
He called a financially motivated threat actor Goblin Magnet is rapidly adopting day-old security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing services and deploy malware onto compromised hosts.
“The hallmark of the Magnet Goblin criminal group is its ability to rapidly exploit newly disclosed vulnerabilities, particularly by targeting public-facing servers and edge devices,” Check Point said.
“In some cases, deployment of exploits occurs within 1 day after a [proof-of-concept] is published, significantly increasing the threat level posed by this actor.”

The adversary’s attacks leveraged unpatched Ivanti Connect Secure VPN, Magento, Qlik Sense, and possibly Apache ActiveMQ servers as the initial infection vector to gain unauthorized access. The group is said to have been active since at least January 2022.
A successful exploitation is followed by the implementation of a cross-platform remote access trojan (RAT) called Nerbian RAT, which was first revealed by Proofpoint in May 2022, as well as its simplified variant called MiniNerbian. The use of the Linux version of Nerbian RAT was previously highlighted by Darktrace.
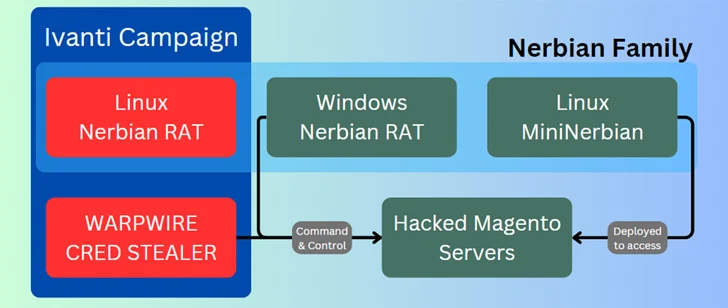
Both strains allow the execution of arbitrary commands received from a command and control (C2) server and the exfiltration of the results supported on it.
Some of the other tools used by Magnet Goblin include the JavaScript credential stealer WARPWIRE, the Go-based tunneling software known as Ligolo, and legitimate remote desktop offerings like AnyDesk and ScreenConnect.

“Magnet Goblin, whose campaigns appear to be financially motivated, has rapidly adopted 1-day vulnerabilities to deliver its own custom Linux malware, Nerbian RAT and MiniNerbian,” the company said.
“These tools have been operating under the radar as they mostly reside on edge devices. This is part of an ongoing trend for threat actors to target areas that have until now been left unprotected.”