
In today’s digital business environment, dominated by SaaS applications, organizations are increasingly dependent on third-party vendors for essential cloud services and software solutions. As more vendors and services are added to the mix, the complexity and potential vulnerabilities within the SaaS supply chain rapidly increase. That’s why effective vendor risk management (VRM) is a critical strategy for identifying, assessing and mitigating risks to protect organizational assets and data integrity.
Meanwhile, common approaches to vendor risk assessment are too slow and static for the modern world of SaaS. Most organizations have simply adapted their legacy evaluation techniques for on-premise software to apply to SaaS vendors. This not only creates huge bottlenecks, but also causes organizations to inadvertently accept excessive risks. To effectively adapt to the realities of modern work, two main aspects need to change: the timing of the initial assessment must shorten, and iterative assessments over time must increase.
How Nudge Security can help you
To address the need for a new, more flexible model, Nudge Security has created security profiles for more than 97,000 SaaS apps, giving customers (and trial users) access to robust, actionable security context and insights into AI-based risks. Each security profile includes an app description, key vendor details, security certifications, breach history, data location, links to security programs, supported authentication methods, and SaaS supply chain details. Using the information in these profiles, you can:
- Speed up vendor security reviews with “one stop shopping” for key details
- Share a list of approved questions with employees
- Speed up supplier evaluations for new technology purchases
- Get an alert when your SaaS vendors or those in your digital supply chain experience breaches
Let’s take a look at how Nudge Security helps you at every stage of vendor risk management.
1. View security profiles for all SaaS apps used by anyone in your organization
Nudge Security detects all SaaS accounts created by anyone in your organization within minutes of starting a free trial and requires only one integration point: read-only API access to your Microsoft 365 or Google Workspace email provider. There’s no need for endpoint agents, network proxies, browser plug-ins, app integrations, or other complicated deployment steps. Find out more about how it works here.
For each of the apps used in your organization, Nudge Security provides a vendor security profile that includes many of the details needed to conduct a vendor security review. Details include app category and description, headquarters, legal terms, data hosting details, and more. You can also view information about the vendor’s security program, breach history, compliance certifications, and links to the vendor’s public support for security efforts.
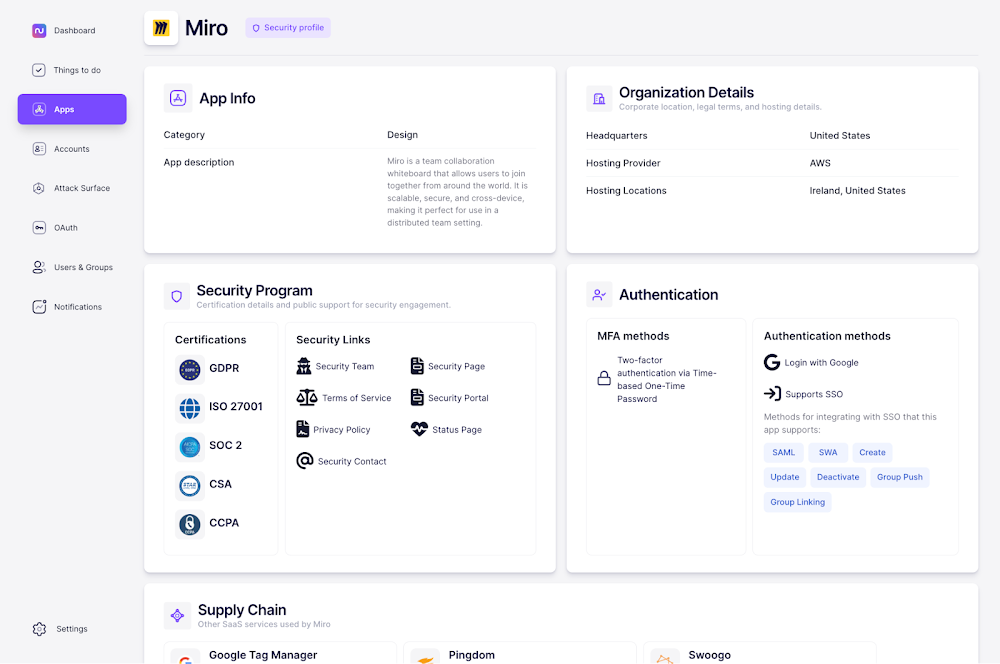
2. Provide employees with a list of approved applications
After reviewing an app, you can assign a status such as “Approved,” “Acceptable,” or “Unacceptable” to indicate whether use should be allowed. For any app deemed “unacceptable,” you can trigger automatic reminders in response to new accounts to redirect the user to a similar approved app or ask for context as to why you need to use that particular app.
