a verified executable published by Microsoft, disable Process Explorer with denial of service (DoS) vulnerabilities and more.”
The underlying problem in the DOS to NT path conversion process also led to the discovery of four security flaws, three of which have been fixed by Microsoft:
- An elevation of privilege (EoP) deletion vulnerability that could be used to delete files without the required privileges (to be addressed in a future release)
- An elevation of privilege (EoP) write vulnerability that could be used to write to files without required privileges by tampering with the process of restoring a previous version from a volume shadow copy (CVE-2023-32054, CVSS score: 7, 3)
- A Remote Code Execution (RCE) vulnerability that could be used to create a specially crafted archive, which can lead to code execution when extracting files to any location of the attacker’s choice (CVE-2023-36396, CVSS score: 7,8)
- A denial of service (DoS) vulnerability affecting Process Explorer when launching a process with an executable that has a name that is 255 characters long and has no file extension (CVE-2023-42757)
“This research is the first of its kind to explore how known issues that appear harmless can be exploited to develop vulnerabilities and ultimately pose a significant security risk,” Yair explained.

“We believe the implications are relevant not only to Microsoft Windows, which is the most widely used desktop operating system in the world, but also to all software vendors, most of which also allow known issues to persist from version to version. more of their software.”