
Threat hunters have identified a new Android malware variant called MoqHao which runs automatically on infected devices without requiring any user interaction.
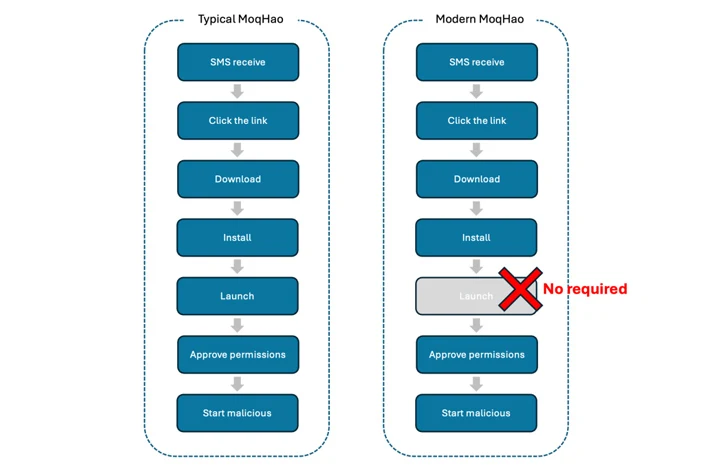
“Typical MoqHao requires users to install and launch the app to achieve the desired purpose, but this new variant requires no execution,” McAfee Labs said in a report published this week. “While the app is installed, their malicious activity starts automatically.”
Campaign targets include Android users located in France, Germany, India, Japan and South Korea.
MoqHao, also called Wroba and XLoader (not to be confused with the Windows and macOS malware of the same name), is an Android-based mobile threat associated with a financially motivated Chinese cluster called Roaming Mantis (aka Shaoye).

Typical attack chains begin with package delivery-themed SMS messages containing fraudulent links that, when clicked by Android devices, lead to malware distribution but redirect victims to credential harvesting pages that impersonate Apple’s iCloud login page when visited from an iPhone.
In July 2022, Sekoia detailed a campaign that compromised at least 70,000 Android devices in France. Early last year, updated versions of MoqHao were discovered to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking, revealing the adversary’s commitment to innovating its arsenal.
The latest iteration of MoqHao continues to be distributed via smishing techniques, but what has changed is that the malicious payload runs automatically upon installation and requires the victim to grant it risky permissions without launching the app, a behavior previously noticed with bogus apps containing HiddenAds Malware virus.
Also new is that links shared in the SMS messages themselves are hidden using URL shorteners to increase the likelihood of the attack being successful. The content of these messages is extracted from the bio field (or description) of fraudulent Pinterest profiles created for this purpose.
MoqHao comes with several features that allow it to stealthily collect sensitive information such as device metadata, contacts, SMS messages, and photos, call specific numbers with silent mode, and enable/disable Wi-Fi, among other things.
McAfee said it reported the findings to Google, which it says is “already working on implementing mitigations to prevent this type of autorun in a future version of Android.”
The development comes as Chinese cybersecurity firm QiAnXin revealed that a previously unknown cybercrime syndicate called Bigpanzi has been linked to the compromise of Android-based smart TVs and set-top boxes (STBs) in order to bundle them into a botnet to conduct distributed waste. of-service attacks (DDoS).

The operation, which has been active since at least 2015, is estimated to control a botnet made up of 170,000 bots active daily, the majority of which are located in Brazil. However, as of August 2023, 1.3 million distinct Brazilian IP addresses have been associated with Bigpanzi.
Infections are made possible by tricking users into installing malicious apps to stream pirated movies and TV shows through untrustworthy websites. The campaign was first made public by Russian antivirus provider Doctor Web in September 2023.
“Once installed, these devices transform into operational nodes within their illicit streaming media platform, providing services such as traffic proxies, DDoS attacks, OTT content delivery, and pirated traffic,” QiAnXin researchers said.
“The possibility that Bigpanzi-controlled TVs and STBs broadcast violent, terrorist or pornographic content, or use increasingly convincing AI-generated videos for political propaganda, represents a significant threat to social order and stability. “