
A security flaw affecting the Lighttpd web server used in baseboard management controllers (BMCs) has not been fixed by device vendors such as Intel and Lenovo, new findings from Binarly reveal.
Although the original flaw was discovered and patched by Lighttpd maintainers in August 2018 with version 1.4.51, the lack of a CVE identifier or warning meant it was overlooked by AMI MegaRAC BMC developers, ultimately ending up in products made by Intel and Lenovo.
Lighttpd (pronounced “Lighty”) is high-performance, open-source web server software designed for speed, security, and flexibility, optimized for high-performance environments without consuming a lot of system resources.
The silent fix for Lighttpd concerns an out-of-bounds read vulnerability that could be exploited to exfiltrate sensitive data, such as process memory addresses, thus allowing threat actors to bypass crucial security mechanisms such as address space layout randomization (ASLR).

“The absence of timely and important information about security fixes prevents proper management of these fixes in both the firmware and software supply chains,” the firmware security company said.
The defects are described below:
- Read out of bounds in Lighttpd 1.4.45 used in Intel M70KLP series firmware
- Read out of bounds in Lighttpd 1.4.35 used in Lenovo BMC firmware
- Out of bounds read in Lighttpd before 1.4.51
Intel and Lenovo have decided not to address the issue as products incorporating the vulnerable version of Lighttpd have reached end-of-life (EoL) status and are no longer eligible for security updates, effectively turning it into a bug forever.
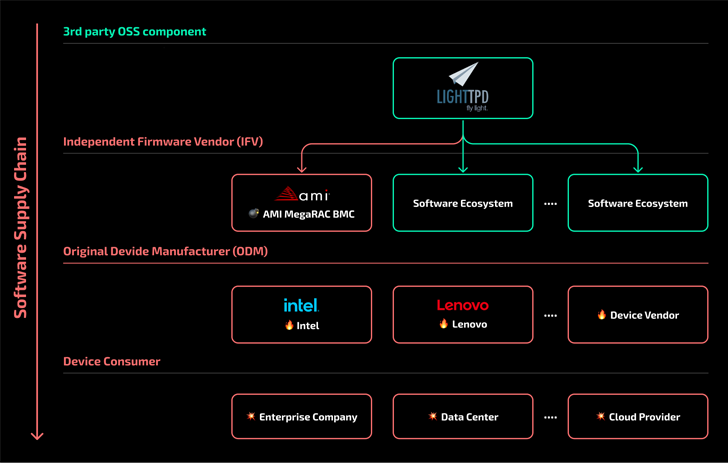
The policy highlights how the presence of obsolete third-party components in the latest firmware version can cross the supply chain and pose unintended security risks to end users.
“This is another vulnerability that will remain unresolved forever in some products and will present a high-impact risk to the industry for a long time,” Binarly added.