
The infamous cybercrime syndicate known as FIN7 has been linked to a spear-phishing campaign targeting the US auto industry to deliver a known backdoor called Carbanak (aka Anunak).
“FIN7 identified company employees who worked in the IT department and had higher levels of administrative rights,” BlackBerry’s research and intelligence team said in a new article.
“They used the lure of a free IP scanning tool to execute their known Anunak backdoor and gain an initial foothold using local binaries, scripts and libraries (LOLBAS).”

FIN7, also known as Carbon Spider, Elbrus, Gold Niagara, ITG14, Sangria Tempest, is a well-known financially motivated electronic crime group that has a long track record of targeting a wide range of verticals to deliver malware capable of stealing information from point of sale (PoS) systems since 2012.
In recent years, the threat actor has shifted to conducting ransomware operations, distributing various strains such as Black Basta, Cl0p, DarkSide, and REvil. Two Ukrainian members of the group, Fedir Hladyr and Andrii Kolpakov, have so far been sentenced to prison in the United States.
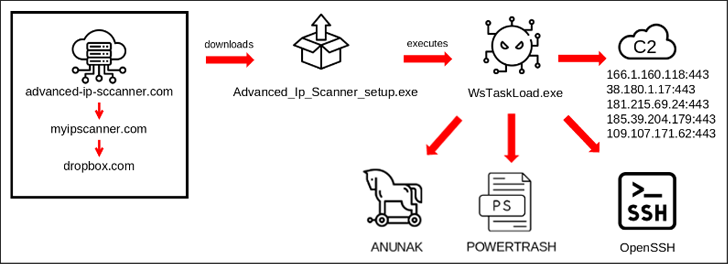
The latest campaign discovered by BlackBerry in late 2023 begins with a spear phishing email that incorporates an explosive link pointing to a fake site (“advanced-ip-sccanner[.]com”) disguised as Advanced IP Scanner.
“This fake site redirected to ‘myipscanner[.]com”, which in turn redirected to a Dropbox owned by the attacker who downloaded the malicious executable WsTaskLoad.exe onto the victim’s computer,” the Canadian cybersecurity firm said.

Binary, for his part, begins a multi-step process that ultimately leads to Carbanak’s execution. It is also designed to provide additional payloads such as POWERTRASH and establish persistence by installing OpenSSH for remote access.
It is currently unknown whether the threat actors were planning to deploy ransomware, as the infected system was detected early and removed from the network before it could reach the lateral movement stage.
Although the target of the attack was a “large multinational automotive manufacturer” based in the United States, BlackBerry said it found several similar malicious domains on the same provider, indicating it may be part of a larger campaign by FIN7.
To mitigate the risks posed by these threats, organizations are advised to be alert to phishing attempts, enable multi-factor authentication (MFA), keep all software and systems updated, and monitor for unusual login attempts.