Digital security
In today’s digitally interconnected world, advanced cyber capabilities have become an exceptionally powerful and versatile commercial tool for both nation-states and criminals
January 29, 2024
•
,
4 minutes Read

For thousands of years, nations have engaged in espionage, spying on their neighbors, allies, and adversaries. Traditionally, this realm of “espionage” relied heavily on human intelligence, but this began to change in the early 1890s with the advent of technologies such as the telegraph, telephone, and later radio signal intelligence (SIGINT). However, in today’s digitally interconnected world, advanced cyber capabilities have become an exceptionally powerful and versatile commercial tool for both nation-states and criminals, marking a significant evolution in espionage for the 21st century.
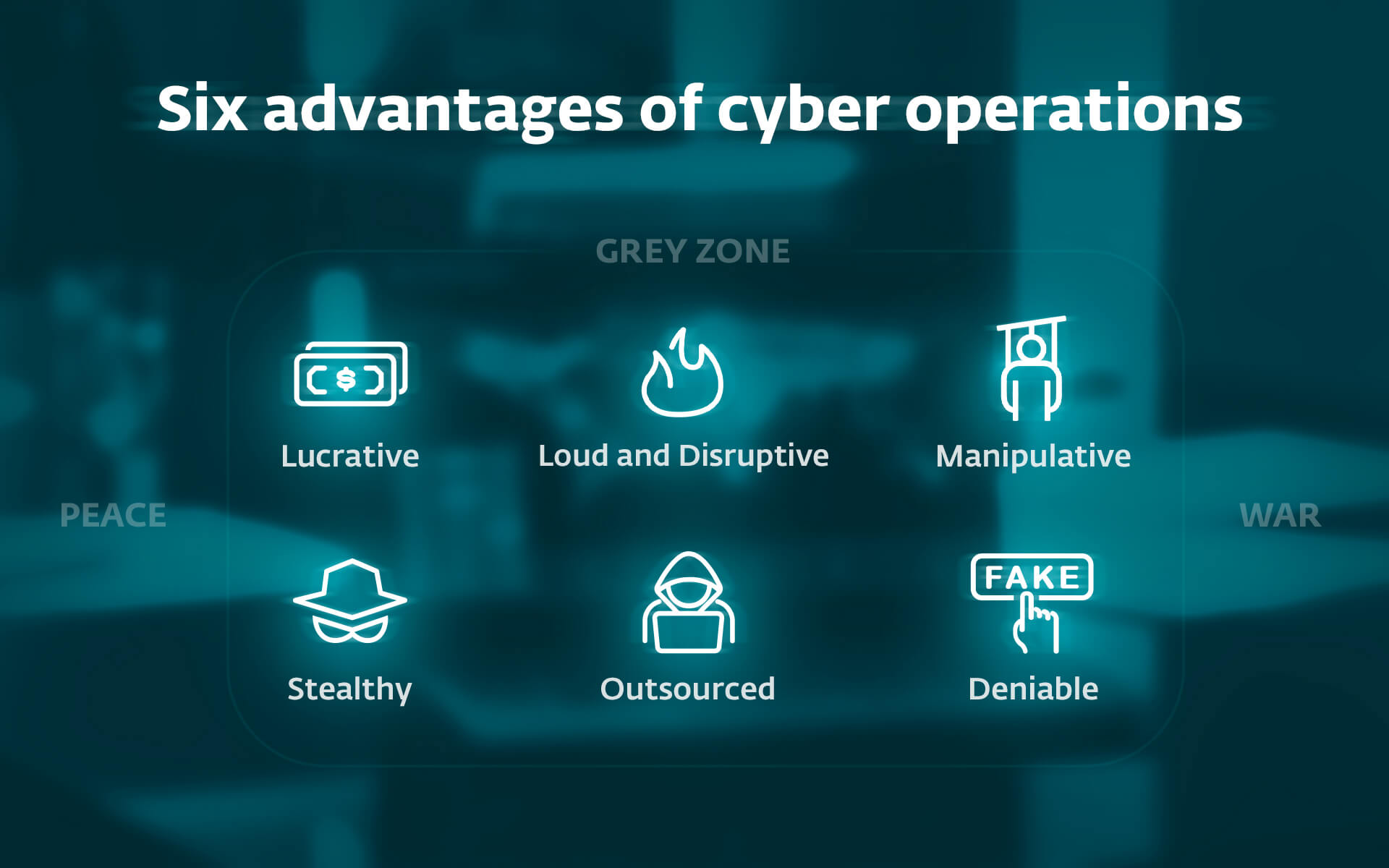
Six benefits of cyber operations
Cyber capabilities are highly valuable to nation-states pursuing political, economic and military objectives, offering significant benefits at a relatively low cost in terms of resources and risk.
