
The menacing actor known as TA577 The use of ZIP archive attachments in phishing emails with the goal of stealing NT LAN Manager (NTLM) hashes has been observed.
The new attack chain “may be used for sensitive information collection purposes and to enable follow-on activities,” enterprise security firm Proofpoint said in a report on Monday.
At least two campaigns leveraging this approach were observed on February 26 and 27, 2024, the company added. Phishing waves have spread thousands of messages and targeted hundreds of organizations around the world.

The messages themselves appeared as replies to previous emails, a technique known as thread hijacking, in an attempt to increase the likelihood of successful attacks.
ZIP attachments come with an HTML file designed to contact a Server Message Block (SMB) server controlled by the actor.
“The goal of TA577 is to capture NTLMv2 Challenge/Response pairs from the SMB server to steal NTLM hashes based on the characteristics of the attack chain and tools used,” the company said, which could then be used for type pass -the-hash (PtH). attacks.
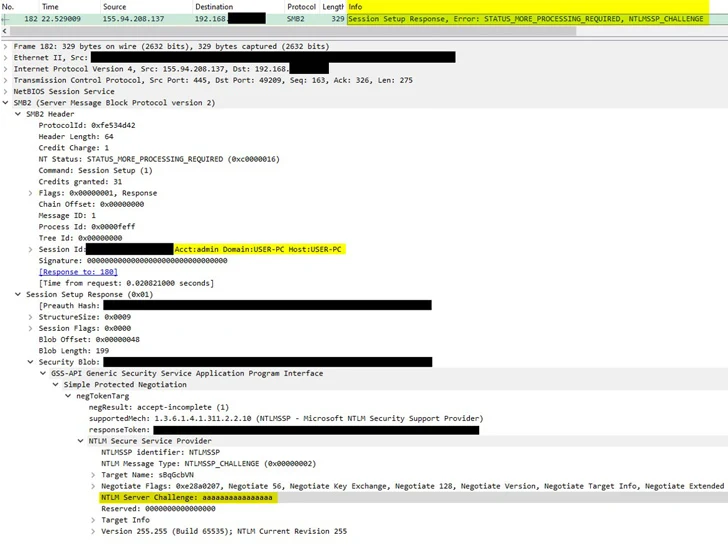
This means that hackers in possession of a password hash do not need the underlying password to authenticate a session, ultimately allowing them to move across a network and gain unauthorized access to valuable data.
TA577, which overlaps with an activity cluster monitored by Trend Micro such as Water Curupira, is one of the most sophisticated cybercrime groups. It has been linked to the distribution of malware families such as QakBot and PikaBot in the past.

“The speed with which TA577 adopts and deploys new tactics, techniques and procedures (TTPs) suggests that the threat actor likely has the time, resources and experience to rapidly iterate and test new deployment methods,” Proofpoint said .
It further described the threat actor as acutely aware of changes in the cyber threat landscape, rapidly adapting and refining its business techniques and delivery methods to evade detection and eliminate a variety of payloads. Organizations are strongly advised to block outbound SMEs to prevent exploitation.