Additionally, Nudge Security makes it easy to create and share an app directory with employees, so everyone in your organization can see a complete list of approved applications that meet the appropriate security and compliance standards. Employees can review the list by category and submit access requests that are addressed directly to the technical owner of each application, whether or not that person resides within central IT. This eliminates the need for IT to act as an “event relay” between users and app owners, while maintaining centralized visibility and governance.
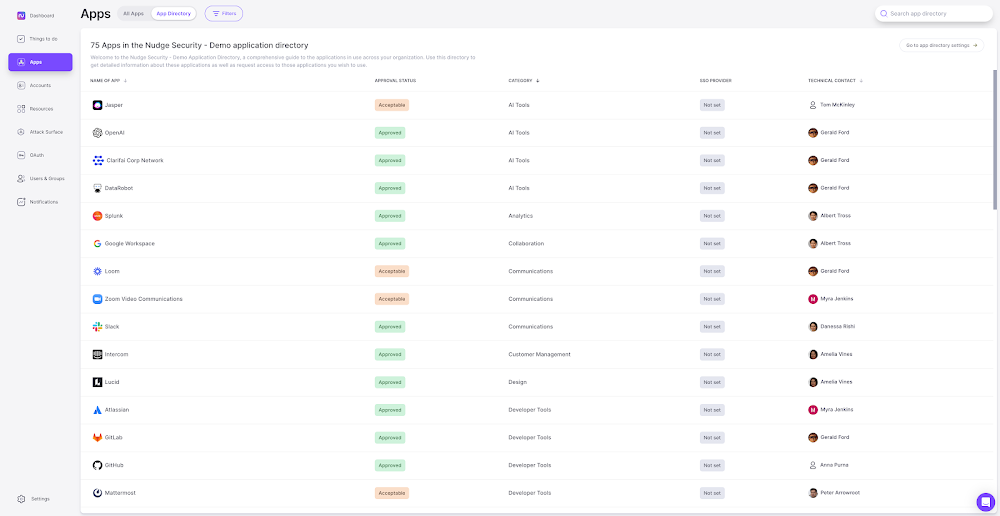
3. Accelerate supplier evaluations for purchases of new technologies
For apps your organization doesn’t already use, Nudge Security still gives you access to vendor security profiles to help you evaluate apps more quickly. You can search for any app and the search results will indicate whether it is currently used in your organization or not.
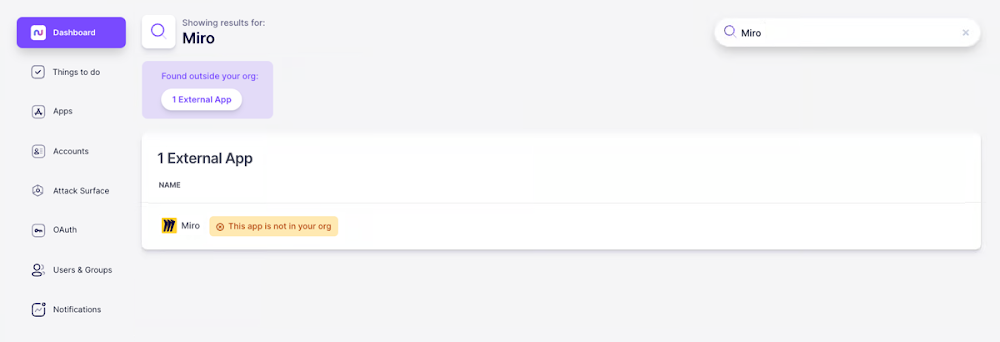
From there, you can access the same vendor security profile details described above and update the app’s status to indicate whether it is “Approved,” “Acceptable,” or “Unacceptable.” Any app deemed “Approved” can be automatically added to the app directory, and you can choose whether to include apps with an “Acceptable” status in the app directory as well.
