
The Android banking trojan known as He turned it on has broadened its focus to include Slovakia, Slovenia and the Czech Republic as part of a new campaign observed in November 2023.
“Some of the campaign droppers successfully exploited the Accessibility Service, despite Google Play’s enhanced detection and protection mechanisms,” ThreatFabric said in a report shared with The Hacker News.
“All droppers in this campaign demonstrated the ability to bypass the limited settings for the Accessibility Service in Android 13.” The campaign, in total, involves five droppers with more than 100,000 total installations.
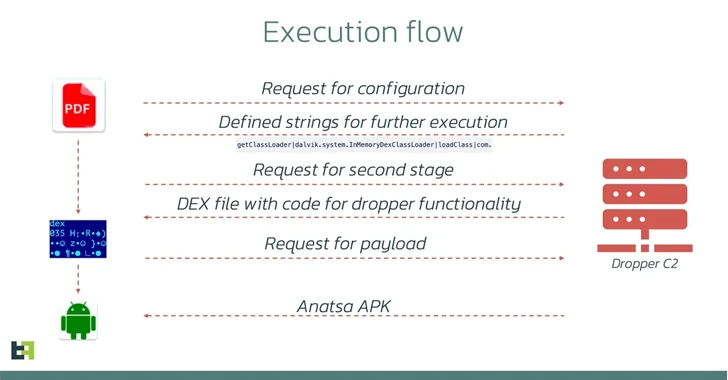
Also known by the names TeaBot and Toddler, Anatsa is known to be distributed under the guise of seemingly harmless apps on the Google Play Store. These apps, called droppers, facilitate the installation of malware by evading Google-imposed security measures that attempt to grant sensitive permissions.
In June 2023, Dutch mobile security firm revealed an Anatsa campaign targeting banking customers in the US, UK, Germany, Austria and Switzerland since at least March 2023 using dropper apps that were downloaded overall over 30,000 times on the Play Store.

Anatsa is equipped with features to gain full control over infected devices and perform actions on behalf of the victim. It can also steal credentials to initiate fraudulent transactions.
The latest iteration seen in November 2023 is no different as one of the droppers disguised itself as a phone cleaning app named “Phone Cleaner – File Explorer” (package name “com.volabs.androidcleaner”) and exploited a technique called versioning to introduce its malicious behavior.
Even though the app is no longer available for download from the official Android store, it can still be downloaded through other shady third-party sources.
According to statistics available on app intelligence platform AppBrain, the app is estimated to have been downloaded around 12,000 times during the period it was available on the Google Play Store between November 13 and November 27, when it had not been published.
“Initially, the app appeared harmless, free of malicious code, and its accessibility service was not involved in any malicious activity,” ThreatFabric researchers said.
“However, a week after its release, an update introduced malicious code. This update altered the functionality of AccessibilityService, allowing it to perform malicious actions such as automatically clicking buttons once it receives a configuration from [command-and-control] server.”
What makes the dropper notable is that its abuse of the accessibility service is tailored to Samsung devices, suggesting that it was designed to exclusively target phones made by the company at one point, although other droppers used in the campaign were found to be unrelated to the producer. .
Droppers are also able to bypass Android 13’s limited settings by mimicking the process used by marketplaces to install new applications without having access to accessibility service features disabled, as previously observed in the case of dropper services like SecuriDropper.

“These actors prefer attacks focused on specific regions rather than a global spread, periodically shifting their focus,” ThreatFabric said. “This targeted approach allows them to focus on a limited number of financial organizations, resulting in a large number of fraud cases in a short time.”
The development comes as Fortinet FortiGuard Labs detailed another campaign that deploys the SpyNote remote access trojan by imitating a legitimate Singapore-based cryptocurrency wallet service known as imToken to replace target wallet addresses with those controlled by actors and conduct illicit resource transfers.
“Like many Android malware today, this malware abuses the accessibility API,” said security researcher Axelle Apvrille. “This SpyNote example uses the Accessibility API to target popular crypto wallets.”