QR code-based email attacks have increased in the last quarter, with attackers specifically targeting corporate executives and managers, reinforcing recommendations that companies place additional digital protections around their corporate leadership.
To make matters worse, phishing emails using QR codes (also known as “quishing”) can often get past spam filters, with attacks targeting Microsoft 365 and DocuSign users successfully landing in email inboxes, according to a report released this week by Abnormal Security, a cloud email security provider.
In the fourth quarter of 2023, the average C-suite top executive experienced 42 times more phishing attacks using QR codes than the average employee. Other management roles also experienced an increase in attacks, although significantly less, with these non-C-level executives experiencing five times more QR code-based phishing attacks, according to the company’s report.
Overall, the data shows that attackers have executives – and other privileged users – on their sites, says Mike Britton, CISO at Abnormal Security.
“If I’m an attacker, I want to attack people who have the ability to charge me and have credentials that give me access to the most interesting information,” he says. “Or do I want to pretend to be those people, because again, social engineering requires that trust, [for a victim to think,] hey, this VP of Sales or this VP of HR is asking me to do something, [making them] they are generally more likely…to act.”
Although QR codes have been around for three decades, they have become much more popular during the pandemic, as restaurants and other businesses have turned customers to online, contactless ordering. In a business context, one of the primary use cases for QR codes is offering links to facilitate the registration process for multi-factor authentication (MFA). Attackers succeeded: More than a quarter of QR code attacks (27%) in the fourth quarter were false MFA notifications, for example, while about one in five attacks (21%) were false notifications related to a shared document, according to Abnormal Security report.
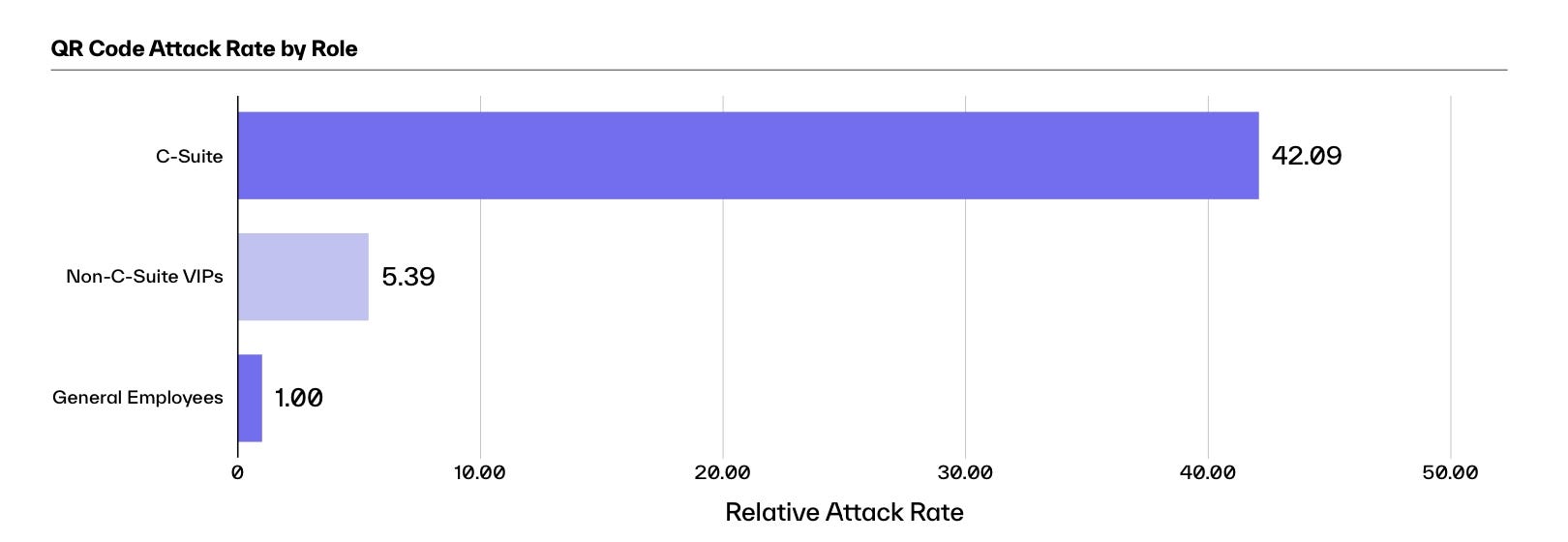
Senior executives suffer 42 times more QR code attacks than regular employees. Source: Anomalous Security
Because attackers hide the phishing link in an image, QR code phishing bypasses user suspicions and some email security products. Additionally, malicious QR codes can be placed in physical spaces using a simple sticker, bypassing digital security altogether.
“Attacks exploit users’ inherent trust in QR codes, embedding them in everyday objects such as parking meters or posters,” says Monique Becenti, director of product at mobile security firm Zimperium. “The success rate of phishing with QR codes will surpass traditional phishing methods because they often bypass typical user suspicion factors, such as typos in the URL, leading to a higher likelihood of scanning them.”
Yet another way to steal executive credentials
In most cases, attackers targeting executives seek the credentials – usernames and passwords – of privileged users. Credential phishing is the most popular form of email attack, accounting for 73% of all vector attacks and 84% of attacks using a QR code; and often lead to more significant compromises, says Abnormal Security’s Britton.
“The main goal is to convince a user to steal their credentials,” he says. “Once I have your credentials, I can do a lot more damage, and I can cause a lot of lasting damage. If I have your credentials, I can access your account, I can see who you’ve sent emails to, I can I can send emails pretending to be you and I can create mail filtering rules.”
This last point is a common way to abuse email credentials, Britton says. The attacker will create a blind carbon copy (BCC) rule that will forward all emails to the attacker’s account.
Additionally, “threat actors also recognize that multiple people often have access to an executive’s inbox, such as executive assistants,” the report states. “As a result, any individual who knows a VIP’s inbox login credentials represents a potential entry point that can be exploited by an attacker.”
To counter Quishing, technology and human training are needed
The good news is that QR code phishing has eased significantly since October, after accounting for 22% of phishing attacks. according to human risk management company Hoxhunt. “Since last October, we’ve seen evidence that email filters are catching up to the QR phishing technique,” says Jon Gellin, threat team lead at Hoxhunt. “Because fewer of these attacks are able to bypass email filters, there has been a subsequent decline in their popularity.”
However, even if quishing fades, it will remain a tool for attackers, just as shortened URLs and image spam continue to be used in cyberattacks. The best way to protect users is to train them, Gellin says. About 5% of users respond to a phishing attack within the first few minutes, suggesting that a well-trained group of employees can help blunt an attack.
“As the QR phishing trend has shown, some threats always manage to get past even the most sophisticated filters,” he says. “At that point, it is up to the human level to possess the skills and tools to address the threat effectively.”
Training is important, but because a single failure can have a significant impact, technical controls are needed, says Abnormal Security’s Britton.
“Well, there are some phishing attacks that I’ve seen that I have to ask people for a second opinion too because they seem so real,” he says. “How can I expect an HR person to do everything right every time? How can I expect an accounts payable person? How can I expect a financial analyst?”
“Training is important, but we will fail, and it only takes one failure,” he says.