
Ukraine’s Computer Emergency Response Team (CERT-UA) has warned that more than 2,000 computers in the country have been infected with a malware strain called DirtyMoe.
The agency attributed the campaign to a threat actor caller UAC-0027.
DirtyMoe, active since at least 2016, is capable of carrying out cryptojacking and distributed denial of service (DDoS) attacks. In March 2022, cybersecurity firm Avast revealed the malware’s ability to propagate as a worm by exploiting known security flaws.
The DDoS botnet is known to be delivered via another malware called Purple Fox or via fake MSI installer packages for popular software such as Telegram. Purple Fox also comes with a rootkit that allows threat actors to hide malware on the machine and make it difficult to detect and remove.

The exact initial entry vector used in the campaign against Ukraine is currently unknown. CERT-UA recommends that organizations keep their systems updated, apply network segmentation, and monitor network traffic for any anomalous activity.
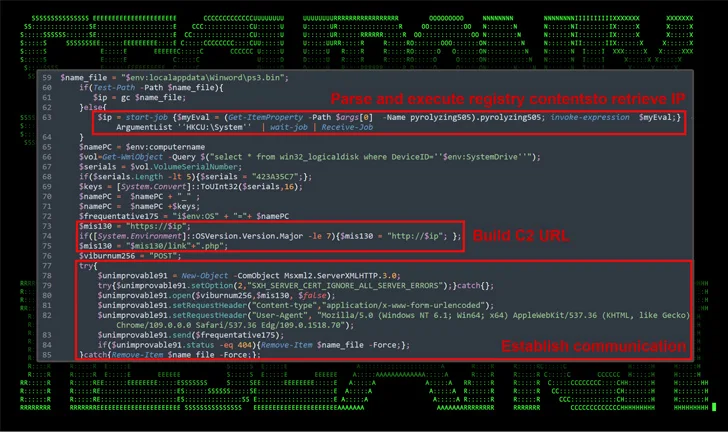
The disclosure comes as Securonix details an ongoing phishing campaign known as STEADY#URSA that targets Ukrainian military personnel with the aim of delivering a bespoke PowerShell backdoor called SUBTLE-PAWS.
“The exploitation chain is relatively simple: it involves the target running a malicious link file (.lnk) that loads and executes a new PowerShell backdoor payload code (found within another file contained in the same archive)” , security researchers Den Iuzvyk, Tim Peck and Oleg Kolesnikov said.
The attack is said to be related to a malicious actor known as Shuckworm, also known as Aqua Blizzard (formerly Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder. Active since at least 2013, it is believed to be part of the Russian Federal Security Service (FSB).
SUBTLE-PAWS, in addition to setting persistence on the host, uses Telegram’s blogging platform called Telegraph to retrieve command and control (C2) information, a technique previously identified as being associated with the adversary since early 2023, and can propagate through removable connected drives.

Gamaredon’s ability to spread via USB drives was also documented by Check Point in November 2023, who named the PowerShell-based USB worm LitterDrifter.
“The SUBTLE-PAWS backdoor uses advanced techniques to dynamically execute malicious payloads,” the researchers said.
“They store and retrieve PowerShell executable code from the Windows registry that can help evade traditional file-based detection methods. This approach also helps maintain persistence on the infected system, as the malware can restart after reboots or other interruptions.”