
Mexican users have been targeted with tax-themed phishing lures since at least November 2023 to distribute previously undocumented Windows malware called TimbreStealer.
Cisco Talos, which discovered the activity, described the perpetrators as skilled and that “the threat actor previously used similar tactics, techniques and procedures (TTPs) to deploy a banking Trojan known as Mispadu in September 2023.
In addition to employing sophisticated obfuscation techniques to evade detection and ensure persistence, the phishing campaign uses geofencing to target users in Mexico, returning a harmless blank PDF file instead of the malicious one if the payload sites are contacted from other locations .
Some of the more notable evasive maneuvers include leveraging custom loaders and direct system calls to bypass conventional API monitoring, as well as using Heaven’s Gate to execute 64-bit code inside a 32-bit process, an approach recently also adopted by HijackLoader.

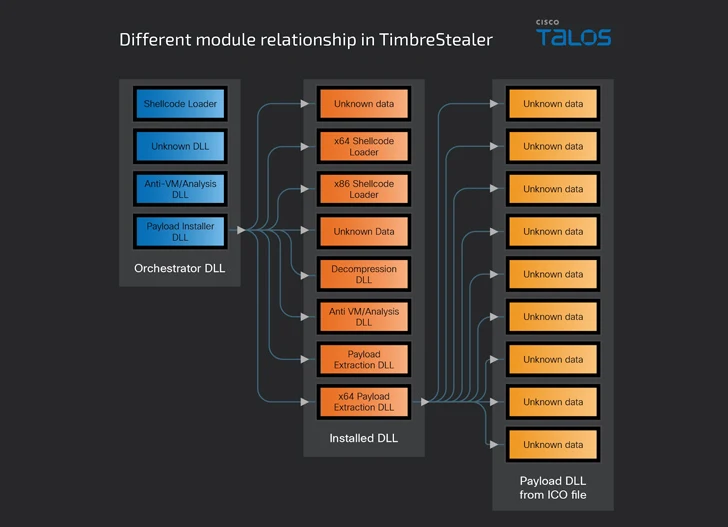
The malware comes with several built-in modules for orchestration, decryption and protection of the main binary file, also performing a series of checks to determine if it is running a sandbox environment, the system language is not Russian and the time zone it is within a Latin American. region.
The orchestrator module also searches for files and registry keys to double-check that the machine has not been previously infected, before launching a payload installation component that displays a benign decoy file to the user, as it ultimately triggers the execution of the primary payload by TimbreStealer.
The payload is designed to collect a wide range of data, including credential information from different folders, system metadata and URLs accessed, search for files matching specific extensions, and check for remote desktop software.
Cisco Talos said it identified overlaps with a Mispadu spam campaign observed in September 2023, although TimbreStealer’s target industries are varied and focused on the manufacturing and transportation sectors.
The disclosure comes as a new version of another information thief called Atomic (also known as AMOS) emerges, which is capable of harvesting data from Apple macOS systems such as local user account passwords, credentials from Mozilla Firefox and browsers based on Chromium, crypto wallet. information and files of interest, using an unusual combination of Python code and Apple Script.

“The new variant is released and uses a Python script to stay hidden,” Bitdefender researcher Andrei Lapusneanu said, noting that the Apple Script blocker for collecting sensitive files from the victim’s computer shows a “significantly high level of similarity” with the RustDoor backdoor.

This also follows the emergence of new families of stealer malware such as XSSLite, which was released as part of a malware development competition hosted by the XSS forum, although existing strains such as Agent Tesla and Pony (aka Fareit or Siplog) have continued to be used for information theft and subsequent sale on thieves’ log marketplaces such as Exodus.