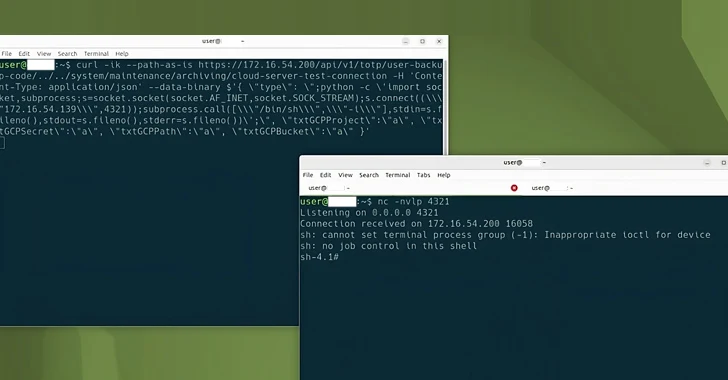
The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory against cyber threat actors exploiting known security flaws in the Ivanti Connect Secure and Ivanti Policy Secure gateways, highlighting that the Integrity Checker Tool (ICT) can be tricked into providing a false sense of security.
“Ivanti ICT is insufficient to detect compromises and that a cyber threat actor may be able to achieve root-level persistence despite performing a factory reset,” the agencies said.
To date, Ivanti has disclosed five security vulnerabilities affecting its products since January 10, 2024, of which four have been actively exploited by multiple threat actors to distribute malware:
- CVE-2023-46805 (CVSS Score: 8.2) – Authentication bypass vulnerability in web component
- CVE-2024-21887 (CVSS Score: 9.1) – Command injection vulnerability in web component
- CVE-2024-21888 (CVSS Score: 8.8) – Privilege escalation vulnerability in web component
- CVE-2024-21893 (CVSS Score: 8.2) – SSRF vulnerability in SAML component
- CVE-2024-22024 (CVSS Score: 8.3) – XXE vulnerability in SAML component
Mandiant, in an analysis published this week, described how an encrypted version of the malware known as BUSHWALK is placed in an ICT-excluded directory at /data/runtime/cockpit/diskAnalysis.

Directory exclusions were also previously highlighted by Eclypsium this month, stating that the tool skips a dozen directories from scanning, thus allowing an attacker to leave backdoors in one of these paths and still pass the integrity check.
“The safest course of action for network defenders is to assume that a sophisticated threat actor can implement rootkit-level persistence on a device that has been reset and remain dormant for an arbitrary period of time,” agencies of Australia , Canada, New Zealand and the United Kingdom. , and the United States said.
They also urged organizations to “consider the significant risk of adversarial access and persistence on Ivanti Connect Secure and Ivanti Policy Secure gateways when determining whether to continue using these devices in an enterprise environment.”
Ivanti, in response to the advisory, said it is not aware of any cases of successful persistence of threat actors following the implementation of security updates and factory resets. He is also releasing a new version of ICT which he says “provides additional visibility into the customer appliance and all files on the system.”