
Maintainers of the Python Package Index (PyPI) repository briefly suspended new user signups following an influx of malicious projects uploaded as part of a typosquatting campaign.
It said that “the creation of new projects and the registration of new users” had been temporarily suspended to mitigate what it said was a “malware loading campaign.” The incident was resolved 10 hours later, on March 28, 2024, at 12:56 UTC.
Software supply chain security firm Checkmarx said the unidentified threat actors behind the repository flooding targeted developers with typosquat versions of popular packages.
“This is a multi-stage attack and the malicious payload aims to steal crypto wallets, sensitive data from browsers (cookies, extension data, etc.) and various credentials,” said researchers Yehuda Gelb, Jossef Harush Kadouri and Tzachi Zornstain. “Additionally, the malicious payload used a persistence mechanism to survive reboots.”
The findings were also independently confirmed by Mend.io, which noted that it had detected more than 100 malicious packages targeting machine learning (ML) libraries such as Pytorch, Matplotlib, and Selenium.

The development comes at a time when open source repositories are increasingly becoming an attack vector for threat actors to infiltrate enterprise environments.
Typosquatting is a well-documented attack technique in which adversaries load packages with names that closely resemble their legitimate counterparts (e.g., Matplotlib vs. Food plot or tensorflow vs. tensile flow) to trick unsuspecting users into downloading them.
These deceptive variants, totaling over 500 packages for Check Point, were discovered to have been uploaded from a unique account starting on March 26, 2024, suggesting that the entire process was automated.
“The decentralized nature of the uploads, in which each package is attributed to a different user, complicates efforts to cross-identify these malicious entries,” the Israeli cybersecurity firm said.
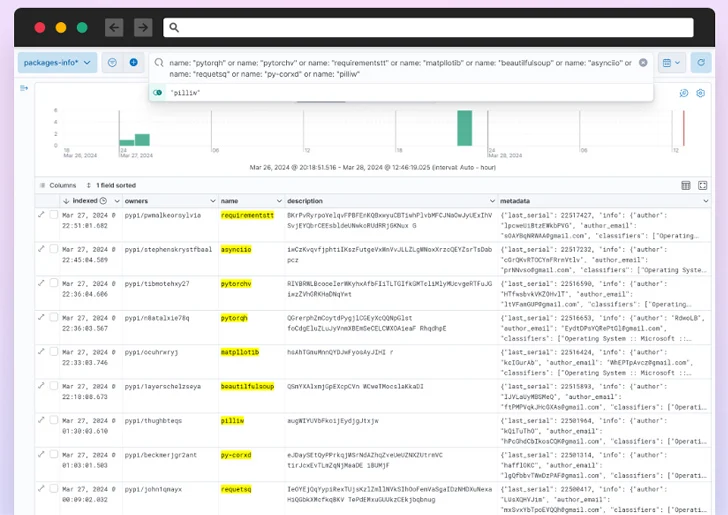
Cybersecurity firm Phylum, which followed the same campaign, said the attackers posted:
- 67 changes in requirements
- 38 Matplotlib variants
- 36 variations of requests
- 35 colorama variations
- 29 tensorflow variations
- 28 variations of selenium
- 26 variations of BeautifulSoup
- 26 PyTorch variants
- 20 cushion variations
- 15 variations of asyncio
The packages, for their part, check whether the installer’s operating system was Windows and, if so, proceed to download and execute an obfuscated payload retrieved from an actor-controlled domain (“funcaptcha[.]ru”).

The malware works like a thief, exfiltrating files, Discord tokens, and data from web browsers and cryptocurrency wallets on the same server. It also attempts to download a Python script (“hvnc.py”) to the Windows Startup folder for persistence.
The development once again illustrates the growing risk posed by software supply chain attacks, making it vital that developers carefully review each third-party component to ensure it protects against potential threats.
This is not the first time PyPI has resorted to such a measure. In May 2023, it temporarily disabled user registrations after discovering that “the volume of malicious users and malicious projects created on the index over the past week exceeded our ability to respond in a timely manner.”
PyPI suspended new user registration for a second time last year, on December 27, for similar reasons. It was later revoked on January 2, 2024.