
Human rights activists in Morocco and the Western Sahara region are the targets of a new threat actor using phishing attacks to trick victims into installing fake Android apps and providing credential harvesting pages for Windows users.
Cisco Talos is monitoring the business cluster under the name Starry Addaxdescribing it primarily as a choice of activists associated with the Sahrawi Arab Democratic Republic (SADR).
The infrastructure of Starry Addax – ondroid[.]site and ondroid[.]store – is designed to target both Android and Windows users, with the latter involving fake websites masquerading as login pages for popular social media websites.

The adversary, believed to be active since January 2024, is known to send spear phishing emails to targets, urging recipients to install the Sahara Press Service mobile app or relevant lure related to the region.
Depending on which operating system the request comes from, the target is served a malicious APK impersonating Sahara Press Service or redirected to a social media login page to harvest their credentials.
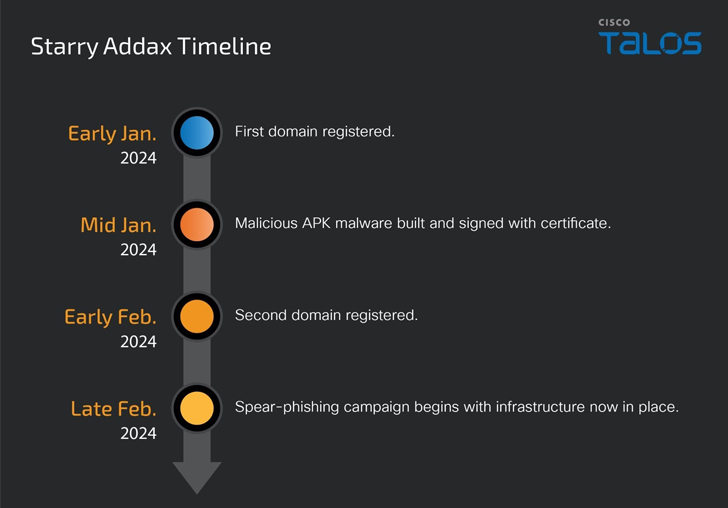
The new Android malware, called FlexStarling, is versatile and equipped to deliver additional malware components and steal sensitive information from infected devices.
Once installed, it requires the victim to grant extended permissions that allow the malware to perform nefarious actions, including retrieving commands to execute from a Firebase-based command and control (C2), a sign that the threat actor is trying to do so . flying under the radar.
“Campaigns like this that target high-value individuals usually intend to remain silent on the device for an extended period,” Talos said.

“All components, from malware to operational infrastructure, appear to be tailor-made for this specific campaign, indicating a strong focus on stealth and conducting activities under the radar.”
The development comes in the context of the emergence of a new commercial Android remote access trojan (RAT) known as Oxicorate which is offered for sale with different information gathering capabilities.