
Facebook advertisers in Vietnam are the target of a previously unknown information thief nicknamed VietCredCare at least from August 2022.
The malware is “noteworthy for its ability to automatically filter Facebook session cookies and stolen credentials from compromised devices and to evaluate whether these accounts manage business profiles and whether they maintain a positive Meta advertising credit balance,” he said Group-IB based in Singapore. a new report shared with The Hacker News.
The ultimate goal of the large-scale malware distribution scheme is to facilitate the takeover of corporate Facebook accounts by targeting Vietnamese individuals who manage the Facebook profiles of major companies and organizations.
The successfully seized Facebook accounts are then used by the threat actors behind the operation to publish political content or to spread phishing and affiliate scams for profit.

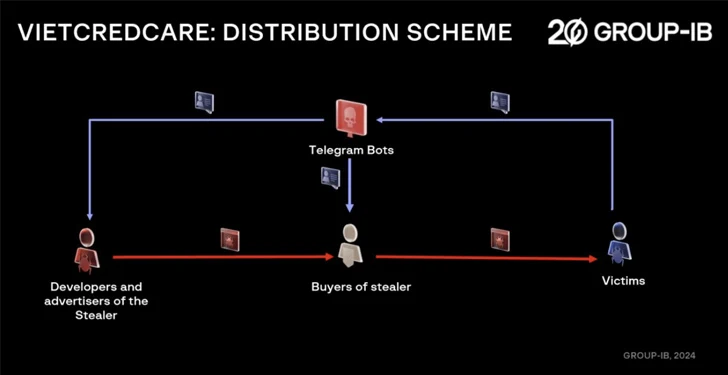
VietCredCare is offered to other would-be cybercriminals under the stealer-as-a-service model and advertised on Facebook, YouTube and Telegram. It is believed to be run by Vietnamese speaking people.
Customers have the option to purchase access to a botnet operated by the malware’s developers or obtain access to the source code for resale or personal use. A bespoke Telegram bot is also provided to handle the exfiltration and delivery of credentials from an infected device.
.NET-based malware is distributed via links to fake sites on social media posts and instant messaging platforms, masquerading as legitimate software such as Microsoft Office or Acrobat Reader to trick visitors into installing them.
One of its key selling points is its ability to extract credentials, cookies, and session IDs from web browsers such as Google Chrome, Microsoft Edge, and Cốc Cốc, indicating its Vietnamese focus.
It can also retrieve a victim’s IP address, check whether Facebook is a business profile, and assess whether the account in question is currently serving any advertisements, while simultaneously taking steps to evade detection by disabling the Windows malware scanning interface ( AMSI) and adding itself to the Windows Defender Antivirus exclusion list.
“VietCredCare’s core functionality to filter Facebook credentials puts organizations in both the public and private sectors at risk of reputational and financial damage if their sensitive accounts are compromised,” said Vesta Matveeva, head of the Crime Investigation Department high-tech for APAC.

Credentials belonging to several Vietnamese government agencies, universities, e-commerce platforms, banks, and companies were stolen via the thieving malware.
VietCredCare is also the latest addition to a long list of stealer malware, such as Ducktail and NodeStealer, originating from the Vietnamese cybercrime ecosystem with the intent to target Facebook accounts.
“The stealer-as-a-service business model allows threat actors with little or no technical expertise to enter the field of cybercrime, which results in more innocent victims being harmed,” Group-IB said .