
A code-named Chinese-speaking threat actor Gold Factory has been attributed to the development of highly sophisticated banking Trojans, including previously undocumented iOS malware called GoldPickaxe that can collect identity documents, facial recognition data and intercept SMS.
“The GoldPickaxe family is available for both iOS and Android platforms,” Singapore-based Group-IB said in an extensive report shared with The Hacker News. “GoldFactory is believed to be a well-organized Chinese-speaking cybercrime group with close ties to Gigabud.”
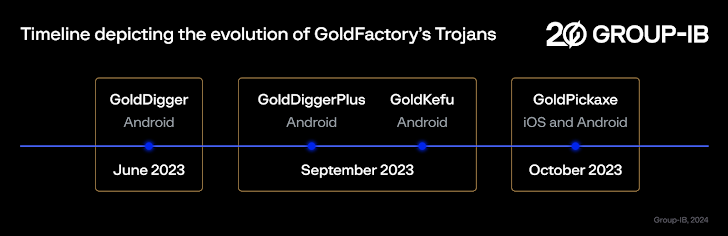
Active since at least mid-2023, GoldFactory is also responsible for another Android-based banking malware called GoldDigger and its enhanced variant GoldDiggerPlus, as well as GoldKefu, a Trojan embedded within GoldDiggerPlus.
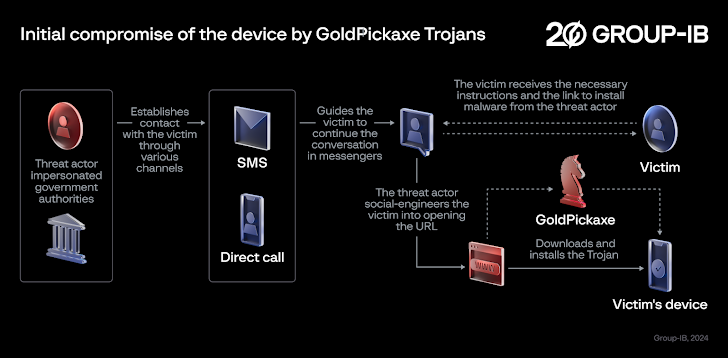
Social engineering campaigns distributing the malware have been found to target the Asia-Pacific region, particularly Thailand and Vietnam, masquerading as local banks and government organizations.
In these attacks, potential victims are sent smishing and phishing messages and guided to transfer the conversation to instant messaging apps such as LINE, before sending fake URLs leading to the implementation of GoldPickaxe on devices.
Some of these malicious apps targeting Android are hosted on fake websites that resemble Google Play Store pages or fake company websites to complete the installation process.

