Conflicts in the Middle East, Ukraine, and other areas of simmering geopolitical tensions have made political experts the latest target of cyber operations conducted by state-sponsored groups.
An Iran-linked group – known as Charming Kitten, CharmingCypress and APT42 – recently targeted experts on Middle East politics in the region, the US and Europe, using a fake webinar platform to compromise its targeted victims, the Volexity incident response services reads a notice published this month.
Charming Kitten is well known for its extensive social engineering tactics, including slow-moving social engineering attacks against think tanks and journalists to gather political information, the company said.
The group often tricks targets into installing Trojan-rigged VPN applications to gain access to the fake webinar platform and other sites, resulting in the installation of malware. Overall, the group has embraced the long game of trust, says Steven Adair, co-founder and president of Volexity.
“I don’t know if this is necessarily sophisticated and advanced, but it requires a lot of effort,” he says. “It’s more advanced and more sophisticated than the average attack by a significant margin. It’s a level of commitment and dedication…definitely different and unusual…to put that much effort into such a specific set of attacks.”
Geopolitical experts in the crosshairs
Political pundits are often targeted by nation-state groups. THE ColdRiver group linked to Russia, for example, has targeted non-governmental organizations, military officers, and other experts who use social engineering to gain the victim’s trust and then use a malicious link or malware. In Jordan, targeted exploitation – reportedly by government agencies – used the Pegasus spyware program developed by the NSO Group and targeted at journalists, digital rights lawyers and other policy experts.
Other companies have also described Charming Kitten/CharmingCypress’ tactics. In a January notice, Microsoft warned that the group, which it calls Mint Sandstorm, had targeted journalists, researchers, professors and other experts covering political and security topics of interest to the Iranian government.
“The operators associated with this subset of Mint Sandstorm are patient, highly trained social engineers whose business activity lacks many of the features that allow users to quickly identify phishing emails,” Microsoft said. “In some cases in this campaign, this subgroup also used legitimate but compromised accounts to send phishing lures.”
The group has been active since at least 2013 strong ties with the Islamic Revolutionary Guard Corps (IRGC)and has not been directly involved in the cyber-operational aspect of the conflict between Israel and Hamas, according to cybersecurity firm CrowdStrike.
“Unlike the Russia-Ukraine war, where known cyber operations directly contributed to the conflict, individuals involved in the Israel-Hamas conflict did not directly contribute to Hamas military operations against Israel,” the company said in its “2024” report Global Threat Report” published on February 21.
Build a relationship over time
These attacks reportedly usually begin with spear-phishing and end with a malware combination delivered to the target’s system a warning from Volexity, which calls the group CharmingCypress. In September and October 2023, CharmingCypress used a series of typo-riddled domains (addresses similar to legitimate domains) to pose as officials from the International Institute of Iranian Studies (IIIS) to invite political experts to a webinar. The initial email demonstrated CharmingCypress’s slow and slow approach, avoiding any malicious links or attachments and inviting the targeted professional to get in touch through other communication channels, such as WhatsApp and Signal.
Using in-depth spearphishing, CharmingCypress aims to convince policy experts to install malware. Source: Volexità
Attacks target Middle Eastern political experts around the world, and Volexity has found the majority of attacks against European and U.S. professionals, Adair says.
“They’re pretty aggressive,” he says. “They also create entire email chains or a phishing scenario where they are looking for comments and there are other people – maybe three, four or five people in that email thread with the exception of the target – who are definitely trying to build a relationship.”
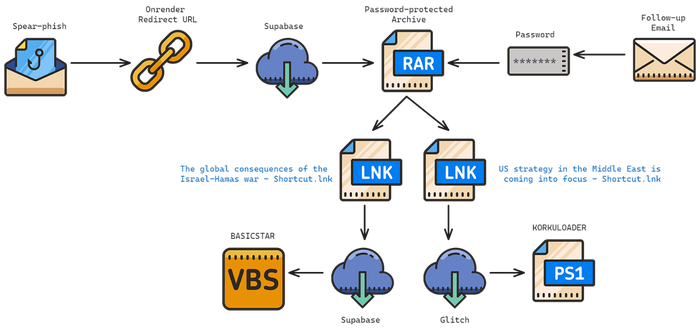
The long con eventually delivers a payload. Volexity has identified five different malware families associated with the threat. The PowerLess backdoor is installed by the Windows version of the malware-laden VPN (Virtual Private Network) application, which uses PowerShell to allow file transfer and execution, as well as targeting specific data on the system, logging keystrokes and take screenshots. A macOS version of the malware is called NokNok, while a separate malware chain using a RAR archive and an LNK exploit leads to a backdoor called Basicstar.
Defense becomes more difficult
The group’s approach to social engineering certainly embodies the “persistence” element of the Advanced Persistent Threat (APT). Volexity sees a “constant barrage” of attacks, so policy experts need to become even more suspicious of cold leads, Adair says.
Doing so will be difficult, as many policy experts are academics in constant contact with students or members of the public and are not used to being strict with their contacts, he says. Yet they should absolutely think before opening documents or entering credentials on a site reached via an unknown link.
“Ultimately, they have to get the person to click something or open something, which, if I want you to review a document or something, means… being very wary of links and files,” Adair says . “If I were to enter my credentials at any time, or authorize anything, that should be a big red flag. Likewise, if I’m asked to download something, that should be a big red flag.”
Additionally, policy experts need to understand that CharmingCypress will continue to target them even if its attempts fail, Volexity said.
“This threat actor is heavily engaged in conducting surveillance on its targets in order to determine how best to manipulate them and distribute malware,” the company said in its advisory. “Furthermore, few other threat actors have consistently churned out as many campaigns as CharmingCypress, dedicating human operators to support their ongoing efforts.”