
The data deletion malware called AcidPour may have been used in attacks against four telecom operators in Ukraine, new findings from SentinelOne show.
The cybersecurity firm also confirmed links between the malware and AcidRain, linking it to clusters of threat activity associated with Russian military intelligence.
“AcidPour’s expanded capabilities would allow it to better disable embedded devices including networks, IoT, large storage devices (RAID), and possibly ICS devices running x86 Linux distributions,” said security researchers Juan Andres Guerrero- Saade and Tom Hegel.
AcidPour is a variant of AcidRain, a wiper used to operationalize Viasat KA-SAT modems at the start of the Russian-Ukrainian war in early 2022 and cripple Ukraine’s military communications.

It also builds on the capabilities of the latter, targeting Linux systems running on x86 architecture. AcidRain, on the other hand, is compiled for the MIPS architecture.
Where AcidRain was more generic, AcidPour incorporates logic to target embedded devices, Storage Area Networks (SANs), Network Associated Storage (NAS) devices, and dedicated RAID arrays.
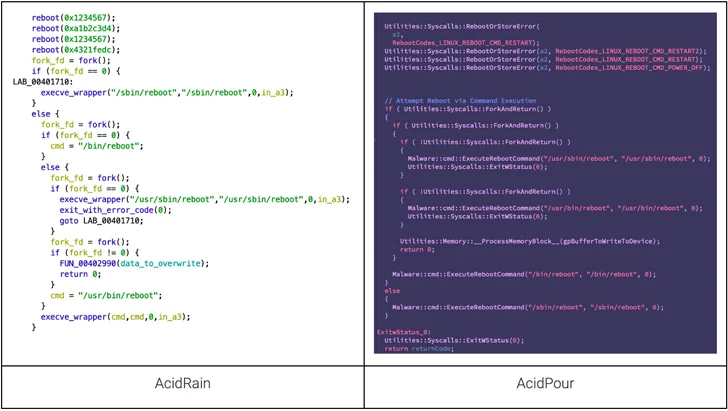
That said, both tensions overlap when it comes to the use of restart calls and the method used for recursively deleting directories. The IOCTL-based device wipe mechanism is also identical and also shares commonalities with another Sandworm-related malware known as VPNFilter.
“One of the most interesting aspects of AcidPour is its coding style, which is reminiscent of the pragmatic CaddyWiper widely used against Ukrainian targets along with major malware such as Industroyer 2,” the researchers said.
The C-based malware has a self-delete function that overwrites itself on disk at the start of its execution, also employing an alternative wipe approach depending on the device type.
AcidPour was attributed to a hacking team identified as UAC-0165, which is associated with Sandworm and has a history of attacking Ukrainian critical infrastructure.
The Computer Emergency Response Team of Ukraine (CERT-UA), in October 2023, implicated the adversary in attacks against at least 11 telecom service providers in the country between May and September last year.

“[AcidPour] could have been used in 2023,” Hegel told The Hacker News. “It is likely that the actor used the AcidRain/AcidPour-related tools consistently throughout the war. A gap in this perspective indicates the level of understanding the public often has regarding cyber intrusions is generally quite limited and incomplete.”
The ties to Sandworm are further strengthened by the fact that an actor known as Solntsepek (aka Solntsepek or SolntsepekZ) claimed to have infiltrated four different telecom operators in Ukraine and disrupted their services on March 13, 2024, three days before the discovery of AcidPour.
Solntsepyok, according to the State Special Communications Service of Ukraine (SSSCIP), is a Russian advanced persistent threat (APT) with probable links to the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), which also operates Verme of the sand.
It is worth pointing out that Solntsepyok was also accused of hacking into Kyivstar’s systems as early as May 2023. The breach came to light in late December.
While it is currently unclear whether AcidPour was used in the latest round of attacks, the finding suggests that threat actors are constantly refining their tactics to mount destructive attacks and inflict significant operational impact.
“This progression reveals not only a refinement of the technical capabilities of these threat actors, but also their calculated approach to selecting targets that maximize aftereffects by disrupting critical infrastructure and communications,” the researchers said.