Fake installers for Adobe Acrobat Reader are used to distribute a new dubbed multi-purpose malware Byakugan.
The starting point of the attack is a PDF file written in Portuguese which, when opened, displays a blurry image and asks the victim to click on a link to download the Reader application to view its contents.
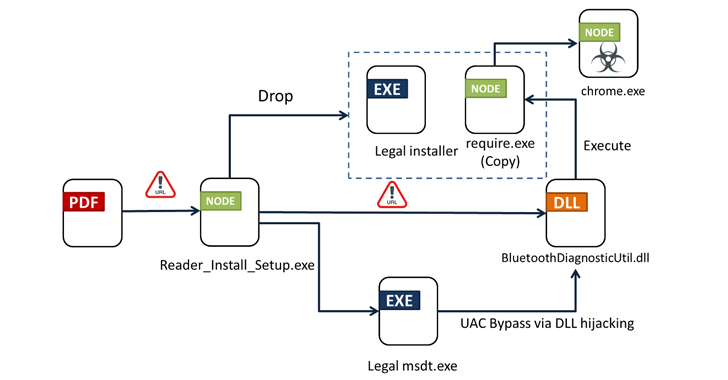
According to Fortinet FortiGuard Labs, clicking the URL displays an installer (“Reader_Install_Setup.exe”) that triggers the infection sequence. Details of the campaign were first disclosed last month by the AhnLab Security Intelligence Center (ASEC).
The attack chain leverages techniques such as DLL hijacking and Windows User Access Control (UAC) bypass to load a malicious dynamic link library (DLL) file named “BluetoothDiagnosticUtil.dll,” which, in turn, loads and releases the final payload. It also distributes a legitimate installer for a PDF reader like Wondershare PDFelement.
The binary is equipped to collect and exfiltrate system metadata on a command and control (C2) server and release the main module (“chrome.exe”) from a different server that also acts as a C2 to receive files and commands.
“Byakugan is node.js-based malware inserted into its executable by pkg,” said security researcher Pei Han Liao. “In addition to the main script, there are several libraries corresponding to the functionality.”

This includes setting persistence, monitoring the victim’s desktop using OBS Studio, taking screenshots, downloading cryptocurrency miners, logging keystrokes, enumerating and uploading files, and capturing of data stored in web browsers.
“There is a growing trend to use both clean and malicious components in malware, and Byakugan is no exception,” Fortinet said. “This approach increases the amount of noise generated during the analysis, making accurate detections more difficult.”
The disclosure comes as ASEC revealed a new campaign propagating the information stealer Rhadamanthys in the guise of an installer for groupware.
“The threat actor created a fake website to resemble the original website and exposed the site to users using the advertising feature in search engines,” the South Korean cybersecurity firm said. “The malware in distribution uses the indirect system call technique to hide from the eyes of security solutions.”
It also follows the discovery that a manipulated version of Notepad++ is being used by unidentified threat actors to propagate the WikiLoader (also known as WailingCrab) malware.