
A recent IcedID malware attack allowed the threat actor to compromise an unnamed target’s Active Directory domain less than 24 hours after gaining initial access, while also borrowing techniques from other groups like Conti to reach his goals.
“Throughout the attack, the attacker followed a routine of command reconnaissance, credential theft, lateral movement abusing Windows protocols, and executing Cobalt Strike on the newly compromised host,” Cybereason researchers said in a report released this week. week.
IcedID, also known by the name BokBot, started life as a banking trojan in 2017 before evolving into a dropper for other malware, joining Emotet, TrickBot, Qakbot, Bumblebee and Raspberry Robin.
Attacks involving the handover of IcedIDs have exploited a variety of methods, especially in the wake of Microsoft’s decision to block macros from Office files downloaded from the web.
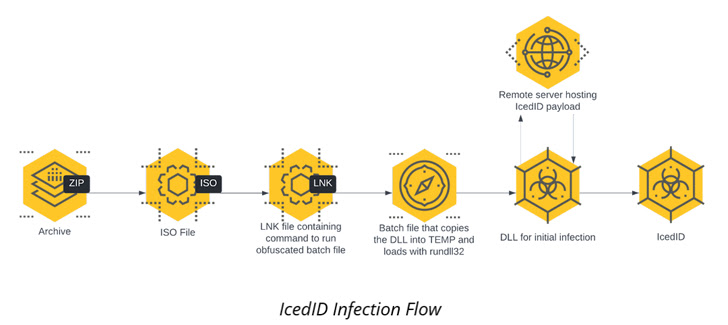
Cybereason’s detailed intrusion is no different as the infection chain starts with an ISO image file contained in a ZIP archive culminating in the execution of the IcedID payload.
The malware then establishes persistence on the host via a scheduled task and communicates with a remote server to download next stage payloads, including the Cobalt Strike Beacon for the next reconnaissance task.
It also performs lateral movement across the network and runs the same Cobalt Strike Beacon on all those workstations, then proceeds to install Atera Agent, a legitimate remote administration tool, as a redundant remote access mechanism.
“Using IT tools like this allows attackers to create an additional ‘backdoor’ for themselves in case their initial persistence mechanisms are discovered and corrected,” the researchers said. “These tools are less likely to be detected by antivirus or EDR, and also more likely to be cleared as false positives.”
The Cobalt Strike Beacon is also used as a conduit to download a C# tool called Rubeus for credential theft, ultimately allowing the threat actor to laterally move to a Windows server with domain administrator privileges.
Elevated permissions are then used as a weapon to stage a DCSync attack, allowing the adversary to mimic the behavior of a domain controller (DC) and retrieve credentials from other domain controllers.
Other tools used as part of the attack include a legitimate utility called netscan.exe to scan the network for lateral movement, as well as file synchronization software rclone to exfiltrate directories of interest to the MEGA cloud storage service.
The findings come as Team Cymru researchers shed more light on the BackConnect (BC) protocol used by IcedID to provide additional functionality after compromise, including a VNC module that provides a remote access channel.
“In the case of BC, there appear to be two operators handling the overall process within distinct roles,” the researchers noted last month, adding “much of the activity […] occurs during the typical work week.”
The development also follows a report from Proofpoint in November 2022 that a resurgence in Emotet activity has been linked to the release of a new version of IcedID.
It is worth noting that the use of the Atgera agent and netscan.exe has previously been attributed to ransomware operations such as Conti and LockBit, suggesting that the criminal actors are taking a leaf out of their playbook.