4. Analyze the SaaS supply chain for each application.
Nudge Security provides critical capabilities to help you manage SaaS security, including visibility into your SaaS supply chain. This information is available within each SaaS security profile, and you can also click on each supply chain app to view the associated security profile.
Understanding an app’s SaaS supply chain can help you assess and manage data security risks and ensure compliance with regulatory standards.
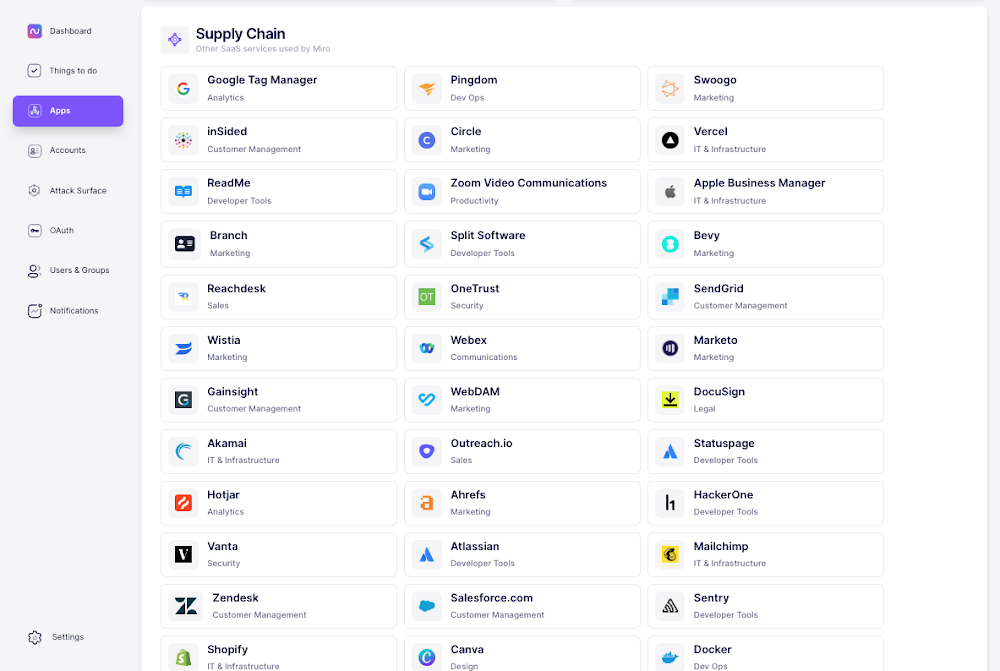
5. Get alerts for breaches affecting your SaaS providers
When an app in use in your organization suffers a data breach, it can put your organization’s security at risk. Nudge Security alerts you when apps used by your employees experience a data breach or apps in their supply chains.
Within each security profile you can see an overview of the app’s violation history or a green thumbs up if there are no known violations.
When an app you use or one in your digital supply chain is affected by a breach, you’ll receive a notification like the one below so you can take appropriate actions to assess and mitigate any potential impacts.

Accelerate supplier risk assessments with Nudge Security
With Nudge Security’s patented SaaS detection method, an unmatched database of vendor security profiles and automated workflows, you can effectively manage third-party risks while strengthening your organization’s SaaS security posture.
Start your 14-day free trial now