
US cybersecurity and intelligence agencies have warned The Phobos ransomware attacks against government entities and critical infrastructure, outlining the various tactics and techniques that threat actors have adopted to distribute file-encrypting malware.
“Structured as a ransomware as a service (RaaS) model, Phobos ransomware authors have targeted entities including municipal and county governments, emergency services, education, public health, and critical infrastructure to successfully ransom several millions of dollars USA,” the government said.
The alert comes from the US Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC).
Active since May 2019, several variants of the Phobos ransomware have been identified to date: Eking, Eight, Elbie, Devos, Faust and Backmydata. Late last year, Cisco Talos revealed that the threat actors behind the 8Base ransomware are leveraging a variant of the Phobos ransomware to conduct their financially motivated attacks.
There is evidence to suggest that Phobos is likely closely managed by a central authority, which controls the ransomware’s private decryption key.
Attack chains involving the ransomware strain have typically leveraged phishing as the initial entry vector to deliver stealthy payloads such as SmokeLoader. Alternatively, vulnerable networks are breached by searching for exposed RDP services and exploiting them via a brute force attack.

A successful digital break-in is followed by threat actors abandoning additional remote access tools, leveraging process injection techniques to execute malicious code and evade detection, and making changes to the Windows registry to maintain persistence within environments compromises.
“Furthermore, Phobos authors have been observed using built-in Windows API functions to steal tokens, bypass access controls, and create new processes to escalate privileges by leveraging the SeDebugPrivilege process,” the agencies said. “Phobos authors attempt to authenticate using cached password hashes on victim computers until they gain domain administrator access.”
The e-crime group is also known to use open source tools such as Bloodhound and Sharphound to enumerate the active directory. File exfiltration is performed via WinSCP and Mega.io, after which volume shadow copies are deleted in an attempt to make recovery more difficult.
The disclosure comes as Bitdefender details a meticulously coordinated ransomware attack that hit two separate companies simultaneously. The attack, described as synchronized and multifaceted, was attributed to a ransomware actor called CACTUS.
“CACTUS continued to infiltrate an organization’s network, planting various types of remote access tools and tunnels on different servers,” said Martin Zugec, director of technical solutions at Bitdefender, in a report published last week.
“When they identified an opportunity to move to another company, they temporarily suspended their operations to infiltrate the other network. Both companies are part of the same group, but operate independently, maintaining separate networks and domains without any relationship of trust established.”
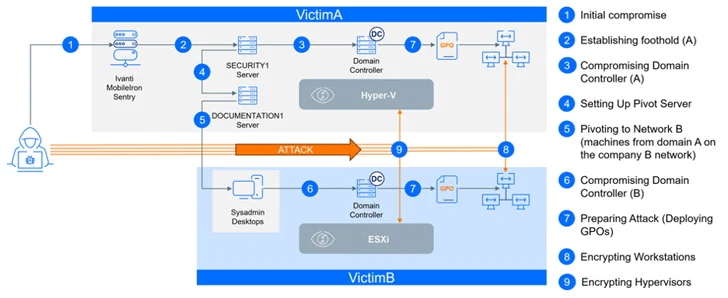
The attack is also notable for targeting the unnamed company’s virtualization infrastructure, indicating that CACTUS actors have expanded their focus beyond Windows hosts to target Hyper-V and VMware ESXi hosts.
It also exploited a critical security flaw (CVE-2023-38035, CVSS score: 9.8) in an Ivanti Sentry server exposed to the Internet less than 24 hours after its initial disclosure in August 2023, once again highlighting the opportunistic and rapid use of newly published vulnerabilities. .

Ransomware continues to be a major source of revenue for financially motivated threat actors, with initial ransomware demands reaching an average of $600,000 in 2023, a 20% increase from the previous year, according to Arctic Wolf. As of the fourth quarter of 2023, the average ransom payment was $568,705 per victim.
Furthermore, paying a ransom demand is not the same as future protection. There is no guarantee that a victim’s data and systems will be safely recovered, and that attackers will not sell the stolen data on underground forums or attack them again.
Data shared by cybersecurity firm Cybereason shows that “a staggering 78% [of organizations] were attacked again after paying the ransom – 82% of them within a year,” in some cases by the same threat actor. Of these victims, 63% were “asked to pay more a second time.”