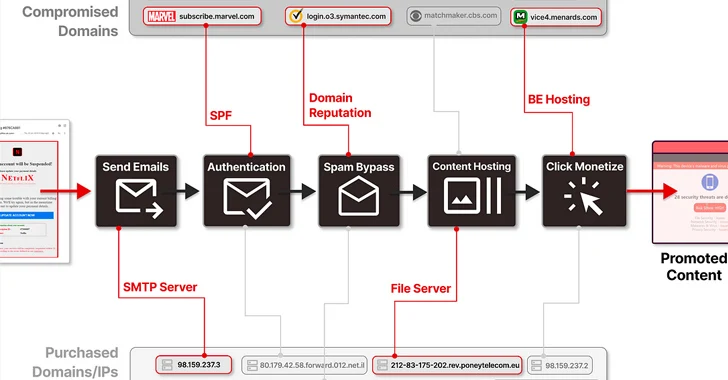
More than 8,000 domains and 13,000 subdomains belonging to legitimate brands and institutions were compromised as part of a sophisticated distribution architecture for spam proliferation and click monetization.
Guardio Labs is monitoring the coordinated malicious activity, which has been ongoing since at least September 2022, under the name SubdoMailing. The emails range from “counterfeit package delivery notices to outright phishing for account credentials.”
The Israeli security company attributed the campaign to a threat actor it reported ResurrecAdsknown for resurrecting dead domains or domains affiliated with big brands with the ultimate goal of manipulating the digital advertising ecosystem for nefarious gains.
“‘ResurrecAds’ operates a large infrastructure that includes a wide range of hosts, SMTP servers, IP addresses, and even private residential ISP connections, along with many additional proprietary domain names,” said security researchers Nati Tal and Oleg Zaytsev in a report shared with The Hacker News.
Specifically, the campaign “exploits the trust associated with these domains to circulate millions of spam and phishing emails every day, subtly using their credibility and stolen assets to bypass security measures.”
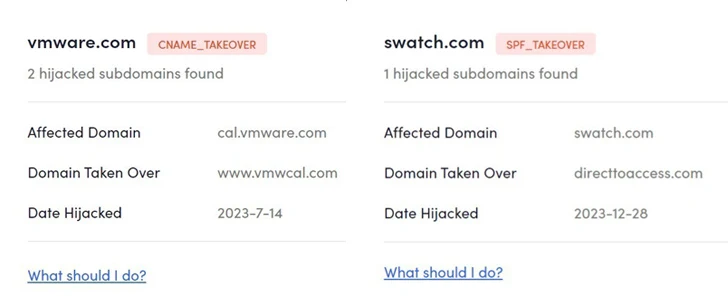
These subdomains belong to or are affiliated with major brands and organizations such as ACLU, eBay, Lacoste, Marvel, McAfee, MSN, Pearson, PwC, Swatch, Symantec, The Economist, UNICEF, and VMware, among others
The campaign stands out for its ability to bypass standard security blocks, with the entire body designed as an image to evade text-based spam filters, clicking on it initiates a series of redirects across different domains.

“These redirects control device type and geographic location, leading to content tailored to maximize profit,” the researchers explained.
“This could be anything from an annoying ad or affiliate link to more deceptive tactics like quiz scams, phishing sites, or even a malware download aimed at scamming you out of your money more directly.”
Another crucial aspect of these emails is that they are also able to bypass the Sender Policy Framework (SPF), an email authentication method designed to prevent spoofing by ensuring that a mail server is authorized to send emails for a given domain.
It’s not just about SPF, as emails also pass DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC) checks that help prevent messages from being marked as spam.
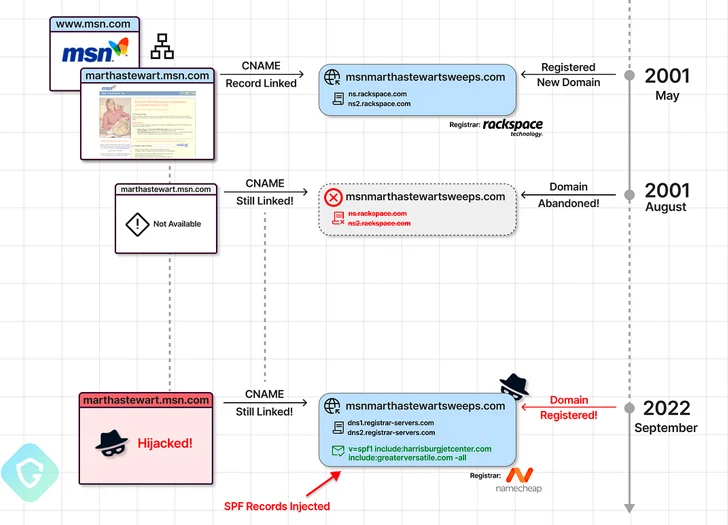
In one example of a deceptive cloud storage warning email highlighted by Guardio, the message originated from an SMTP server in Kiev, but was marked as sent from Return_UlKvw@marthastewart.msn.com.
A closer look at marthastewart.msn.com’s DNS record revealed that the subdomain is linked to another domain (msnmarthastewartsweeps[.]com) via a CNAME record, an aliasing technique that has previously been weaponized by ad tech companies to bypass third-party cookie blocking.
“This means that the subdomain inherits the entire behavior of msnmarthastewartsweeps[.]com, including its SPF policy,” the researchers said. “In this case, the actor can send emails to anyone he wants as if msn[.]com and their approved mailers sent those emails!”

It’s worth pointing out that both domains were legitimate and active for a short time in 2001, before being left in an abandoned state for 21 years. It wasn’t until September 2022 when msnmarthastewartsweeps[.]com was registered privately with Namecheap.
In others, the hijacking scheme involves threat actors systematically scanning long-forgotten subdomains with dangling CNAME records of abandoned domains and then registering them to take control of them.

CNAME takeover can also have serious consequences when such reputable subdomains are hijacked to host fake phishing landing pages designed to harvest user credentials. That said, there is no evidence that any of the hacked subdomains were used for this purpose.
Guardio said he has also seen cases where a known domain’s SPF DNS record contains abandoned domains associated with defunct email or marketing services, thus allowing attackers to take ownership of those domains, insert their IP addresses into the records and finally send emails on behalf of the primary domain name.
In an effort to counter the threat and dismantle the infrastructure, Guardio has made available a SubdoMailing Checker, a website that allows domain administrators and site owners to look for signs of compromise.
“This operation is meticulously designed to abuse these resources to distribute various malicious ‘advertisements’, with the aim of generating as many clicks as possible for these ‘ad network’ customers,” the researchers said.
“Armed with a vast collection of trusted and compromised domains, servers and IP addresses, this ad network deftly moves through the process of propagating malicious emails, seamlessly switching and jumping between its assets at will.”