
Employment agencies and retail companies located primarily in the Asia-Pacific (APAC) region have been targeted by a previously undocumented threat actor known as ResumeLooters since the beginning of 2023 with the aim of stealing sensitive data.
Singapore-based Group-IB said the hacking team’s activities were geared towards job search platforms and resume theft, with as many as 65 websites compromised between November 2023 and December 2023.
The stolen files are estimated to contain 2,188,444 user data records, of which 510,259 were taken from job search websites. There are over two million unique email addresses in the dataset.
“Using SQL injection attacks against websites, the threat actor attempts to steal user databases which may include names, phone numbers, emails and DoBs, as well as information about job seekers’ experience, history work and other sensitive personal data,” security researcher Nikita Rostovcev said in a report shared with The Hacker News.

“The stolen data is then offered for sale by the threat actor in Telegram channels.”
Group-IB said it also discovered evidence of cross-site scripting (XSS) infections on at least four legitimate job search websites designed to load malicious scripts responsible for displaying phishing pages capable of harvesting administrator credentials.
ResumeLooters is the second group after GambleForce to stage SQL injection attacks in the APAC region since late December 2023.
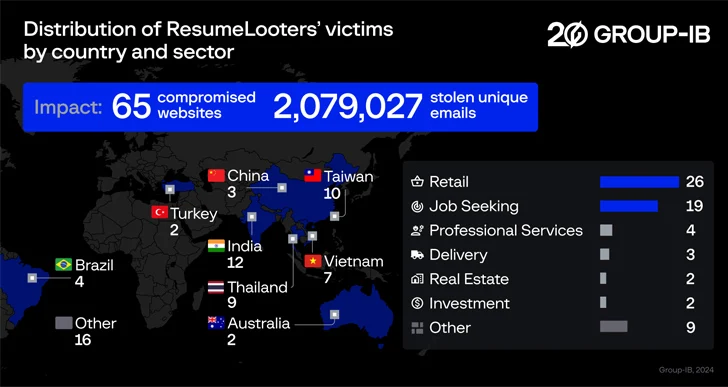
Most of the compromised websites are based in India, Taiwan, Thailand, Vietnam, China, Australia, and Turkey, although compromises have also been reported from Brazil, the United States, Turkey, Russia, Mexico, and Italy.
ResumeLooters’ modus operandi involves using the open source sqlmap tool to perform SQL injection attacks and dropping and executing additional payloads such as the BeEF (short for Browser Exploitation Framework) penetration testing tool and rogue JavaScript code designed to harvest data sensitive and redirect users to credential collection pages.
The cybersecurity firm’s analysis of the threat actor’s infrastructure reveals the presence of other tools such as Metasploit, dirsearch, and xray, along with a folder hosting the stolen data.

The campaign appears to be financially motivated, as ResumeLooters created two Telegram channels called Penetration Data Center and GDS Ali last year to sell the information.
“ResumeLooters is yet another example of how much damage can be done with just a handful of tools available to the public,” Rostovcev said. “These attacks are fueled by poor security and poor database and website management practices.”
“It is surprising to see how some of the older but remarkably effective SQL attacks continue to prevail in the region. However, the tenacity of the ResumeLooters group stands out as they experiment with different methods to exploit vulnerabilities, including XSS attacks.”