
Cybersecurity researchers have discovered a new Linux variant of a remote access trojan (RAT) called BIFROSE (also known as Bifrost) that uses a deceptive domain that mimics VMware.
“This latest version of Bifrost aims to bypass security measures and compromise targeted systems,” said Palo Alto Networks Unit 42 researchers Anmol Maurya and Siddharth Sharma.
BIFROSE is one of the long-standing threats that has been active since 2004. It was previously offered for sale in underground forums for up to $10,000, according to a December 2015 Trend Micro report.
The malware was used by a state-backed Chinese hacking group identified as BlackTech (also known as Circuit Panda, HUAPI, Manga Taurus, Palmerworm, PLEAD, Red Djinn, and Temp.Overboard), which has a history of attacking organizations in Japan, Taiwan and the United States

The threat actor is suspected to have purchased the source code or gained access to it around 2010 and repurposed the malware for use in their own campaigns via custom backdoors such as KIVARS and XBOW.
Linux variants of BIFROSE (aka ELF_BIFROSE) have been observed since at least 2020 with the ability to launch remote shells, download/upload files, and perform file operations.
“Attackers typically distribute Bifrost via email attachments or malicious websites,” the researchers said. “Once installed on the victim’s computer, Bifrost allows the attacker to collect sensitive information, such as the victim’s hostname and IP address.”
What makes the latest variant noteworthy is that it reaches a command and control (C2) server with the name “download.vmfare[.]com” in an attempt to masquerade as VMware. The deceptive domain is resolved by contacting a public DNS resolver based in Taiwan with the IP address 168.95.1[.]1.
Unit 42 claimed to have detected a spike in Bifrost activity since October 2023, identifying no fewer than 104 artefacts in its telemetry. It also discovered an Arm version of the malware, suggesting that threat actors are likely looking to expand their attack surface.

“With new variants employing deceptive dominance strategies such as typosquatting, a recent spike in Bifrost activity highlights the dangerous nature of this malware,” the researchers said.
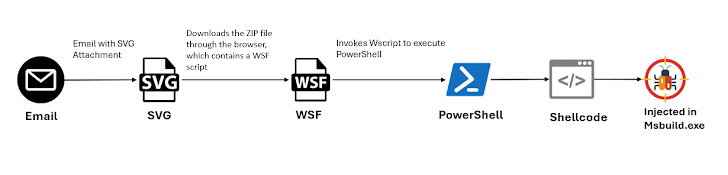
The development comes as McAfee Labs details a new GuLoader campaign that propagates malware through malicious SVG file attachments in email messages. The malware was also observed to be distributed via VBS scripts as part of a multi-stage payload distribution.

“This recent wave highlights its evolving tactics for wider reach and evasion,” Trustwave SpiderLabs She said in a post on X earlier this week.
The Bifrost and GuLoader attacks coincide with the publication of a new version of the Warzone RAT, of which two of its operators were recently arrested and its infrastructure dismantled by the US government.