The Iranian-born actor known as Charming Kitten has been linked to a new series of targeted attacks against Middle East political experts with a new backdoor called BASICSTAR creating a fake webinar portal.
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453 and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns that have cast a wide net in their targeting, often singling out think tanks, NGOs and journalists .
“CharmingCypress often employs unusual social engineering tactics, such as engaging targets in prolonged email conversations before sending links to malicious content,” said Volexity researchers Ankur Saini, Callum Roxan, Charlie Gardner, and Damien Cash.
Last month, Microsoft revealed that high-profile individuals working in Middle East affairs were targeted by the adversary to deploy malware such as MischiefTut and MediaPl (aka EYEGLASS) capable of collecting sensitive information from a compromised host.

The group, believed to be affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC), has also deployed several other backdoors such as PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho) and NokNok over the past year, underlining its determination to continue its cyberattack, adapting his tactics and methods despite public exposure.
Phishing attacks observed between September and October 2023 involved Charming Kitten operators impersonating the Rasanah International Institute for Iranian Studies (IIIS) to initiate and build trust among targets.
Phishing attempts are also characterized by the use of compromised email accounts belonging to legitimate contacts and multiple email accounts controlled by threat actors, the latter of which is called Multi-Persona Impersonation (MPI).
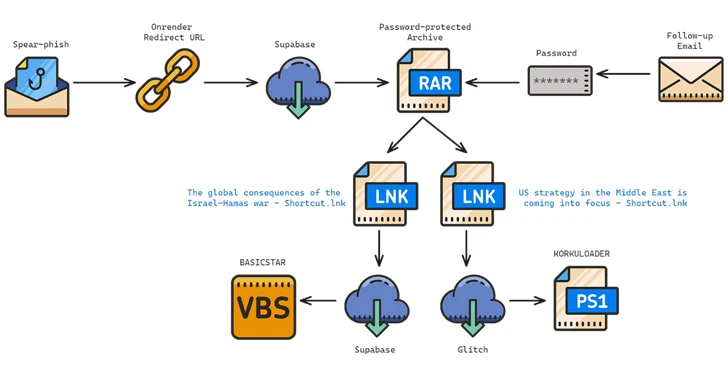
Attack chains typically use RAR archives containing LNK files as a starting point to distribute malware, with messages inviting potential targets to attend a fake webinar on topics of interest to them. One of these multi-stage infection sequences has been observed to deploy BASICSTAR and KORKULOADER, a PowerShell downloader script.
BASICSTAR, a Visual Basic Script (VBS) malware, is capable of gathering basic system information, remotely executing commands transmitted from a command and control (C2) server, and downloading and viewing a decoy PDF file.
Furthermore, some of these phishing attacks are designed to serve different backdoors depending on the machine’s operating system. While Windows victims are compromised with POWERLESS, Apple macOS victims are targeted with a chain of infections culminating in NokNok via a functional VPN application laced with malware.
“This threat actor is highly engaged in conducting surveillance on its targets in order to determine how best to manipulate them and distribute malware,” the researchers said. “Furthermore, few other threat actors have consistently churned out as many campaigns as CharmingCypress, dedicating human operators to support their ongoing efforts.”

The revelation comes as Recorded Future discovered that the IRGC has been targeting Western countries using a network of contracting companies that also specialize in exporting technology for surveillance and offensive purposes to countries such as Iraq, Syria and Lebanon.
The relationship between intelligence, military organizations and contractors based in Iran takes the form of various cyber centers that act as “firewalls” to hide the sponsoring entity.
They include Ayandeh Sazan Sepher Aria (suspected to be associated with Emennet Pasargad), DSP Research Institute, Sabrin Kish, Soroush Saman, Mahak Rayan Afraz and the Parnian Telecommunication and Electronic Company.
“Iranian contracting companies are founded and managed by a close-knit network of people who, in some cases, represent the contractors as board members,” the company said. “The individuals are closely associated with the IRGC and, in some cases, are also representatives of sanctioned entities (such as the IRGC Cooperative Foundation).”