
A new malware campaign has been observed targeting Redis servers for initial access with the ultimate goal of mining cryptocurrency on compromised Linux hosts.
“This particular campaign involves the use of a number of new system-weakening techniques against the data store itself,” Matt Muir, a security researcher at Cado, said in a technical report.
The cryptojacking attack is facilitated by malware codenamed Migo, an ELF Golang binary featuring compile-time obfuscation and the ability to persist on Linux machines.

The cloud security company said it detected the campaign after identifying an “unusual set of commands” targeting its Redis honeypots designed to lower security defenses by disabling the following configuration options:
These options are suspected to be disabled to send additional commands to the Redis server from external networks and facilitate future exploitations without attracting much attention.
This step is then followed by threat actors setting up two Redis keys, one pointing to an attacker-controlled SSH key and the other to a cron job that retrieves the malicious primary payload from a file transfer service called Transfer.sh , a technique previously identified in early 2023.
The shell script to recover Migo using Transfer.sh is embedded in a Pastebin file which, in turn, is obtained using a curl or wget command.
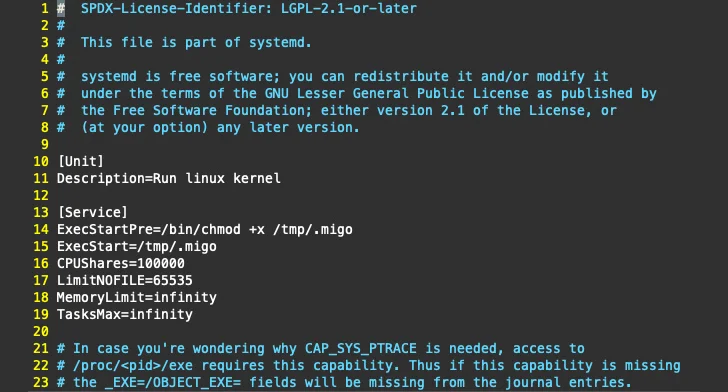 |
| Persistence |
The Go-based ELF binary, in addition to incorporating mechanisms to resist reverse engineering, serves as a downloader for an XMRig installer hosted on GitHub. It is also responsible for performing a series of steps to establish persistence, eliminate competing miners, and launch the miner.
Besides that, Migo disables Security-Enhanced Linux (SELinux) and looks for uninstallation scripts for monitoring agents clustered in compute instances from cloud providers such as Qcloud and Alibaba Cloud. It also distributes a modified version (“libsystemd.so”) of a popular user-mode rootkit called libprocesshider to hide processes and artifacts on disk.
It is worth pointing out that these actions overlap with tactics employed by well-known cryptojacking groups such as TeamTNT, WatchDog, Rocke, and threat actors associated with the SkidMap malware.

“Interestingly, Migo appears to recursively iterate through files and directories in /etc,” Muir noted. “The malware will simply read the files in these locations and do nothing with the contents.”
“One theory is that this may be a (weak) attempt to confuse sandbox and dynamic analysis solutions by performing a large number of benign actions, resulting in a non-malicious classification.”
Another hypothesis is that the malware is looking for an artifact specific to the target environment, although Cado said he found no evidence to support this line of reasoning.
“Migo demonstrates that cloud-focused attackers continue to refine their techniques and improve their ability to exploit web-facing services,” Muir said.
“Although libprocesshider is often used by cryptojacking campaigns, this particular variant includes the ability to hide disk artifacts in addition to the malicious processes themselves.”