
A “complexly designed” remote access trojan (RAT) called Xenon RAT has been made available on GitHub, making it available to other actors at no additional cost.
Written in C# and compatible with Windows 10 and Windows 11 operating systems, the open-source RAT comes with a “full set of features for remote system management,” according to its developer, who goes by the name moom825.
It includes a SOCKS5 reverse proxy and the ability to record audio in real time, as well as incorporating a hidden virtual network computing (hVNC) module along the lines of DarkVNC, which allows attackers to gain remote access to an infected computer.
“Xeno RAT is developed entirely from scratch, ensuring a unique and tailored approach to remote access tools,” says the developer in the project description. Another noteworthy aspect is that it has a builder that allows the creation of tailor-made variants of the malware.

It is worth noting that moom825 is also the developer of another C#-based RAT called DiscordRAT 2.0, which was distributed by threat actors inside a malicious npm package called node-hide-console-windows, as disclosed by ReversingLabs in October 2023.
Cybersecurity firm Cyfirma, in a report published last week, said it had observed the spread of Xeno RAT via the Discord content delivery network (CDN), highlighting once again how an increase in affordable malware and freely available is leading to an increase in campaigns using RAT.

“The main carrier in the form of a link file, disguised as a WhatsApp screenshot, acts as a downloader,” the company said. “The downloader downloads the ZIP archive from the Discord CDN, extracts it, and executes the next stage payload.”
The multi-step sequence leverages a technique called DLL sideloading to launch a malicious DLL, while simultaneously taking steps to establish persistence and evade scanning and detection.

The development comes as the AhnLab Security Intelligence Center (ASEC) revealed the use of a Gh0st RAT variant called Nood RAT that is used in attacks against Linux systems, allowing adversaries to collect sensitive information.
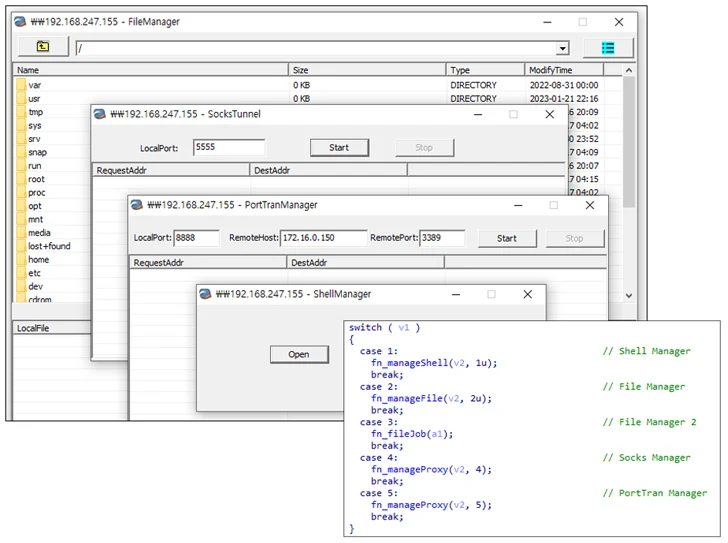
“Nood RAT is a backdoor malware that can receive commands from the C&C server to perform malicious activities such as downloading malicious files, stealing systems’ internal files, and executing commands,” ASEC said.
“Although simple in form, it features encryption functionality to avoid detection of network packets and can receive commands from threat actors to carry out multiple malicious activities.”