- Cyber operations can be furtiveallowing undetected access to target systems for data collection or covert activity, as seen in incidents like SolarWinds.
- They may as well be strong and disruptive or destructive, as evidenced in the conflicts in Ukraine and the Middle East.
- IT means are manipulative, useful for influencing scenarios and increasingly widespread in most continents.
- I am lucrative for profit, as demonstrated by the activities attributed to North Korea, which finances its military program through ransomware campaigns.
- They can be outsourced encouraging third-party operations such as mercenaries or hacktivists willing to undertake these attacks in exchange for money or even political goals and beliefs.
- And they have a high degree of deniabilityas it can take time (including overcoming obfuscation techniques) to trace the origin of an attack with absolute certainty.
The cyber domain is also equipped with a variety of tactics, tools and techniques, supported by a thriving dark web market and an endless array of vulnerabilities to exploit. Furthermore, the lack of meaningful deterrents or punishments for cyber activities increases their attractiveness to nation-states.
Global cyber operations and evolving tactics of major nations
The growing interest in cyber capabilities among nations is evident, with many of them seeking to maximize their cyber potential. Russia, China, Iran, and North Korea are often cited for their malicious cyber activities. It is said that all countries spy, but some are believed to go beyond accepted norms.
China, in particular, has made extensive use of cyber’s unique capabilities. Intelligence agencies of the Five Eyes nations continuously warn of widespread activities of China-aligned groups affecting all continents. More recently, this alliance has highlighted the scale and sophistication of China’s intellectual property theft and acquisition of expertise, a phenomenon described as unprecedented.
Russia, in addition to focusing on Ukraine for disruption and destruction, is also engaged in cyber espionage globally, with Europe in particular in its sights. Russia is also alleged to have conducted influence campaigns in Africa, targeting governments with close Western ties and seeking to undermine governments in other countries that are less supportive of the Russian government.
North Korea-aligned groups remain focused on acquiring defense-related technologies, generating revenue through ransomware, and conducting espionage, especially in Asia. The Lazarus group is probably the most infamous of the North Korea-aligned hackers, including an alleged attack on a Spanish aerospace company.
Iran-aligned groups are expanding their capabilities and reach, extending beyond their traditional focus on the Middle East, particularly targeting Israel.
In addition to these well-known actors, an ever-increasing number of states are developing their capabilities to conduct cyber operations beyond their borders or target foreign entities, including embassies, international organizations, companies and individuals, within their own countries. For example, the alleged Belarusian group MoustachedBouncer is believed to be able to access a Belarusian telecommunications operator to conduct a “man-in-the-middle” attack against foreign entities in Belarus.
But when domestic capacity is insufficient, or to increase deniability, some nations turn to the private sector and cyber mercenaries. The number of nations involved in cyber operations could conservatively be greater than 50 and is growing globally. Indeed, according to CERT-EU, there have been 151 malicious activities of interest against EU institutions, including by groups aligned with Turkey and Vietnam. This global trend highlights the growing importance and evolution of the threat landscape.
A window onto a complex world
Activities in cyberspace offer a glimpse into the complexity of geopolitics, and attacks can often only be understood through the lens of political intent. The three great powers of the world are engaged in a competition for influence, prosperity and power. In most regions there are live conflicts, latent tensions, political, security and economic challenges. In this climate of instability, increased competition, often disillusioned populations and in an increasingly digitally connected world, cyber is an extremely convenient tool for states to use. Nowadays, it is rare for bilateral disputes not to involve some form of cyber dimension on the part of state actors, their proxies, or aligned/influenced hacktivists. While some conflicts between nations in cyberspace are predictable, bilateral conflicts can also erupt without warning.
Securing agreement on binding international standards of reasonable behavior of States in cyberspace seems unrealistic in the medium term, despite the efforts of the United Nations. Faced with this inconvenient reality, the need for greater international cooperation, policy frameworks and awareness campaigns to manage and mitigate the risks associated with these harmful activities is becoming more urgent than ever. Building resilience will require a holistic, society-wide approach, as the cyber domain is set to remain a key battlefield in an increasingly restive world.
