
Processing alerts quickly and efficiently is the cornerstone of the role of a Security Operations Center (SOC) professional. Threat intelligence platforms can significantly improve their ability to do this. Let’s find out what these platforms are and how they can empower analysts.
The challenge: alert overload
The modern SOC faces a relentless barrage of security alerts generated by SIEM and EDR. Analyzing these alerts takes time and resources. Analyzing a potential threat often requires searching multiple sources before finding conclusive evidence to verify whether it poses a real risk. This process is further hindered by the frustration of spending precious time searching for artifacts that ultimately turn out to be false positives.
As a result, a significant portion of these events remain uninvestigated. This highlights a crucial challenge: finding the necessary information related to different indicators quickly and accurately. Threat data platforms offer a solution. These platforms allow you to search for any suspicious URL, IP or other indicator and receive immediate information about the potential risk. One such platform is Threat Intelligence Lookup by ANY.RUN.
Threat intelligence platforms to the rescue
Specialized platforms for SOC investigations leverage their own databases of threat data, aggregated from multiple sources. Take, for example, ANY.RUN’s Threat Intelligence Lookup (TI Lookup). This platform collects indicators of compromise (IOCs) from millions of interactive analysis sessions (activities) conducted within the ANY.RUN sandbox.
The platform offers an additional dimension of threat data: process logs, registry and network activity, command line contents, and other system information generated during sandbox analysis sessions. Users can then search for relevant details in these fields.
Benefits of Threat Intelligence Platforms
Deeper visibility into threats
Instead of relying on scattered data sources, such platforms offer a single point of access for searching IOCs across various data points. This includes URLs, file hashes, IP addresses, logged events, command lines, and logs, allowing for more comprehensive threat identification and investigation.
Faster alert investigations
When a security incident occurs, time is of the essence. TI platforms help quickly gather relevant threat intelligence data, enabling a deeper understanding of the nature of the attack, the systems affected and the extent of the compromise. This can significantly speed up and improve response efforts.
Proactive threat hunting
Threat intelligence platforms allow teams to actively search for known IOCs associated with specific malware families. This proactive approach can help uncover hidden threats before they turn into serious incidents.
They may provide access to data that could reveal potential vulnerabilities associated with known threats. This information can provide useful information for risk assessment and help organizations prioritize security efforts based on the most pressing dangers.
Threat analysis and decision making
With detailed information about malware behavior, teams can more accurately analyze threats and make informed decisions about containment, remediation, and future preventative measures. This continuous learning cycle strengthens the overall security posture and competence of the team.
Threat Intelligence Platform query examples
Search with individual indicators

Imagine that you suspect that a compromised system within your network is downloading malicious files. You identify a specific IP address as a potential source and decide to investigate further. Enter the IP address into the search bar of a threat intelligence platform. Immediately, the platform flags the address as malicious and linked to Remcos malware, offering information about domains, ports and even files associated with this IP.
It also provides access to the analysis sessions in which this IP address was involved and lists the tactics, techniques and procedures (TTPs) used by the malware in these sessions.

You can study each session in detail by simply clicking on it. The system will take you to the session page in the ANY.RUN sandbox, where you can explore all processes, connections, and log activity, as well as collect malware configuration and IOCs, or download a full threat report.
Flexible wildcard search
Another useful feature of threat intelligence platforms like TI Lookup is the ability to send wildcard and combined queries.
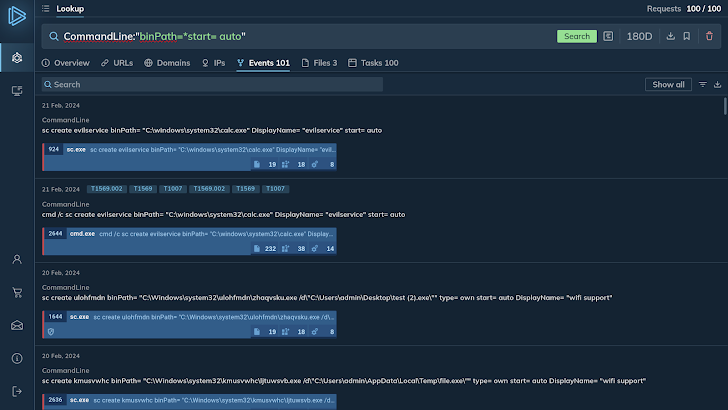
For example, the query “binPath=*start= auto” uses the asterisk wildcard character and searches for any command line with “binPath=” followed by any character ending with “start= auto”.
The platform returns a hundred sessions in which the same fragment appeared. A closer examination of the search results indicates that this specific command line artifact is characteristic of the Tofsee malware.
Combined search requests
Another option for conducting an investigation is to pool all available indicators and send them to the threat intelligence platform to identify all cases where these criteria appear collectively.
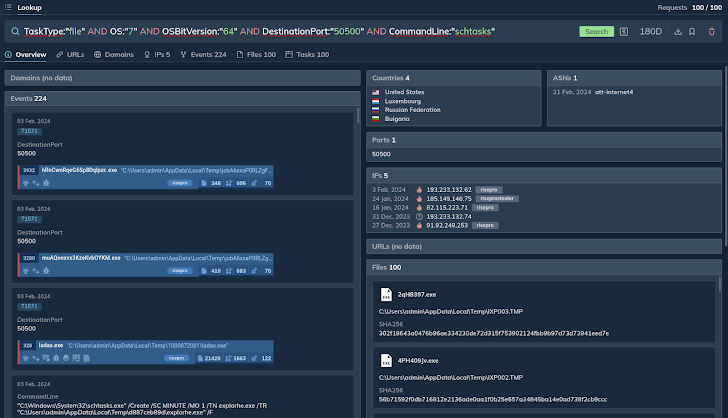
For example, you can construct a query that searches for all tasks (sessions) classified as “files”, running on Windows 7, with a 64-bit operating system, connecting to port 50500, and containing the string “schtasks” in the command line.
The platform then identifies numerous sessions that meet the specified criteria and also provides a list of IPs tagged with “RisePro”, highlighting the malware responsible.
Try searching for threat information
ANY.RUN’s Threat Intelligence Lookup lets you investigate threats with precision. Analyze processes, files, network activity and more. Refine your search with over 30 fields, including IPs, domains, logged events, and MITER techniques. Combine parameters for a holistic understanding. Use wildcard queries to expand your reach.
Request a trial to receive 50 free requests to explore the platform.