A critical security flaw in the Bricks WordPress theme is being actively exploited by threat actors to execute arbitrary PHP code on sensitive installations.
The flaw, identified as CVE-2024-25600 (CVSS score: 9.8), allows unauthenticated attackers to remotely execute code. Affects all versions of Bricks up to and including 1.9.6.
It was fixed by the theme developers in version 1.9.6.1 released on February 13, 2024, just days after WordPress security vendor Snicco reported the flaw on February 10.
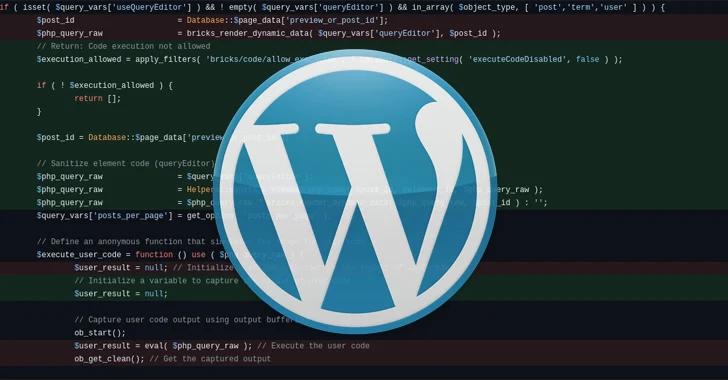
While a proof-of-concept (PoC) exploit has not been released, technical details have been released by both Snicco and Patchstack, noting that the underlying vulnerable code exists in the prepare_query_vars_from_settings() function.
Specifically, this involves the use of security tokens called “nonces” to verify permissions, which can then be used to pass arbitrary commands to execute, effectively allowing a threat actor to take control of a hijacked site. aim.
The nonce value is publicly available on the frontend of a WordPress site, Patchstack said, adding that proper role checks are not enforced.

“Nonces should never be relied upon for authentication, authorization, or access control,” WordPress warns in its documentation. “Secure your functions using current_user_can() and always assume nonces can be compromised.”
WordPress security firm Wordfence said it detected over three dozen attack attempts exploiting the flaw as of February 19, 2024. The exploit attempts are said to have begun on February 14, a day after the public disclosure .
Most attacks come from the following IP addresses:
- 200.251.23[.]57
- 92.118.170[.]216
- 103.187.5[.]128
- 149.202.55[.]79
- 5,252,118[.]211
- 91.108.240[.]52
Bricks is estimated to have approximately 25,000 active installations currently. Plugin users are advised to apply the latest patches to mitigate potential threats.