
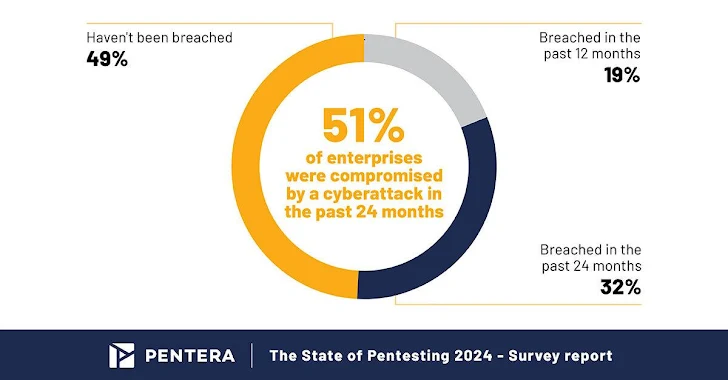
In the last two years, a shocking fact 51% of organizations surveyed in a major industry report have been compromised by a cyber attack. Yes, more than half.
And this, in a world where businesses are mobilizing an average of 53 different security solutions to safeguard your digital domain.
Alarming? Absolutely.
A recent survey of CISOs and CIOs, commissioned by Pentera and conducted by Global Surveyz Research, offers a quantifiable glimpse into this evolving battlefield, revealing a stark contrast between the growing risks and increasingly tight budget constraints under which professionals operate of information security.
With this report, Pentera has once again taken a magnifying glass on the state of pentesting to release its annual report on pentesting practices today. Involving 450 security executives from North America, LATAM, APAC and EMEA, all in VP or C level positions in organizations with more than 1,000 employees, the report paints a current picture of modern security validation practices across the enterprise.
Key findings include:
- The impact of a breach is high:
- 43% reported unplanned downtime
- 36% reported data exposure
- 31% reported financial losses
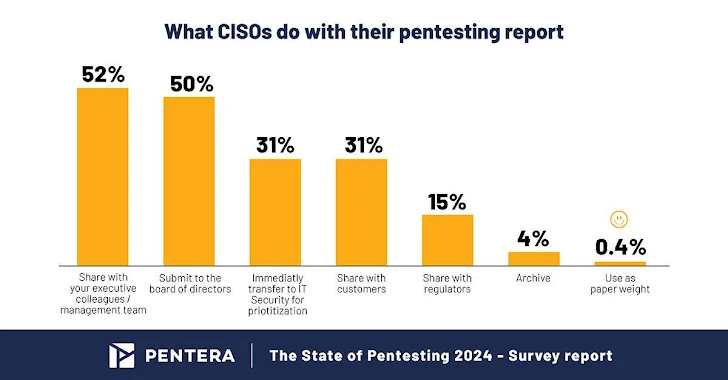
- As boards of directors (BoDs) become more aware of the cyber problem, over 50% of CISOs now share their pentesting reports with their boards.
- There is a notable gap between the rate of change in IT environments and the frequency of security testingleaving organizations’ digital assets untested for long periods of time.
- With an average of 500 repair events per week, Effective prioritization is one of the most important factors for security teams.

Security breaches persist despite investments
The 2024 report reveals that companies have an average of 53 security solutions, but struggle to maintain the Confidentiality, Integrity, Availability (CIA) trifecta. As part of security policies and practices, this triad protects information systems and data from various threats, ensuring that information is safe, reliable and accessible to the right people.
This reality is underlined by the fact that 51% of CISOs surveyed admitted to having suffered a cybersecurity breach in the past two years. These breaches led to significant operational disruptions, including unplanned downtime, data exposure and financial losses. Only 7% of companies avoided a substantial impact resulting from a breach. These incidents demonstrate the importance of having strong cybersecurity defenses.
Companies have seen an almost even distribution of attacks across their IT infrastructure; including remote devices, on-premises and cloud environments, highlighting the need to regularly test and secure each of these domains. The cloud’s increased profile as an attack target is consistent with other industry reports. Crowdstrike’s Global Threat Report for 2024 reported a 75% increase in cloud intrusions year-over-year. They predicted that in the coming years, as more organizations progress with their cloud migration efforts and move toward predominantly cloud or cloud-native deployments, this figure will increase.
Greater involvement of executives and the board of directors
In light of high-profile breaches making headlines, there is a notable increase in senior management oversight of cybersecurity. Over half of CISOs now regularly report pentest results to their boards, highlighting the strategic importance of cybersecurity for the enterprise. CISOs are increasingly using pentest reports as a way to better communicate cybersecurity risks to their executive teams and boards.
Furthermore, 31% of CISOs share pentest results with customers, recognizing the importance of transparency in managing third-party and supply chain risks. Adopting this practice not only builds trust, but also promotes a culture of openness about cybersecurity challenges and measures.
Bridging the Pentesting Gap
The survey highlights a disconcerting gap between the frequency of IT environment changes and the cadence of security testing. While 73% of organizations report making IT changes quarterly, only 40% maintain this pace with their pentesting efforts. This leaves organizations exposed to risk for prolonged periods.
On averagebusinesses dedicate $164,400 to manual pentesting, representing 12.9% of their annual IT security budget. With 60% of organizations pentesting a maximum of twice a year, this is a large investment and a sizable portion of the budget for a security activity that provides only an instant assessment of security posture. Given the importance of pentesting in improving IT resilience, it is worth considering solutions that provide continuous and scalable pentesting.

The perfect patch is not realistic
In addition to remediation tasks, security teams are tasked with a diverse set of responsibilities that push them to the limit.
In this context, companies are inundated with security-related events. With over 60% of companies reporting receiving at least 500 incidents requiring resolution each week, Patch perfection has never been more elusive. It is increasingly clear that the art of prioritization is an art that security teams will need to learn to keep their organization well protected. Security teams that can effectively understand the context of a vulnerability, its compensating controls, and the data it leads to will be the ones that stay in the game.
What do these results mean?
The 2024 State of Pentesting survey, conducted by Pentera, highlights a critical moment for cybersecurity: As threats continue to evolve, many security solutions are failing to mitigate them, requiring CISOs to more consistently validate the security of their infrastructure.
The results of this survey aren’t just statistics: they’re a call to action for better, more efficient cybersecurity practices that align with the financial and operational realities of our time.
Discover key findings from the 2024 State of Pentesting survey in this webinar. Join us as we explore the findings, discuss strategies for managing cybersecurity, prioritize tasks, and learn how to communicate your security posture to leadership more effectively.
Download the State of Pentesting 2024 Survey OR register here to participate in the live webinar.