North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector around the world.
In a joint warning published by the German Federal Office for the Protection of the Constitution (BfV) and South Korea’s National Intelligence Service (NIS), the agencies said that the aim of the attacks is to plunder advanced defense technologies so “economic” .
“The regime is using military technologies to modernize and improve the performance of conventional weapons and to develop new strategic weapons systems including ballistic missiles, reconnaissance satellites and submarines,” they noted.
The infamous Lazarus Group was accused of one of two hacking incidents, which involved using social engineering to infiltrate the defense sector as part of a long-running operation called Dream Job. The campaign has been running since August 2020 in several waves.
In these attacks, threat actors create a fake profile or leverage legitimate but compromised profiles on platforms like LinkedIn to approach potential targets and build trust with them, before offering lucrative job opportunities and moving the conversation to a different messaging service like WhatsApp. to start the recruitment process.

Victims are then sent coding assignments and job offer documents loaded with malware which, once launched, trigger the infection procedure to compromise their computers.
“Typically, the fact that employees usually do not discuss job offers with colleagues or the employer works in the attacker’s favor,” the agencies said.
“The Lazarus Group changed its tools over the course of the campaign and demonstrated more than once that it is capable of developing everything necessary to adapt the situation.”
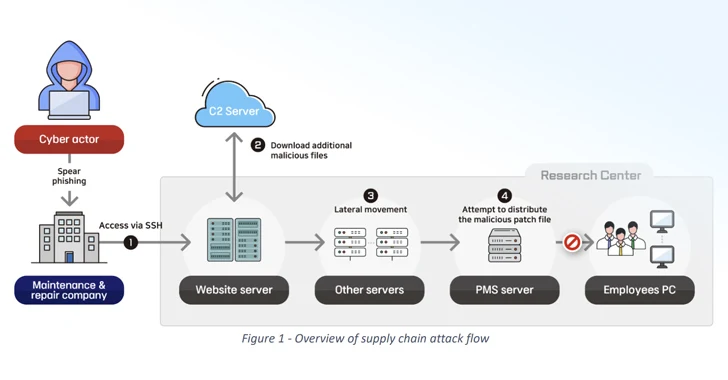
The second case involves an intrusion into a defense research center in late 2022 by executing a software supply chain attack against an unnamed company responsible for maintaining one of the research center’s web servers.
“The cyber attacker further infiltrated the research center by distributing remote-controlled malware via a patch management system (PMS) of the research center and stole various account information from corporate portals and email content,” BfV said and NIS.

The breach, carried out by another North Korea-based criminal actor, occurred in five phases:
- Hack Web Server Maintenance Company, Steal SSH Credentials, and Gain Remote Access to Research Center Server
- Download additional malicious tools using curl commands, including tunneling software and a Python-based downloader
- Perform lateral movements and loot employee account credentials
- Exploit stolen security officer account information to unsuccessfully deploy an update containing a trojan capable of uploading and downloading files, executing code, and gathering system information
- Persevere in the target environment by weaponizing a file upload vulnerability in the website to implement a web shell for remote access and send spear-phishing emails
“The actor avoided launching a direct attack against his target, which maintained a high level of security, but rather launched a first attack against its vendor, the maintenance and repair company,” the agencies explained. “This indicates that the actor took advantage of the relationship of trust between the two entities.”

The safety bulletin is the second published by BfV and NIS in as many years. In March 2023, the agencies warned of Kimsuky actors using rogue browser extensions to steal users’ Gmail inboxes. Kimsuky was sanctioned by the US government in November 2023.
The development comes as blockchain analytics firm Chainalysis revealed that the Lazarus Group has switched to using bitcoin mixer YoMix to launder stolen proceeds following the shutdown of Sinbad late last year, indicating their ability to adapt the own modus operandi in response to the actions of the police.
“Sinbad became the mixer of choice for North Korea-affiliated hackers in 2022, soon after the approval of Tornado Cash, which had previously been the go-to for these sophisticated cybercriminals,” the company said. “With Sinbad out of the picture, Bitcoin-based mixer YoMix acted as a replacement.”
The malicious activities are the work of a plethora of North Korean hacking units operating under the broad umbrella of Lazarus, known to be involved in a variety of hacking operations ranging from cyber espionage to cryptocurrency thefts, ransomware and chain attacks supply to achieve their strategic objectives. goals.