
Some Ukrainian government networks have been infected with malware called OfflRouter since 2015.
Cisco Talos said its findings are based on the analysis of more than 100 confidential documents that were infected with the VBA macro virus and uploaded to the VirusTotal malware scanning platform.
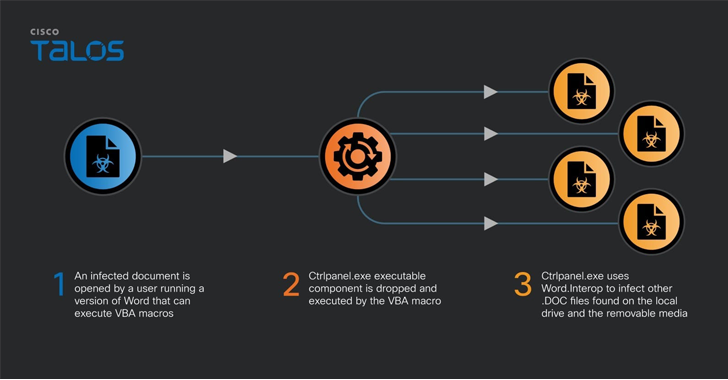
“The documents contained VBA code to release and run an executable with the name ‘ctrlpanel.exe,’” security researcher Vanja Svajcer said. “The virus is still active in Ukraine and is causing potentially sensitive documents to be uploaded to publicly accessible document archives.”
One surprising aspect of OfflRouter is its inability to spread via email, making it necessary for it to be propagated through other means, such as sharing documents and removable media, including USB sticks containing the infected documents.
These design choices, whether intentional or not, are said to have limited OfflRouter’s spread within the borders of Ukraine and to a few organizations, thus escaping detection for nearly 10 years.

It is currently unknown who is responsible for the malware and there is no indication that it was developed by anyone from Ukraine.
Whoever he is, he has been described as inventive but inexperienced due to the unusual propagation mechanism and the presence of numerous errors in the source code.
OfflRouter was previously highlighted by MalwareHunterTeam as early as May 2018 and again by the Computer Security Incident Response Team Slovakia (CSIRT.SK) in August 2021, detailing infected documents uploaded to the Ukrainian National Police website.
The modus operandi has remained virtually unchanged, with Microsoft Word documents embedded in VBA macros that drop a .NET executable named “ctrlpanel.exe”, which then infects all files with the .DOC (not .DOCX) extension found on the system and other removable media with the same macro.
“The infection loops through a list of candidate documents to infect and uses an innovative method to check the document infection marker to avoid multiple infection processes: the function checks the document creation metadata, adds creation times, and checks the value of the sum,” Svajcer said.
“If the sum is zero, the document is considered already infected.”
That said, the attack is only successful when VBA macros are enabled. Microsoft, as of July 2022, blocks macros by default in Office documents downloaded from the Internet, prompting threat actors to look for other initial entry paths.
Another key function of the malware is to make changes to the Windows registry to ensure that the executable runs every time the system starts.
“The virus only targets documents with the .DOC extension, the default extension for OLE2 documents, and will not attempt to infect other file extensions,” Svajcer explained. “The default Word document file name extension for newer versions of Word is .DOCX, so few documents will be infected.”

It’s not all. Ctrlpanel.exe is also capable of searching for potential plugins (with .ORP extension) present on removable drives and executing them on the machine, which implies that the malware expects plugins to be delivered via USB drives or CD-ROMs.
Conversely, if the plugins are already present on a host, OfflRouter takes care of encoding them, copying the files to the root folder of the attached removable media with the .ORP file name extension, and manipulating them to make them hidden so that they are not visible via Explore files when you connect them to another device.
That said, one of the main unknowns is whether the initial vector is a document or the executable module ctrlpanel.exe.
“The advantage of the two-module virus is that it can be spread as a standalone executable or as an infected document,” Svajcer said.
“It may also be advantageous to initially spread it as an executable since the module can run standalone and set registry keys to allow running VBA code and changing default saved file formats to .DOC before infecting documents. This way, the infection could be a little more stealthy.”