
The China-linked menacing actor known as Evasive panda has orchestrated both wateringhole and supply chain attacks against Tibetan users since at least September 2023.
The aim of the attacks is to deliver malicious downloaders for Windows and macOS that distribute a known backdoor called MgBot and a previously undocumented Windows implant known as Nightdoor.
The findings come from ESET, which says attackers compromised at least three websites to carry out watering-hole attacks, as well as a compromise of the supply chain of a Tibetan software company. The operation was discovered in January 2024.
Evasive Panda, active since 2012 and also known as Bronze Highland and Daggerfly, was previously revealed by the Slovakian cybersecurity firm in April 2023 to have targeted an international non-governmental organization (NGO) in mainland China with MgBot.

Another report from Broadcom-owned Symantec around the same time implicated the adversary in a cyber espionage campaign aimed at infiltrating telecommunications service providers in Africa since at least November 2022.
The latest round of cyber attacks involves the strategic compromise of the Kagyu International Monlam Trust website (“www.kagyumonlam[.]org”).
“The attackers inserted a script into the website that checks the potential victim’s IP address and, if it falls within one of the targeted address ranges, displays a fake error page to entice the user to download a certificate named ‘ fix’,” ESET researchers said.
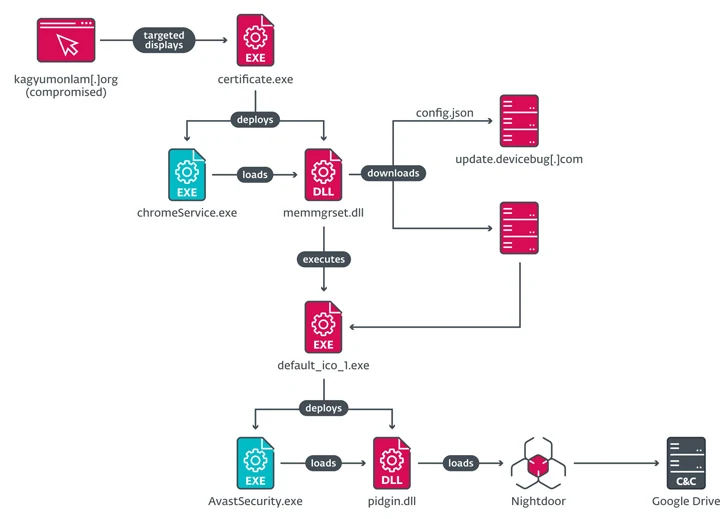
“This file is a malicious downloader that implements the next step in the chain of compromise.” IP address checks show the attack is specifically designed to target users in India, Taiwan, Hong Kong, Australia and the United States
Evasive Panda is suspected to have exploited the annual Kagyu Monlam Festival that took place in India between late January and February 2024 to target the Tibetan community in several countries and territories.
The executable, named “certificate.exe” on Windows and “certificate.pkg” on macOS, serves as a launchpad to load the Nightdoor implant, which, subsequently, abuses the Google Drive API for command and control (C2) .
Additionally, the campaign is known for infiltrating the website of an Indian software company (“monlamit[.]com”) and supply chain in order to distribute Windows and macOS installers containing Tibetan language translation software trojans. The compromise occurred in September 2023.

“The attackers also abused the same website and a Tibetan news site called Tibetpost – tibetpost[.]net – to host payloads obtained from malicious downloads, including two full backdoors for Windows and an unknown number of payloads for macOS,” the researchers noted.
The trojan-affected Windows installer, for its part, activates a sophisticated multi-step attack sequence to eliminate MgBot or Nightdoor, signs of which were detected as early as 2020.
The backdoor comes with features to collect system information, list of installed apps and running processes; generate a reverse shell, perform file operations and uninstall itself from the infected system.
“The attackers have deployed several downloaders, droppers and backdoors, including MgBot – used exclusively by Evasive Panda – and Nightdoor: the latest major addition to the group’s toolkit and which has been used to target several networks in Asia eastern,” ESET said.