
Dubbed a previously undocumented threat actor STARTING WINE has been observed targeting officials in European countries with Indian diplomatic missions using a new backdoor called WINE CHARGER.
The adversary, according to a report by Zscaler ThreatLabz, used a PDF file in emails purportedly from India’s ambassador, inviting diplomatic staff to a wine tasting event on February 2, 2024.

The PDF document was uploaded to VirusTotal from Latvia on January 30, 2024. That said, there is evidence to suggest that this campaign may have been active since at least July 6, 2023, thanks to the discovery of another similar PDF file uploaded from the same country.
“The attack is characterized by the very low volume and advanced tactics, techniques and procedures (TTPs) employed in the malware and command and control (C2) infrastructure,” said security researchers Sudeep Singh and Roy Tay.
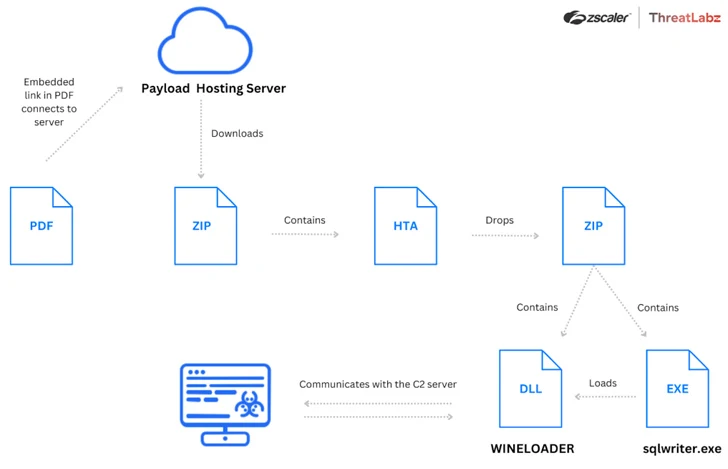
At the heart of the new attack is the PDF file that is embedded with a malicious link that disguises itself as a questionnaire, inviting recipients to fill it out to participate. Clicking the link takes you to an HTML application (“wine.hta”) that contains obfuscated JavaScript code to retrieve an encoded ZIP archive containing WINELOADER from the same domain.
The malware has a core module designed to execute modules from the C2 server, insert itself into another dynamic link library (DLL), and update the sleep interval between beacon requests.

A notable aspect of cyber incursions is the use of compromised websites for C2 and the hosting of intermediate payloads. It is suspected that “the C2 server only responds to certain types of requests at certain times”, thus making attacks more evasive.
“The threat actor made additional efforts to remain undetected by evading memory forensics and automated URL scanning solutions,” the researchers said.