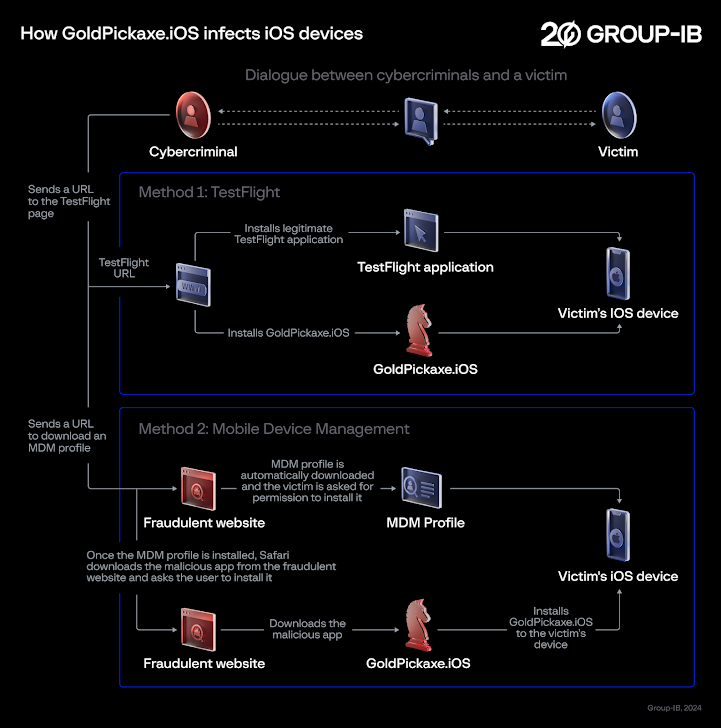
GoldPickaxe for iOS, however, uses a different distribution scheme, with later iterations leveraging Apple’s TestFlight platform and booby-trapped URLs that prompt users to download a Mobile Device Management (MDM) profile to grant complete control over iOS devices and install the rogue app.
Both of these propagation mechanisms were disclosed by Thailand Banking Sector CERT (TB-CERT) and Cyber Crime Investigation Bureau (CCIB) in November 2023, respectively.
GoldPickaxe’s sophistication is also evident in the fact that it is designed to bypass security measures imposed by Thailand that require users to confirm larger transactions using facial recognition to prevent fraud.
“GoldPickaxe asks the victim to record a video as a confirmation method in the fake application,” said security researchers Andrey Polovinkin and Sharmine Low. “The recorded video is then used as raw material for the creation of deepfake videos facilitated by face-swapping artificial intelligence services.”
Additionally, the Android and iOS versions of the malware are capable of collecting the victim’s identity documents and photos, intercepting incoming SMS messages and proxy traffic through the compromised device. GoldFactory perpetrators are suspected of using their devices to access the bank’s application and perform unauthorized fund transfers.
That said, the iOS variant features fewer features than its Android counterpart due to the closed nature of the iOS operating system and the relatively more stringent nature of iOS permissions.
The Android version, considered the evolutionary successor to GoldDiggerPlus, also presents itself as over 20 different applications from the Thai government, financial sector and utility companies to steal login credentials from these services. However, it is currently unclear what threat actors do with this information.
Another noteworthy aspect of the malware is its abuse of Android Accessibility Services to record keystrokes and extract content on the screen.

GoldDigger also shares code-level similarities with GoldPickaxe, although it is primarily designed to steal banking credentials, while the latter is more geared towards collecting personal information from victims. So far, no GoldDigger artifacts targeting iOS devices have been identified.
“The main feature of GoldDigger is that it targets over 50 applications of Vietnamese financial companies, including their package names in the trojan,” the researchers said. “Every time you open the targeted applications, the text displayed or written on the user interface, including passwords, as you enter them, will be saved.”
The basic version of GoldDigger, first discovered in June 2023 and still in circulation, has since paved the way for more updated variants, including GoldDiggerPlus, which comes embedded with another Trojan APK component called GoldKefu, to trigger harmful actions. .
GoldDiggerPlus is said to have emerged in September 2023, with GoldKefu posing as a popular Vietnamese messaging app to steal banking credentials associated with 10 financial institutions.

Goldkefu also integrates with the Agora Software Development Kit (SDK) to facilitate interactive voice and video calls and trick victims into contacting a fake banking customer service by sending fake alerts that induce a false sense of urgency by claiming that a transfer of funds at the rate by 3 million Thai baht were deposited into their accounts.
If anything, this development is a sign that the mobile malware landscape remains a lucrative market for cybercriminals seeking quick financial gains, even as they find ways to bypass the defensive measures erected by banks to counter such threats. It also demonstrates the dynamic and ever-evolving nature of social engineering schemes that aim to deliver malware to victims’ devices.
To mitigate the risks posed by GoldFactory and its mobile banking malware suite, you are strongly advised not to click on suspicious links, install apps from untrusted sites, as they are a common malware vector, and periodically review your granted permissions to apps, especially those that require Android accessibility services.
“GoldFactory is a resourceful team experienced in various tactics, including identity theft, accessibility keylogging, fake banking websites, fake bank alerts, fake call screens, identity and facial recognition data collection,” they said researchers. “The team includes separate development groups and operators dedicated to specific regions.”
“The group has well-defined processes and operational maturity and is constantly improving its toolset to align with the target environment, demonstrating high expertise in malware development.”